What Is Unified Threat Management (UTM)?
Unified Threat Management (UTM) is a consolidated cybersecurity solution that integrates multiple security functions into a single hardware or software appliance. UTM platforms centralize core capabilities—such as firewalls, intrusion prevention, antivirus, content filtering, and more—under a unified management console. This architecture streamlines network protection and policy enforcement, particularly for small and midsize businesses (SMBs) with limited security staff or tooling integration capabilities.
Core Components of UTM
Let’s dive into several core components of a Unified Threat Management solution:
Stateful Inspection Firewall
It performs Layer 3/4 packet filtering based on state tables, enabling the enforcement of security policies across IP addresses, ports, and protocols. Some UTMs also support Layer 7 filtering and application awareness.
Intrusion Detection and Prevention System (IDPS)
Monitors network traffic for known attack patterns and behavioral anomalies. Integrated IDPS engines often use signature-based detection combined with heuristic or behavioral analysis to prevent zero-day exploits and lateral movement.
Antivirus and Antimalware
UTMs integrate endpoint and gateway-level malware detection, leveraging signature-based scanning, hash-based comparisons, and heuristic engines to block file-based malware, ransomware, worms, and trojans.
Virtual Private Network (VPN)
Most UTM solutions support IPsec and SSL VPNs to facilitate encrypted remote access. VPN support includes site-to-site and client-to-site tunneling, allowing secure connections across distributed environments.
Web and Content Filtering
Enforces browsing restrictions based on URL categories, DNS filtering, and domain reputation databases. This protects users from accessing malicious domains and reduces exposure to phishing or exploit kit sites.
Email and Spam Filtering
Uses content inspection, DNSBLs (DNS-based block lists), and SPF/DKIM verification to block inbound spam and phishing attempts. Some UTM solutions integrate directly with mail servers for inline inspection.
Data Loss Prevention (DLP)
Implements regex-based and fingerprinting-based detection of sensitive data (e.g., PII, PCI, PHI), leaving the organization. DLP rules can trigger alerts or block data exfiltration attempts over web, email, or file transfer protocols.
Application Control
Identifies and controls application usage via deep packet inspection (DPI). This includes policy enforcement for shadow IT, SaaS access, and unauthorized software communications.
Benefits of Unified Threat Management
- Centralized Security Orchestration: UTM platforms offer a single pane of glass for monitoring, configuration, and enforcement of network security policies, reducing management overhead and error-prone tool sprawl.
- Cost Consolidation: By replacing multiple point products (e.g., separate firewalls, AV gateways, content filters), UTMs reduce Capital and Operational costs. Licensing is typically bundled, reducing administrative friction.
- Enhanced Threat Correlation: Tightly integrated modules enable cross-functional threat intelligence sharing—for example, malware detection can trigger firewall blocking or DLP enforcement, reducing response latency.
- Regulatory Alignment: UTMs can generate audit logs and compliance reports and implement consistent security policies aligned with standards such as HIPAA, PCI DSS, and GDPR.
UTM vs. Next-Generation Firewall (NGFW)
Though UTM and NGFW appliances may appear similar, their strategic focus and architectural depth differ. Let’s review some of the key differences:
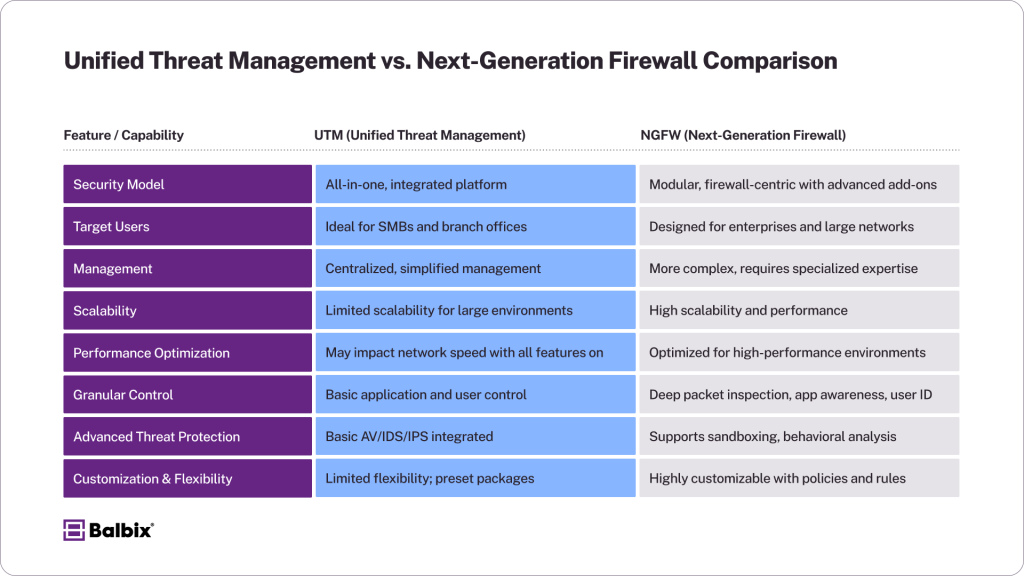
Key Considerations Before UTM Deployment
- Scalability: Ensure throughput and session limits match your network size and growth projections.
- Performance Benchmarks: Evaluate real-world traffic handling under full security feature loads (AV, DPI, VPN).
- Update Frequency: Confirm frequent signature updates, firmware patches, and zero-day protections.
- Interoperability: Validate integration with SIEM, EDR, Active Directory, and orchestration tools.
- Vendor Lock-In: Understand proprietary risks if migrating to a modular or best-of-breed stack later.
Conclusion
Unified Threat Management offers a pragmatic path to consolidating essential network defenses under a single management framework. While ideal for SMBs seeking operational simplicity and broad coverage, UTMs may lack the performance and customization required by enterprises with specialized security needs. For organizations that prioritize ease of use and centralized oversight over architectural flexibility, UTM remains a viable and often cost-effective cornerstone of perimeter defense.
Frequently Asked Questions
- What is Unified Threat Management (UTM) in cybersecurity?
-
Unified Threat Management (UTM) is a security solution that combines multiple network protection features, like firewall, antivirus, intrusion prevention, and VPN, into a single platform for simplified security management.
- How is UTM different from a Next-Generation Firewall (NGFW)?
-
UTMs offer broad security coverage in one appliance, which is ideal for SMBs. NGFWs focus on advanced firewall capabilities with granular application and traffic control, better suited for enterprises.
- What are the main features of a UTM appliance?
-
Core UTM features include a stateful firewall, intrusion detection and prevention (IDPS), antivirus, VPN support, content filtering, email protection, data loss prevention (DLP), and application control.
- Is UTM suitable for large enterprises?
-
While UTM is effective for small to midsize organizations, large enterprises may prefer NGFWs or modular solutions for higher performance, scalability, and customizable security architectures.
- What should organizations consider when choosing a UTM solution?
-
Key considerations include scalability, performance under full load, update frequency, integration with existing tools, vendor support, and total cost of ownership.


