Security teams are drowning in alerts. From endpoint anomalies and phishing attempts to threat intel feeds and SIEM events, the volume of data to ingest, correlate, and act on is overwhelming—and often impossible to manage manually. That’s where SOAR comes in.
Security Orchestration, Automation, and Response (SOAR) platforms help streamline detection-to-response workflows by connecting tools, automating tasks, and codifying incident response. While SIEMs focus on data collection and analysis, SOARs are designed for action.
Here’s a technical look at what SOAR is, how it works, and how it fits into modern security operations.
What is SOAR?
SOAR, a term popularized by Gartner, refers to a category of platforms designed to streamline and automate security operations. SOAR stands for Security Orchestration, Automation, and Response. While the acronym remains widely used, some vendors now refer to this space as ‘security automation’ or ‘security operations platforms’ to reflect evolving capabilities.
SOAR performs three core functions:
- Orchestration – Connecting your existing tools (SIEMs, EDR, ticketing systems, threat intel sources) and enabling inter-tool communication.
- Automation – Executing predefined tasks (e.g., enrichment, triage, containment) without human input.
- Response – Enabling consistent, documented, and often automated actions based on incident context and severity.
SOAR platforms provide structured workflows and decision logic to drive repeatable, auditable processes at speed and scale.
What Is the Difference Between Security Automation and Orchestration?
Automation and orchestration are often used interchangeably in security operations, but they refer to distinct layers of functionality.
Automation is the execution of individual tasks without human intervention. For example, enriching an IP address with whois data or isolating a compromised endpoint via an EDR API are automated actions. These are usually discrete, rule-based, and repeatable, focused on speed and consistency at the task level.
Read more about security automation.
Orchestration connects and coordinates security tools so they can share data and trigger actions across systems. Workflow logic—such as decision branches and task dependencies—is typically handled in the playbook or automation layer.
For instance, a phishing response playbook that ingests a reported email, enriches indicators, checks historical logs, quarantines messages, and creates a case is an orchestrated workflow that leverages multiple automations.
In essence, automation handles the “what,” while orchestration governs the “when,” “how,” and “in what order.” SOAR platforms combine both to streamline and scale security operations.
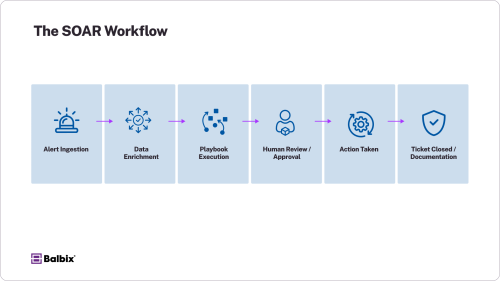
How SOAR Works
A SOAR platform acts as a centralized coordination layer across the security operations stack, enabling structured, repeatable, and semi- or fully-automated responses to diverse security events.
Its architecture typically integrates four core capabilities: orchestration, automation, intelligence, and response. These components work together to reduce manual effort, increase consistency, and accelerate time to resolution.
Orchestration: Connectors and Integration Frameworks
At the foundation of SOAR is its orchestration capability—unifying a fragmented toolset through a robust integration layer. This is accomplished via connectors and APIs and prebuilt or custom integrations that link the SOAR platform with other security and IT systems.
These may include SIEMs (e.g., Splunk, Microsoft Sentinel), EDR platforms (e.g., CrowdStrike, SentinelOne), firewalls, sandbox environments, threat intelligence platforms (e.g., VirusTotal, Recorded Future), and ITSM tools (e.g., ServiceNow, Jira).
These integrations allow SOAR to:
- Ingest alerts and telemetry from disparate systems
- Trigger response actions (e.g., block IP, isolate endpoint)
- Enrich data by querying external or internal intel sources
- Open or update tickets in workflow management tools
The breadth and reliability of these integrations directly impact the efficiency and scalability of SOAR workflows.
Automation: Playbooks and Execution Engine
The automation engine is responsible for carrying out predefined actions at machine speed. These actions are organized into playbooks—structured, logic-driven workflows triggered by specific alert types or event conditions.
