What is Cloud Computing?
Cloud computing delivers computing services, including servers, storage, databases, networking, software, and analytics, over the internet (“the cloud”). This model allows organizations to access and manage resources on demand, offering flexibility, scalability, and cost-efficiency.
Rather than investing in physical infrastructure, businesses pay for computing services from cloud providers. This approach supports rapid innovation, facilitates remote work, lower physical overhead, and enables global scalability.
Types of Cloud Deployment Models
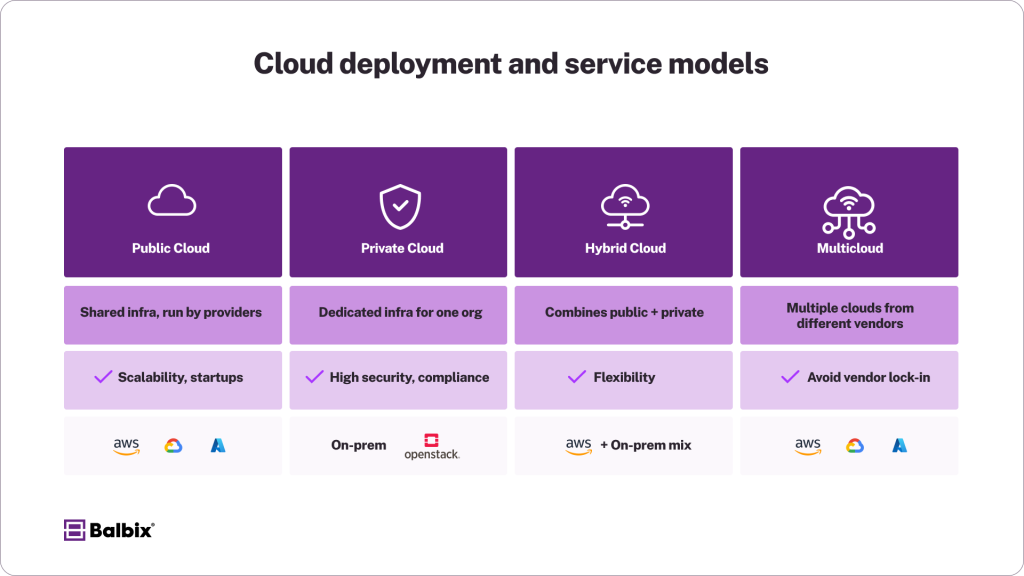
Public Cloud
Public clouds refer to shared IT infrastructures delivered over the internet, operated by third-party providers like AWS, Google Cloud, and Microsoft Azure. These providers own and manage the hardware and networking equipment, enabling organizations to lease resources on a subscription or pay-as-you-go payment structure.
Benefits:
- Scalability: Elastic scaling allows workloads to increase or decrease capacity automatically in response to demand spikes. For instance, e-commerce platforms often use public clouds to handle seasonal surges during holidays.
- Global Reach: Providers operate dozens of geographically distributed data centers, offering low-latency services across regions.
- Cost Efficiency: Shared infrastructure reduces operational costs, as there is no CAPEX (capital expenses) for hardware. Billing models such as pay-per-use or reserved instances further optimize budgets.
Technical Considerations:
- Security Models rely on shared responsibility frameworks. For example, AWS ensures the security of the cloud infrastructure, but users are responsible for securing configurations, applications, and data.
- Performance Challenges can arise due to noisy neighbors in multi-tenancy environments, though resource isolation mechanisms like Virtual Private Clouds (VPCs) mitigate such issues.
- Limited Customization exists because while managed services simplify deployment, they often lack the granular control some enterprise workloads need.
Private Cloud
A private cloud is a dedicated environment built exclusively for a single organization, either hosted on-premises or by a managed provider. These environments leverage virtualization and software-defined technologies to deliver cloud-like benefits while meeting specific organizational demands.
Benefits:
- Security and Compliance: Private clouds support stringent regulatory and internal governance requirements. For example, large enterprises can enforce strict data residency policies and maintain full visibility into their infrastructure to meet internal audit and compliance standards.
- Customization: Full-stack control enables tailored infrastructure design to support complex, enterprise-scale applications, such as ERP systems or custom analytics platforms, with optimized performance and integration.
Considerations:
- Virtualization Layers: Popular platforms such as VMware vSphere or Red Hat OpenShift enable private cloud functionality, providing features like centralized resource pooling and policy-based workload placement.
