Advanced cyberattacks are evolving, and traditional security measures are struggling to keep pace. Threats no longer operate in silos; they move laterally across systems, exploiting gaps between endpoints, networks, identity platforms, and the cloud. This is where Extended Detection and Response (XDR) steps in, revolutionizing how organizations detect, correlate, and respond to cyber threats.
This article unpacks how XDR works, its key features, and why it outperforms traditional detection solutions.
What is Extended Detection and Response (XDR)?
XDR, or Extended Detection and Response, is a cybersecurity approach that unifies threat detection and response across traditionally siloed domains—endpoints, networks, cloud infrastructure, identity systems, and email. Unlike tools like EDR or SIEM, which focus on specific areas, XDR integrates and correlates telemetry across the entire IT ecosystem.
Unlike siloed tools like EDR or SIEM, XDR provides a centralized platform that correlates security telemetry, automates incident response, and enhances visibility across your IT environment.
Key Characteristics of XDR:
- Integrated Telemetry: Combines data from various sources (e.g., endpoints, firewalls, and email logs) into a unified view.
- Contextual Detection: Correlates events across domains to identify sophisticated attack patterns.
- Automated Response: Executes predefined actions (e.g., quarantining endpoints, revoking cloud credentials) to contain threats quickly.
- Scalability and Cloud-Native Design: Many modern XDR platforms are built to operate natively in cloud or hybrid environments, scaling with organizational growth.
XDR doesn’t just collect data; it transforms fragmented alerts into actionable insights, enabling security teams to focus on what matters most.
How XDR Works
The power of XDR lies in its ability to consolidate, analyze, and act on telemetry data. Here’s a closer look at how the system functions:
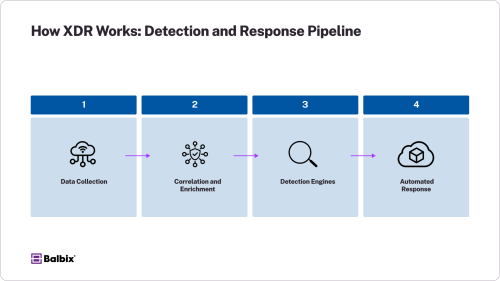
1. Cross-Domain Data Collection
XDR continuously ingests telemetry from multiple sources, including:
- Endpoint Detection and Response (EDR): Tracks process behavior, file system activity, and more.
- Network Detection and Response (NDR): Monitors flow data, anomalies, and packet captures.
- Identity and Access Management (IAM): Collects identity-related events like user logins and suspicious authentication attempts.
- Cloud and Email Services: Logs access events, email flows, and potential misconfiguration.
2. Data Correlation and Normalization
To make sense of raw telemetry, XDR analyzes and enriches data:
- Event Stitching: Combines disparate alerts into a narrative of attacker behavior.
- Threat Intelligence Integration: This process maps activity to frameworks like MITRE ATT&CK or enriches it with IOC (Indicators of Compromise) intelligence.
- Behavioral Analysis: Models baseline activity across users, devices, and networks to identify anomalies.
3. Advanced Threat Detection
XDR employs multiple detection methods in parallel:
- Signature-Based Detection: Matches known attack patterns like malicious hashes or domains.
- Behavioral Analytics: Detects unusual patterns, such as lateral movement or privilege escalation.
- Kill Chain and TTP Mapping: XDR platforms may model threats based on the attack lifecycle (e.g., reconnaissance to exfiltration) and map activity to known tactics, techniques, and procedures (TTPs) using frameworks like MITRE ATT&CK.
4. Automated and Orchestrated Response
Once threats are detected, XDR can automatically respond through built-in playbooks:
- Endpoints: Isolate compromised hosts, terminate suspicious processes, or disable network connections.
- Network: Block malicious IPs/domains or restrict east-west traffic.
- Cloud: Revoke access tokens or enforce stricter IAM policies.
- Email: Quarantine malicious messages and remove phishing threats from inboxes.
Key Features and Benefits of XDR
For cybersecurity teams, XDR offers significant improvements in efficiency, detection, and response:
Unified Visibility Across Attack Surfaces
XDR consolidates telemetry from endpoints, networks, cloud services, identity systems, and email platforms into a centralized view. This unified visibility allows security teams to see the full scope of an attack, trace its path across systems, and eliminate blind spots that siloed tools often miss.
Improved Threat Detection Fidelity
XDR can detect sophisticated, multi-stage attacks that evade traditional tools by analyzing events across multiple domains. For example, it can correlate lateral movement in the network with suspicious user behavior and endpoint anomalies, providing deeper context and reducing false positives.
