Imagine having a centralized system that can collect and analyze massive amounts of security data in real time, detect advanced threats, and guide your response efforts efficiently. That’s precisely what SIEM (Security Information and Event Management) brings. This guide will help you understand what SIEM is, its key capabilities, and the value it offers for securing your IT environment.
What is SIEM?
At its core, SIEM is a technology that revolutionizes how organizations monitor and respond to cybersecurity threats. As the nerve center of security operations, SIEM platforms aggregate, analyze, and correlate security data from across the IT infrastructure. They provide real-time insights, alert systems, and automated responses essential for maintaining a secure environment.
Conceived initially to simplify compliance reporting and log management, SIEM solutions today have evolved. They now play a pivotal role in advanced threat detection and incident response strategies, ensuring enterprises can respond swiftly and effectively to even the most complex threats.
Why Does SIEM Matter?
Here’s why SIEM has become indispensable in cybersecurity:
- Proactive Threat Detection: SIEM systems detect patterns and anomalies that could indicate an attack.
- Enhanced Visibility: They centralize logs and data across your environment, offering security teams a complete picture.
- Compliance Made Easy: With automatic reports and audit logs, meeting regulatory requirements becomes less cumbersome.
- Incident Response Support: SIEM flags threats and equips IT teams with the necessary context to react decisively and reduce damage.
Key Functions of a SIEM System
To fully understand SIEM’s power, it’s essential to break down its core functions.
1. Data Collection
SIEM systems act as collectors, aggregating data from diverse sources, including:
- Servers and Endpoints: Operating system logs, application logs, and endpoint behavior.
- Firewalls and IDS/IPS: Data from firewalls and intrusion detection/prevention systems to monitor network threats.
- Cloud Applications: Insights from cloud platforms like AWS, Microsoft Azure, or Google Cloud.
- Identity and Access Management (IAM) Systems: User authentication and access control logs.
This vast data collection provides a bird’s-eye view of the organization’s IT landscape.
2. Data Aggregation and Correlation
Once collected, raw data is standardized and aggregated into a single source of truth. Then, SIEM tools apply correlation rules and behavioral analytics to identify patterns that might suggest malicious activity.
For instance:
- Multiple failed login attempts within seconds.
- Unusual user behavior, such as accessing systems at odd hours.
- Logins from geographically distant locations in a short time.
3. Threat Detection and Alerting
SIEM continuously monitors activity and compares it against:
- Threat Intelligence Feeds: Real-time data about known vulnerabilities and cyberattack methodologies.
- Behavioral Baselines: AI-driven analysis of normal operational behavior.
When potential threats arise, the system generates alerts, ranked by severity, to prioritize critical issues.
4. Incident Investigation
When alerts are raised, SIEM systems simplify investigation by offering:
- Incident Timelines: Tracks how an event evolved.
- Event Correlation Dashboards: Visualize connections between critical events across your infrastructure.
This empowers security analysts to quickly determine an incident’s root cause, scope, and impact.
5. Compliance Reporting
Many organizations face regulatory hurdles like PCI DSS, GDPR, or HIPAA. SIEM helps streamline compliance by generating logs and reports aligned with regulatory needs, though full compliance typically involves additional validation.
6. Automated Response
Advanced SIEM systems integrate with Security Orchestration, Automation, and Response (SOAR) capabilities. Here’s what they can do:
SIEM systems can trigger actions like blocking IPs or quarantining devices to prevent further spread when integrated with SOAR tools or security infrastructure. Additionally, they can notify security teams in real time through email or SMS.
This reduces the manual burden on security teams and accelerates response times dramatically.
The Benefits of SIEM
Investing in a SIEM solution can be transformative for businesses. Here’s how:
1. Enhanced Threat Detection
With robust correlation features and threat intelligence, SIEM identifies advanced, multi-vector threats that individual security tools might miss.
2. Faster Incident Response
By consolidating data and providing actionable insights, SIEM reduces dwell time (when a threat exists before being addressed). This quick response minimizes potential damage.
3. Improved Compliance
Regulatory fines for poor IT security are skyrocketing. SIEM simplifies compliance reporting and minimizes the risk of non-compliance penalties.
4. Centralized Visibility
Modern IT environments span on-premise systems, cloud platforms, and remote endpoints. SIEM centralizes visibility, offering a unified space to monitor the entire security environment.
5. Operational Efficiency and Cost Savings
By automating threat detection, reporting, and investigation workflows, SIEM reduces the need for manual intervention. This saves time and lightens the load on overburdened IT teams.
Alternatives to SIEM
While SIEM (Security Information and Event Management) is a foundational tool in many security stacks, it’s not the only option available. Depending on your organization’s size, specific needs, and overall security maturity, other solutions can complement or even replace some of SIEM’s traditional use cases.