- Higher Cost Structure: Organizations bear the full burden of infrastructure procurement, maintenance, and scaling, which can offset the agility benefits of cloud.
- Edge Integration: Many private cloud architectures now support seamless integration with edge computing nodes for low-latency applications or distributed sensors, especially in IoT-heavy industries.
Hybrid Cloud
Hybrid clouds combine on-premises infrastructure (or private clouds) with public cloud services, creating a unified ecosystem where workloads, data, and applications can seamlessly transition between environments.
Common Use Cases:
- Data Residency: Organizations often store sensitive data locally in private clouds while running analytics or compute-intensive operations on public cloud resources.
- Workload Portability: For example, retailers employ a hybrid deployment when synchronizing backend inventory databases stored on private cloud servers with public-facing e-commerce platforms hosted on the public cloud.
- Disaster Recovery (DR): Hybrid models facilitate business continuity strategies by leveraging public cloud for off-site backup and failover mechanisms. Asynchronous block replication tools such as VMware Site Recovery are often employed in such architectures.
Tools and Technologies:
- Orchestration Frameworks: Modern hybrid cloud environments utilize tools like Kubernetes, HashiCorp Terraform, and Red Hat Ansible to automate workload deployment across platforms.
- Networking and Connectivity: Solutions such as AWS Direct Connect and Azure ExpressRoute provide private, high-bandwidth connections to mitigate latency and enhance data transfer reliability.
Multicloud
Multicloud strategies revolve around using two or more cloud providers to avoid vendor lock-in, optimize for performance, and build redundancies. Unlike hybrid clouds, multicloud environments do not necessarily require connectivity between platforms.
Scenarios for Multicloud Adoption:
- Avoiding Vendor Lock-in: By distributing workloads across AWS, Azure, and Google Cloud, for example, organizations retain flexibility in response to changes in provider offerings, pricing, or terms.
- Purpose-built Workloads: Certain providers excel in specific areas. For instance, Google Cloud’s TPU (Tensor Processing Units) offers unmatched performance for AI/ML workloads, while AWS Outposts addresses hybrid use cases.
- Redundancy: Implementing disaster recovery plans across multiple providers minimizes downtime risks tied to single-platform outages.
Challenges and Benefits:
- Operational Complexity: Multicloud environments demand sophisticated Cloud Management Platforms (CMPs) such as VMware Tanzu to monitor performance, manage resources, and enforce security policies consistently.
- Interoperability: The use of open standards (e.g., OpenAPI, CloudEvents) is critical for enabling cross-cloud communication. However, establishing unified logging, monitoring, and access control frameworks across providers remains complex.
Cloud Service Models
Infrastructure as a Service (IaaS)
IaaS provides essential resources like virtualized servers, storage, and networking, offering businesses control and scalability. Leading platforms such as AWS EC2, Azure Virtual Machines, and Google Compute Engine allow users to configure VMs, manage OS updates, and customize networking.
For example, an e-commerce platform can scale VMs during high traffic, preventing resource overuse. However, organizations must handle OS patching, application updates, and secure configurations to avoid risks like exposed storage buckets, making governance critical.
Platform as a Service (PaaS)
PaaS eliminates infrastructure concerns, providing pre-configured environments for application development and deployment. Services such as AWS Elastic Beanstalk and Google App Engine support agile development by offering automatic scaling and seamless integration with tools like Firebase.
While PaaS accelerates workflows, vendor lock-in and limited customizability can pose challenges, so teams should evaluate compatibility with existing systems.
Software as a Service (SaaS)
SaaS delivers ready-to-use applications via the Internet, removing local installation and maintenance requirements. Platforms like Salesforce and Google Workspace handle updates, infrastructure, and security, supporting efficient hybrid workflows.
Multi-tenant architecture enhances resource use, but organizations must ensure providers comply with privacy laws and implement strong encryption, authentication, and data recovery measures.
Serverless Computing
Serverless architecture allows developers to focus on code, with cloud providers managing infrastructure and scaling automatically. Services like AWS Lambda and Google Cloud Functions execute code based on events, charging only for compute time used.
For example, AWS Lambda can resize images after uploads, simplifying workflows. However, cold start delays and risks like event injection require strong security measures, including least privilege policies and robust input validation. Monitoring event logs for suspicious activities and securing code dependencies through regular vulnerability scanning and updates are critical steps to protect serverless applications from potential exploits.