Faster Detection and Response
XDR platforms often include automated response capabilities and prebuilt playbooks, allowing security teams to contain threats, such as isolating endpoints, revoking access tokens, or blocking malicious IP addresses, within minutes. This rapid response capability helps reduce Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Reduced Alert Fatigue
XDR dramatically reduces the volume of redundant or low-priority alerts by stitching together related events and prioritizing them based on severity and context. Analysts are presented with clear, high-fidelity incidents rather than being overwhelmed by thousands of fragmented alerts.
Enhanced SOC Efficiency
With fewer manual investigations and less time spent on repetitive tasks, SOC teams can focus on proactive threat hunting, incident analysis, and strategy. XDR not only improves day-to-day efficiency but also helps teams scale operations without a proportional increase in headcount.
XDR vs. Traditional Detection Architectures
Here’s how XDR compares to other detection solutions like EDR, NDR, and SIEM:
| Feature | EDR/NDR | SIEM | XDR |
| Detection Scope | Single domain | Aggregated logs | Cross-layer integration |
| Correlation | Limited | Manual | Automated and AI-driven |
| Alert Volume | High | Very high | Tuned and prioritized |
| Response Orchestration | Endpoints or network | Manual playbooks | Fully integrated response |
SIEMs focus on data aggregation and compliance reporting, often requiring manual correlation and tuning. EDR/NDR tools specialize in specific domains. XDR enhances these by automating real-time correlation and response across all domains.
Read more about EDR (Endpoint Detection and Response) and SIEM (Security Information Event Management).
Considerations Before Implementing XDR
Before deploying an XDR solution, evaluating how well it fits into your security ecosystem and future operational goals is important. Key considerations include:
Integration with Existing Tools
Ensure your XDR platform can ingest telemetry from your current security stack. Look for robust APIs and out-of-the-box connectors for EDR, firewalls, cloud providers, and identity services.
Identity Signal Coverage
Instead of relying on traditional Identity and Access Management (IAM) systems, XDR platforms typically ingest identity-related telemetry from sources like SSO/MFA providers (e.g., Okta, Azure AD) or Identity Threat Detection and Response (ITDR) tools. These signals include authentication attempts, access patterns, and anomalous behavior tied to user identities.
Detection Customization
Look for platforms that allow custom detection logic—whether through rules, machine learning tuning, or support for detection-as-code frameworks like Sigma. Flexibility in detection engineering can be crucial for defending against organization-specific threats.
Data Retention and Latency
Understand how long telemetry is stored and how quickly it can be processed for real-time detection. Low-latency processing is key for time-sensitive threats, while longer retention supports threat hunting and compliance.
Open vs. Closed XDR Architectures
Be aware of the difference between open and closed XDR platforms. Open XDR supports third-party integrations and offers flexibility across your tooling ecosystem. Closed XDR is typically vendor-specific, with tight integration across a proprietary stack. It is often faster to deploy, but it is potentially limiting if you need cross-vendor interoperability.
Choosing the right XDR platform means balancing immediate detection and response needs with long-term adaptability. Carefully evaluating these factors ensures your investment supports current threats and future scalability.
Frequently Asked Questions
- What is Extended Detection and Response (XDR)?
-
Extended Detection and Response (XDR) is an integrated cybersecurity solution that collects and correlates data from multiple sources like endpoints, networks, identity platforms, and the cloud. It enhances threat detection and automates responses to improve security efficiency.
- How does XDR work?
-
XDR ingests telemetry from diverse security layers, normalizes the data, and applies advanced analytics, threat intelligence, and behavioral models to detect threats. It automates responses, such as isolating endpoints or blocking domains, to minimize attack impact.
- What are the benefits of XDR?
-
XDR provides unified visibility, improved threat detection fidelity, faster response times, and reduced alert fatigue. It also enhances overall SOC efficiency by correlating alerts across domains and automating repetitive tasks.
- How is XDR different from EDR and SIEM?
-
XDR integrates data across multiple domains, unlike EDR, which focuses on endpoints, or SIEM, which aggregates logs without automated correlation. XDR automates detection and response while reducing alert noise for more efficient threat management.
- Who should adopt XDR?
-
Organizations seeking to improve threat visibility and response across complex environments, reduce alert fatigue, and streamline SOC operations should consider XDR. It’s especially valuable for businesses managing endpoint, network, cloud, and identity security.


