Both penetration testing (pen testing) and vulnerability scanning are crucial tools for identifying weaknesses in a network or system. While these techniques aim to improve security and posture, they differ in approach, scope, and outcome. Knowing when to use each can distinguish between identifying a potential breach and leaving your organization vulnerable to attack.
What is Penetration Testing and Vulnerability Scanning?
Before diving into the differences, let’s clarify what each method involves:
Penetration Testing is a simulated or real-world cyberattack performed by security professionals to uncover exploitable vulnerabilities in an organization’s systems or networks. It often involves a mix of automated tools and manual techniques to see how far an attacker can go once inside.
The Penetration Testing Execution Standard (PTES) provides a comprehensive approach to conducting penetration tests. It is divided into seven phases:
- Pre-Engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post-Exploitation
- Reporting
Vulnerability Scanning is an automated process that scans systems for known vulnerabilities, such as unpatched software, misconfigurations, and missing security controls. It is typically repeated regularly to identify new and mitigated issues.
The vulnerability scanning (management) process typically includes the following stages:
- Identification: Discovering vulnerabilities in a system.
- Evaluation: Assessing the flaws’ severity and impact.
- Remediation: Fixing the flaws.
- Verification: Checking if the fixes are effective.
- Reporting: Documenting everything.
Key Differences Between Penetration Testing and Vulnerability Scanning
While both strategies aim to identify security weaknesses, their methods, scope, and intended results differ. Understanding these differences helps organizations choose the right tool for their security needs.
Automation vs. Manual Testing
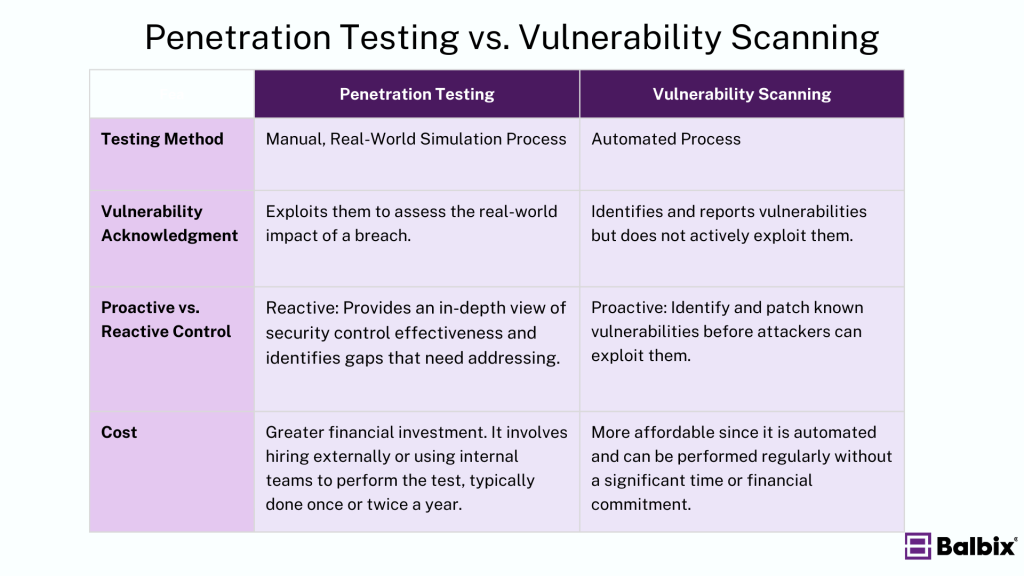
Vulnerability Scanning is an automated process, designed to quickly scan your network and systems for known vulnerabilities. Automated scans reduce human error and allow for repeatable, consistent results.
Penetration Testing, on the other hand, is usually a manual process. Skilled security professionals simulate a real-world attack, often bypassing traditional defenses to see how an attacker could exploit vulnerabilities. While tools assist pen testers, the human element remains crucial for finding more complex vulnerabilities.
Exploiting Vulnerabilities
Vulnerability Scanning identifies and reports vulnerabilities but does not actively exploit them. It helps organizations build an inventory of weaknesses that need to be addressed.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

Penetration Testing, however, goes beyond identifying vulnerabilities—it exploits them to assess the real-world impact of a breach. This provides valuable insights into how a malicious actor might move through the system and what data could be compromised.
Preventive vs. Reactive Controls
Vulnerability Scanning is primarily a preventive measure. It helps security teams identify and patch known vulnerabilities before attackers can exploit them.
Penetration testing is often used as a reactive or detective control. It provides an in-depth view of how effective your current security controls are and identifies gaps that need to be addressed. Organizations often run pen tests after significant changes to their networks or systems.
Financial Investment Required
Vulnerability Scanning is generally more affordable since it is automated and can be performed regularly without a significant time or financial commitment.
Penetration testing, being labor-intensive and more thorough, requires a greater financial investment. It involves hiring cybersecurity professionals or using internal team resources to perform the test, typically done once or twice a year for high-risk environments.
Gain Visibility of Your Cyber Risk with Balbix
Penetration testing and vulnerability scanning are crucial for identifying security gaps, but relying on them alone may not give you complete visibility into your cyber risk. While vulnerability scanning provides an inventory of known risks, and penetration testing simulates a real-world attack, it’s also important to consider the business impact of these vulnerabilities. Each of the security disciplines directly influences the effectiveness of an organization’s ability to respond to present and emerging threats.
Balbix’s AI-powered exposure management platform goes beyond traditional scanning and testing methods by continuously monitoring your attack surface and prioritizing vulnerabilities based on business risk. Balbix helps organizations move beyond detecting vulnerabilities and gain actionable insights to reduce overall cyber risk. With real-time visibility and automated workflows, your security team can focus on what matters most: protecting your business. By leveraging the learnings from each technique, resources can be focused on dealing with high-priority events or tasks.
Frequently Asked Questions
- What is the main difference between vulnerability scanning and penetration testing?
-
The main difference lies in their depth and focus. Vulnerability scanning is like a health check-up, identifying known weaknesses in a system using automated tools. It’s broad and relatively surface-level.
Penetration testing, on the other hand, is more like a stress test. It’s a comprehensive, hands-on examination where experts actively try to exploit vulnerabilities in a system, simulating a real-world attack. This approach is deeper and aims to test the system’s resilience to security breaches.
- What is a penetration and vulnerability tester?
-
A penetration and vulnerability tester is a professional who simulates cyber attacks on a company’s systems to find security weaknesses. They are like good hackers who help improve security before real hackers can cause harm.
They use various tools and techniques to uncover and report vulnerabilities, helping businesses protect their data and networks from potential threats. They play a crucial role in maintaining a company’s cybersecurity health.
- What is the greatest advantage of vulnerability scanning over penetration testing?
-
The greatest advantage of vulnerability scanning over penetration testing is its efficiency in quickly identifying and cataloging potential vulnerabilities across a broad network or system with minimal resource expenditure.
Unlike penetration testing, which takes a more in-depth, manual approach to exploit vulnerabilities, vulnerability scanning automates the detection process, making it a faster, less labor-intensive option for maintaining cybersecurity.