Playbooks can:
- Parse and normalize alert data
- Enrich artifacts (e.g., domains, hashes) using threat intel or DNS/whois lookups
- Query past events or correlated logs from the SIEM
- Trigger containment or remediation steps, such as disabling user accounts or isolating devices
- Create or update tickets in ITSM systems
These workflows are typically defined in a visual or YAML-based interface and support complex logic (conditional branching, loops, error handling). Some playbooks are fully automated, while others include human-in-the-loop controls—checkpoints that require analyst review or approval before proceeding with potentially disruptive actions (e.g., quarantining a host or sending user notifications).
Intelligence: Contextual Enrichment and Correlation
Many SOAR platforms now include built-in threat intelligence modules or integrate directly with real-time threat scoring engines, enabling more accurate enrichment and prioritization.
Key enrichment and correlation activities include:
- IP/domain reputation checks
- Geolocation and whois lookups
- Asset criticality and vulnerability data mapping
- Historical alert correlation to detect broader attack patterns
By automatically aggregating this information, SOAR gives analysts a richer, more actionable view of each incident without requiring time-consuming manual lookups.
Response: Case Management and Incident Lifecycle
SOAR wraps the detection and response process in a case management system, which organizes alerts, artifacts, actions taken, and analyst notes into a single interface. This helps ensure consistent incident handling, facilitates collaboration between Tier 1–3 analysts, and preserves full audit trails for post-incident review, compliance, or metrics reporting.
Cases can be:
- Automatically generated from alert ingestion
- Escalated or closed based on playbook logic
- Reopened if new evidence emerges
All response actions, both manual and automated, are tracked, timestamped, and correlated within the case to provide full traceability.
Example: Phishing Alert Playbook
An everyday use case is the automated triage of phishing alerts. When a suspicious email is reported, the SOAR playbook begins by parsing the email header and extracting embedded indicators such as domains, URLs, and attachment hashes. These indicators are then checked against internal and external threat intelligence feeds.
The case is auto-closed if the IOCs are benign or previously marked as false positives. If malicious indicators are confirmed, the playbook queries historical SIEM data to identify other recipients or related activity.
It then automatically quarantines the email across all user inboxes, notifies the security team, and escalates the incident for further investigation. All actions and findings are logged in the case record for traceability throughout the process.
SOAR vs. SIEM: Complementary, Not Redundant
While SIEM and SOAR platforms often overlap in the security operations stack, they serve distinct functions:
| Feature | SIEM | SOAR |
| Core Function | Log aggregation & correlation | Incident response & automation |
| Input | Logs, events, telemetry | Alerts, indicators, case metadata |
| Output | Alerts, dashboards | Tickets, response actions, reports |
| Response | Manual or limited | Automated & orchestrated |
| Analyst Role | Investigate alerts | Investigate + respond |
Modern SOCs typically deploy both, feeding SIEM alerts into SOAR playbooks for triage, enrichment, and containment.
Key Use Cases for SOAR
SOAR becomes more powerful the more workflows you automate. While some organizations begin with simple enrichment tasks, high-performing teams build full-stack orchestration pipelines that address various security scenarios. Here are four of the most impactful use cases.
1. Phishing Response
Phishing Response is one of the most common and practical starting points for SOAR automation. When users report suspicious emails—often through integrated mailbox plugins—SOAR can automatically ingest those reports, extract relevant data like headers and attachments, and parse indicators such as URLs, IPs, and domains. It then queries threat intelligence feeds to determine reputation or known maliciousness.
Based on this analysis, the platform can automatically quarantine the email from user inboxes, delete duplicates enterprise-wide, and create a case for analyst review if needed.
2. Ransomware Containment
Ransomware Containment requires speed and coordination across multiple systems. SOAR can monitor for anomalous encryption behaviors flagged by EDR or SIEM tools, such as mass file renames or spikes in CPU usage from unauthorized processes.
When such behaviors are detected, SOAR playbooks can isolate affected endpoints from the network in real time, notify incident response teams, and even trigger automated workflows to restore from known-good backups. This containment workflow drastically reduces the blast radius of ransomware infections and shortens response windows.