Cloud-Native Security Tools and Techniques
Kubernetes Security
Kubernetes security involves leveraging container orchestration best practices to safeguard your system. This includes implementing pod security policies to control how pods interact, enforcing role-based access control (RBAC) to manage permissions, and using namespace isolation to separate workloads for better security and resource management. Regularly updating Kubernetes versions is also crucial to mitigate known vulnerabilities.
Container Security
Container security focuses on protecting containerized environments throughout their lifecycle. This includes scanning container images for known vulnerabilities before deployment, enforcing runtime security to detect and prevent malicious activity during execution, and ensuring that container registries are securely configured in order to avoid unauthorized access. Adding automated vulnerability scans and periodic auditing of configurations can further strengthen container security.
Cloud Security Frameworks and Standards
Security frameworks provide structure and benchmarks to help organizations protect their cloud operations effectively. These frameworks offer guidelines, best practices, and standards to address potential risks and vulnerabilities.
Examples include:
- NIST Cybersecurity Framework provides comprehensive guidance for identifying, managing, and mitigating cybersecurity risks. It helps organizations establish a robust security posture by outlining core functions such as identifying assets, protecting systems, detecting threats, responding to incidents, and recovering from disruptions.
- ISO/IEC 27017 is an international standard specifically designed for cloud service security. It provides detailed controls to secure cloud environments, including responsibilities for both cloud service providers and users. This framework ensures clarity and accountability in managing cloud-specific risks.
- Cloud Security Alliance (CSA) is a globally recognized organization that offers best practices, tools, and checklists to secure cloud usage. Their Cloud Controls Matrix (CCM) and STAR program provide practical resources for organizations to manage cloud security and compliance effectively.
Incident Response in Cloud Environments
A robust incident response (IR) plan tailored for cloud environments is critical for minimizing the impact of security incidents and ensuring business continuity. Key components of such a plan include:
- Real-time log analysis of cloud activities: Continuously monitoring logs for unusual or suspicious activity helps detect potential threats early. This includes reviewing access logs, API calls, and user behavior to identify anomalies.
- Collaboration with cloud vendors during forensic investigations: Establishing clear communication channels with your cloud service providers ensures quicker resolution during an incident. Vendors can provide specialized tools, expertise, and insights into their platform’s security features to aid forensic analysis.
Cloud Security Automation
Automation is critical in improving compliance and security within cloud environments, enabling organizations to operate more efficiently while reducing human error. Through advanced tools and practices, security becomes proactive and scalable:
- Infrastructure as Code (IaC) and Security as Code (SaC) ensure consistent, repeatable configurations across your cloud infrastructure. These practices allow you to define and manage your infrastructure and security policies through code, minimizing manual effort and making maintaining a secure and compliant environment easier.
- Continuous Monitoring and Automated Compliance Checks provide real-time insights and instant detection of misconfigurations, vulnerabilities, or policy breaches. Identifying potential issues as they arise, these tools help mitigate risks quickly, ensuring your cloud environment meets security and compliance standards at all times.
Vendor Risk Management and Third-Party Dependencies
Managing vendor risk and third-party dependencies is crucial to maintaining a secure and resilient cloud environment. This involves thoroughly evaluating cloud vendor security postures to ensure they align with your organization’s standards and risk tolerance.
Key steps include:
- Adherence to high security and compliance standards, such as SOC 2 and ISO 27001 certifications, confirms the vendor’s commitment to protecting data and maintaining operational integrity.
- Proactively identifying and addressing service dependencies to minimize risks of vendor lock-in, which can limit flexibility and increase long-term costs if switching providers becomes necessary.
- Implementing multi-vendor strategies to build redundancy and ensure robust failover mechanisms allows uninterrupted operations even if one vendor experiences downtime or other service disruptions.
Quantum Computing and Its Impact on Cloud Security
Quantum computing poses a significant threat to existing encryption algorithms, such as RSA, by potentially rendering them obsolete. This is because quantum computers, with their immense processing power, can solve complex mathematical problems that traditional encryption relies on to remain secure.
Without proactive measures, sensitive data encrypted today could be vulnerable in the near future. Transitioning to quantum-resistant techniques, like post-quantum cryptography, is essential to prepare for these risks. These advanced cryptographic methods are specifically designed to withstand attacks from quantum computers, ensuring that data remains secure even as this new technology evolves.
8 Best Practice Strategies for Cloud Computing
- Shadow IT Risks: Unapproved cloud usage introduces vulnerabilities and compliance gaps. Enforce policies requiring approved services with integrated monitoring tools to maintain visibility and control.