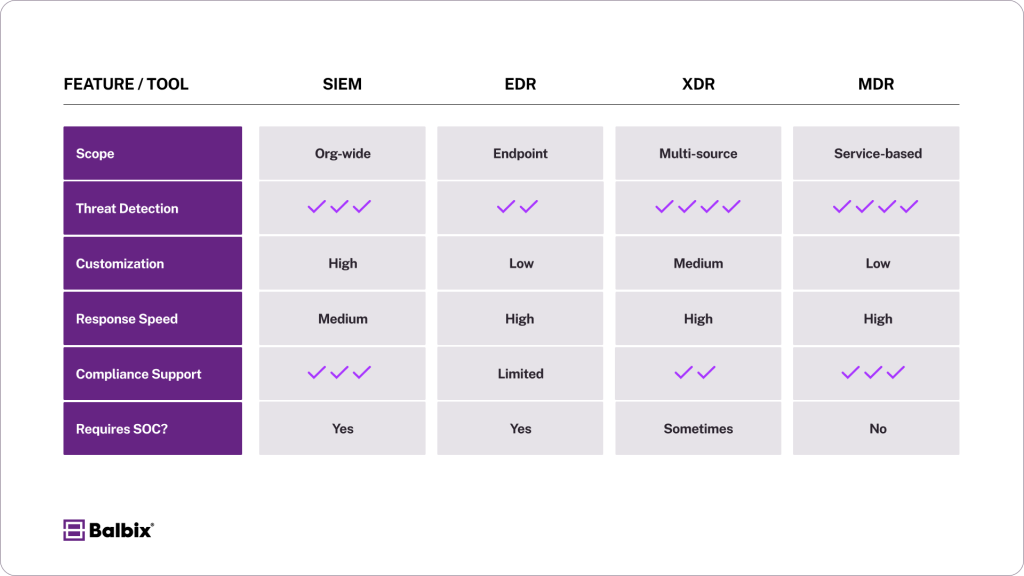
1. EDR (Endpoint Detection and Response)
EDR focuses on detecting and responding to threats at the endpoint level, such as laptops, desktops, and servers. These tools provide deep visibility into individual devices, allowing security teams to investigate and remediate threats directly at their source.
While EDR excels at protecting endpoints, it lacks the broad, centralized view of an organization’s entire IT environment that SIEM offers. Organizations often use EDR alongside other monitoring solutions to achieve a more holistic threat detection and response approach.
2. XDR (Extended Detection and Response)
XDR goes beyond EDR by combining data from multiple sources, such as endpoints, networks, cloud environments, and applications. Like SIEM, it provides a unified view of security events with built-in analytics, automation, and correlation capabilities that simplify investigation and response.
XDR solutions are often offered as single-vendor packages, integrating multiple tools into a seamless platform. While this reduces complexity and enhances ease of use, it may come at the cost of reduced customization compared to traditional SIEM platforms.
3. MDR (Managed Detection and Response)
For organizations without a dedicated Security Operations Center (SOC) or in-house security expertise, MDR offers a service-based alternative. With MDR, a third-party provider takes on the responsibility of threat detection, investigation, and response on behalf of the organization.
This allows smaller or resource-constrained businesses to benefit from expert cybersecurity management without the overhead of hiring and maintaining an in-house team. MDR providers often use advanced tools, including SIEMs and EDRs, to deliver services.
Other SIEM Alternatives and Adjacent Tools
In addition to the above options, other tools and approaches can either replace a traditional SIEM or complement it to enhance your security posture.
1. Open Source SIEM
For organizations seeking flexibility and cost savings, open-source SIEM solutions like ELK Stack (Elasticsearch, Logstash, Kibana), Wazuh, or Graylog are worth considering. These tools allow significant customization to meet specific needs but require substantial effort to deploy, tune, and maintain. Open-source SIEMs are ideal for organizations with skilled IT teams that have the time and resources to manage these platforms effectively.
2. Cloud-Based SIEM
Cloud-native SIEM platforms, such as Microsoft Sentinel, offer scalable, pay-as-you-go solutions that integrate seamlessly with cloud environments. These platforms eliminate the need to manage physical infrastructure while providing advanced capabilities like automated threat detection, machine learning-driven analytics, and native cloud integrations. Cloud SIEMs are particularly beneficial for organizations heavily reliant on cloud services or those looking to reduce operational overhead.
3. SOAR (Security Orchestration, Automation, and Response)
SOAR platforms are not direct replacements for SIEMs but are often used alongside them to enhance security efficiency. These tools focus on automating and orchestrating security workflows, such as incident response and threat hunting.
SOAR platforms help reduce alert fatigue and speed up response times by automating repetitive tasks and centralizing workflows. Organizations with mature security operations can use SOAR to optimize processes and empower their teams to focus on higher-priority tasks.
How SIEM Supports the Future of Cybersecurity
Emerging AI-powered attacks, zero-day vulnerabilities, and more make threat detection increasingly complex. Modern SIEM platforms increasingly incorporate AI/ML features to detect anomalies and reduce alert fatigue.
Whether your primary aim is to ensure compliance, enhance visibility, or improve threat response, SIEM remains a critical technology for achieving these goals.
Frequently Asked Questions
- What is SIEM and why is it important?
-
SIEM (Security Information and Event Management) is a technology that collects, analyzes, and correlates security data across an organization’s IT infrastructure. It is vital for detecting threats, enhancing visibility, streamlining compliance, and enabling efficient incident response.
- How does a SIEM system detect threats?
-
SIEM systems detect threats by aggregating data from servers, firewalls, and cloud applications. They apply behavioral analytics, correlation rules, and threat intelligence to identify suspicious patterns, such as unusual login attempts or unauthorized access.
- What are the key benefits of using a SIEM platform?
-
SIEM enhances threat detection, speeds up incident response, simplifies compliance reporting, provides centralized visibility, and improves overall operational efficiency by automating tasks, reducing manual effort, and minimizing response times.
- What are common alternatives to a traditional SIEM solution?
-
Alternatives to SIEM include EDR (Endpoint Detection and Response) for endpoint security, XDR (Extended Detection and Response) for unified threat detection, MDR (Managed Detection and Response) for outsourced monitoring, and open-source or cloud-based SIEMs that offer flexibility and scalability.
- How does modern SIEM integrate AI for cybersecurity?
-
Modern SIEM solutions leverage AI and machine learning to enhance threat detection, reduce false positives, and better anticipate emerging risks. These features help organizations respond faster to complex cyberattacks and mitigate risks more effectively.