3. Insider Threat Detection
Insider Threat Detection benefits from SOAR’s ability to correlate data across disparate systems. By ingesting events from DLP, IAM, and UEBA platforms, SOAR can identify behavioral anomalies that suggest potential insider activity, such as large-volume downloads outside business hours or access to sensitive systems outside an employee’s typical role.
These events can trigger investigative playbooks that aggregate contextual data, generate alerts, and automatically disable user accounts or revoke access privileges in high-severity scenarios.
4. Vulnerability Management
Vulnerability Management workflows can be fully orchestrated with SOAR. SOAR platforms can prioritize vulnerabilities using contextual risk data, such as known exploits, asset criticality, or business impact. The platform can then generate remediation tickets, route them to the appropriate owners with relevant configuration information, and track patch status.
Once remediation is confirmed, the SOAR playbook can verify closure through rescans and automatically close the loop in the case management system.
Benefits of SOAR
Implementing SOAR can result in:
- Lower MTTR – From hours to minutes with automated response.
- Fewer False Positives – Enrichment and correlation improve fidelity.
- Scalable Operations – One analyst can manage hundreds of alerts per day.
- Auditable Workflows – Every action is logged and replayable.
- Centralized Control – This reduces the need to manually switch between consoles for common tasks, though deep investigations may still require native tool interfaces.
Critically, SOAR doesn’t just automate—it codifies tribal knowledge into repeatable processes. This institutional memory is essential as teams grow or turnover.
Operational Considerations
While powerful, SOAR implementation isn’t trivial. Teams need to account for:
- Playbook Design – Building effective workflows that reflect actual response practices.
- Data Quality – Garbage in, garbage out. Enrichment depends on clean, structured inputs.
- Integration Overhead – Custom connectors may be required for niche or legacy tools.
- Change Management – Analysts must trust automation, especially when performing destructive actions.
Security engineers should also test and version-control playbooks like any production codebase, using staging environments where possible.
When Does SOAR Make Sense?
SOAR shines in environments where:
- Alert volume outpaces manual triage capacity
- Security tooling is mature but fragmented
- Incident response is inconsistent or poorly documented
- Teams want to scale without linear headcount growth
Even smaller orgs can benefit by automating high-frequency, low-complexity tasks first (e.g., phishing triage) and layering complexity over time.
The Future of SOAR: AI and Autonomous Response
Next-gen SOAR platforms increasingly incorporate ML and LLMs to assist decision-making, recommend actions, and summarize incidents. While some platforms enable limited autonomous response, such as endpoint isolation under predefined policies, full automation of destructive actions remains rare and highly controlled.
- Autonomous response loops
- Natural language playbook creation
- Proactive risk reduction workflows (e.g., patch prioritization)
Still, human oversight remains critical. The goal isn’t full automation—it’s augmented decision-making.
Final Thoughts
SOAR platforms work with with Balbix to automate response to high-priority cyber risks. Balbix identifies and prioritizes exposures—like unpatched vulnerabilities or misconfigurations—based on business context. This data flows into SOAR tools, which trigger automated playbooks to investigate, take action (e.g., isolate a host or create a ticket), and notify responders. As teams remediate, Balbix updates the risk posture, enabling faster, more accurate incident response with less manual effort.
Frequently Asked Questions
- What is SOAR and how does it help in cybersecurity?
-
SOAR (Security Orchestration, Automation, and Response) helps security teams respond to threats faster by automating repetitive tasks and coordinating tools.
- How is SOAR different from SIEM?
-
SIEM collects and analyzes security data for monitoring, while SOAR automates response actions based on that data, orchestrating workflows across systems.
- What types of tasks can SOAR automate?
-
SOAR can automate alert triage, data enrichment, IOC lookups, threat containment (like isolating endpoints), ticketing, and documentation.
- Do you still need humans if you use a SOAR platform?
-
Yes. SOAR automates routine tasks, but analysts still play a key role in reviewing high-impact incidents, approving sensitive actions, and refining playbooks.
- How does SOAR integrate with other cybersecurity tools?
-
SOAR platforms use APIs to connect with SIEMs, EDRs, threat intel feeds, and platforms like Balbix to enrich alerts and trigger contextual, automated responses.