- Data Breaches and Loss: Sensitive data remains a prime target. Protect it with encryption at rest (e.g., AES-256) and in transit (e.g., TLS). Implement efficient key management and rotate keys regularly to safeguard assets.
- Insecure Interfaces and APIs: Poorly secured APIs can expose critical endpoints. Enhance security by limiting exposures, employing robust authentication methods (e.g., OAuth), and monitoring for abnormalities.
- Weak Identity and Access Management (IAM): Insufficient access controls can compromise security. Implement multi-factor authentication (MFA), role-based access control (RBAC), and single sign-on (SSO) to restrict unauthorized access.
- Lack of Zero-Trust Practices: Relying on legacy trust models increases risk. Adopt zero-trust policies by verifying all users, devices, and applications dynamically with micro-segmentation and context-aware access rules.
- Insufficient Monitoring and Auditing: Gaps in oversight can leave threats undetected. Deploy Security Information and Event Management (SIEM) systems and conduct regular audits using frameworks like NIST to maintain compliance and safety.
- Misconfiguration and Compliance Oversights: Poorly configured cloud environments are vulnerable. Use Cloud Security Posture Management (CSPM) tools to automate identification of misconfigurations and enforce policy compliance.
- Human Error and Unawareness: Employees can unknowingly expose systems to risks through phishing or shadow IT. To enhance awareness, provide continuous training on cybersecurity best practices and simulate attacks.
Read more about cloud security.
How Balbix Helps Organizations with Secure Cloud Computing
Balbix empowers organizations to achieve secure computing by providing AI-powered visibility into their entire attack surface, helping to identify and prioritize vulnerabilities based on risk impact. Its automation capabilities streamline response strategies, reducing time to mitigate potential threats and improving security posture.
With real-time insights and predictive analytics, Balbix enables proactive decision-making to focus on the most critical business exposures. Integrating seamlessly with existing tools enhances operational efficiency while ensuring compliance with security frameworks.
Frequently Asked Questions
- What are the main types of cloud deployment models?
-
The main cloud deployment models are public cloud, private cloud, hybrid cloud, and multicloud.
- Public cloud services are provided by third-party vendors like AWS or Azure and are shared among users.
- Private cloud environments are dedicated to a single organization, offering more control and security.
- Hybrid cloud combines on-premises or private infrastructure with public cloud resources, enabling flexibility and data residency control.
- Multicloud uses services from multiple cloud providers without requiring tight integration, helping to avoid vendor lock-in and improve redundancy.
- Public cloud services are provided by third-party vendors like AWS or Azure and are shared among users.
- What are the different cloud service models (IaaS, PaaS, SaaS)?
-
Cloud service models include Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS):
- IaaS delivers virtualized computing resources like servers and storage (e.g., AWS EC2).
- PaaS offers pre-configured environments for app development and deployment (e.g., Google App Engine).
- SaaS provides ready-to-use applications over the internet (e.g., Salesforce, Google Workspace).
Each model differs in how much control the user vs. the provider has over customization and maintenance responsibility.
- IaaS delivers virtualized computing resources like servers and storage (e.g., AWS EC2).
- What is serverless computing and how does it work?
-
Serverless computing allows developers to run code without managing infrastructure. Services like AWS Lambda and Google Cloud Functions execute code in response to events and scale automatically. Users only pay for the compute time used, making it cost-efficient.
However, security measures such as input validation, least privilege policies, and cold start mitigation are critical to protect against threats in serverless environments. - How can organizations secure cloud environments effectively?
-
To secure cloud environments, organizations should:
- Use encryption for data at rest and in transit.
- Apply multi-factor authentication (MFA) and role-based access control (RBAC).
- Regularly scan for vulnerabilities in containers and cloud workloads.
- Follow frameworks like NIST Cybersecurity Framework and ISO/IEC 27017.
- Automate security via Infrastructure as Code (IaC) and continuous monitoring tools.
Implementing these strategies helps reduce misconfigurations, data breaches, and compliance risks.
- What are the risks of quantum computing for cloud security?
-
Quantum computing threatens current encryption methods like RSA and ECC, which protect cloud data. Once mature, quantum computers could break these algorithms, exposing sensitive information.
To prepare, organizations must adopt post-quantum cryptography, which includes quantum-resistant encryption algorithms designed to withstand attacks from quantum-capable systems. Transitioning early helps ensure long-term data confidentiality.