Traditional tools like firewalls and antivirus software can’t keep pace with today’s multi-vector ransomware attacks and targeted phishing campaigns. Managed Detection and Response (MDR) offers hands-on detection, investigation, and response services delivered by dedicated security experts.
This article will explain everything you need to know about MDR, how it works without the heavy lift of building in-house security operations.
What is MDR?
Managed Detection and Response (MDR) is a fully managed cybersecurity service that helps organizations detect and respond to advanced threats. Unlike basic monitoring tools, MDR combines threat intelligence, 24/7 monitoring, and rapid response to contain and neutralize attacks before they cause harm.
Key Components of MDR
- 24/7 Monitoring: Continuous surveillance of your systems to catch potential threats in real time.
- Advanced Threat Detection: Often uses AI-powered tools, behavioral analysis, and threat intelligence to identify known and emerging risks like malware or insider threats.
- Incident Investigation: Human experts analyze suspicious activity, confirming the severity and scope of incidents to minimize false alarms.
- Rapid Response: MDR providers act immediately to contain threats, limit damage, and support recovery efforts.
- Ongoing Reporting and Expert Guidance: Detailed post-incident analysis and recommendations help improve overall security posture.
The MDR Lifecycle
MDR follows a structured lifecycle, covering every phase from threat detection to resolution:
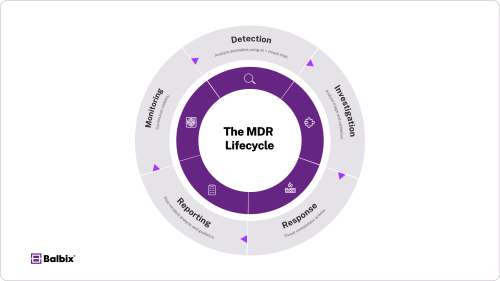
1. Monitoring
MDR providers continuously monitor your environment—including endpoints, networks, and log data—for indicators of compromise (IOCs) and anomalous behavior. This 24/7 visibility ensures rapid detection across the entire attack surface.
2. Detection
Suspicious activity is analyzed using a combination of AI-driven analytics, behavioral modeling, and up-to-date threat intelligence. This enables the identification of advanced threats such as ransomware, credential misuse, lateral movement, and insider attacks.
3. Investigation
MDR analysts triage and validate detected threats in real time. They assess context, severity, and potential business impact, eliminating false positives and reducing the noise your internal teams have to handle.
4. Response
Upon confirmation, MDR teams initiate predefined response actions—such as isolating hosts, terminating malicious processes, and executing containment playbooks—often aligned with frameworks like NIST or MITRE ATT&CK—to disrupt attacker activity rapidly.
5. Reporting and Recommendations
Each incident is followed by a detailed report outlining what happened, how it was handled, and recommended improvements to harden your environment and reduce dwell time in the future.
Why MDR Stands Out
MDR moves beyond alert-based models to deliver end-to-end threat management. Here are the key aspects that set it apart:
24/7 Threat Monitoring
Cyber threats don’t clock out at 5 PM, and neither do MDR providers. They ensure round-the-clock visibility into your IT environment so threats are detected and addressed as they happen, not hours (or days) later.
Proactive Threat Hunting
Reacting to threats isn’t enough. MDR teams leverage proactive threat hunting, searching for hidden risks using data analysis and adversary tactics before they escalate.
Advanced Tools with Human Expertise
While AI and machine learning power MDR technology, you also get access to cybersecurity professionals who validate threats and offer tailored remediation guidance. This optimal balance of man and machine greatly enhances accuracy and response times.
Scalable and Cost-Effective
Building an in-house security operations center (SOC) is time-consuming and expensive. MDR offers organizations the same level of advanced protection at a fraction of the cost by acting as an outsourced SOC.
Reduced Alert Fatigue
MDR filters out noise, ensuring you only focus on verified, high-priority threats. This reduces alert fatigue, particularly for lean IT teams.
Benefits of MDR
MDR delivers critical advantages to businesses, including:
- Faster Detection and Response: Reduce Mean Time to Detect (MTTD) and Mean Time to Resolve (MTTR) with immediate action on verified threats.
- Access to Security Expertise: Gain insights and expertise from seasoned security teams, bypassing the in-house hiring challenges.
- Minimized Business Disruption: Identify and neutralize threats before they escalate, ensuring minimal impact on operations.
- Scalable Security: Grow your cybersecurity capabilities without added internal resource demands.
- Enhanced Threat Protection: Benefit from cutting-edge AI tools and continuous threat intelligence updates.
Comparing MDR to MSSP, EDR, and XDR
Choosing the right security solution can be daunting. Here’s how MDR stacks up against other services and tools:
| Solution | Focus | Management | Detection & Response | Threat Hunting | Human Expertise |
| MDR | End-to-end detection & response | Managed by the provider | ✔️ | ✔️ | ✔️ |
| MSSP | Monitoring & log forwarding | Managed by the provider | Sometimes | Limited, often focused on log management | Limited |
| EDR | Endpoint threat detection | Typically in-house | ✔️ | Depends on team | ❌ |
| XDR | Cross-platform threat correlation | Hybrid or in-house | ✔️ | ✔️ | Varies by provider* |
*Note: Some XDR platforms are purely technology-focused, while others include or integrate with MDR services to offer analyst-led support and threat response.
Conclusion
As threat actors grow more sophisticated, organizations need more than basic monitoring—end-to-end threat detection, response, and risk reduction. Balbix complements MDR by providing continuous visibility into your cyber risk posture, helping you understand where you’re most vulnerable and how to prioritize what matters most. MDR and Balbix give security teams the intelligence and agility to stay ahead of modern threats.
Frequently Asked Questions
- What is Managed Detection and Response (MDR)?
-
Managed Detection and Response (MDR) is a fully managed cybersecurity service that detects, investigates, and responds to cyber threats using advanced tools, threat intelligence, and human expertise. It provides continuous monitoring, rapid response, and proactive threat hunting to protect businesses from evolving attacks.
- How does MDR work?
-
MDR services leverage 24/7 monitoring, AI-driven threat detection, and expert analysis to identify and classify threats. Once validated, the MDR team executes response actions, such as isolating compromised systems or stopping malicious processes, to minimize damage and secure the environment.
- What are the benefits of MDR?
-
MDR enhances threat detection and response speed, reduces alert fatigue, provides access to expert security talent, and offers cost-effective, round-the-clock protection. It’s an outsourced solution that delivers SOC-level security without the overhead of building and maintaining an in-house team.
- How is MDR different from MSSP, EDR, and XDR?
-
MDR combines advanced detection tools and human expertise for full threat response, unlike MSSPs, which focus on monitoring and log forwarding. Unlike standalone tools like EDR (endpoint-focused) and XDR (cross-platform), MDR offers proactive threat hunting, managed response, and comprehensive incident resolution.
- Who should consider using MDR services?
-
MDR is ideal for organizations without an in-house Security Operations Center (SOC), those struggling with alert fatigue, or businesses seeking expert-level cybersecurity support. It’s especially valuable for companies needing fast, scalable protection from advanced threats like ransomware and insider attacks.


