Quantum computing is no longer confined to science fiction or theoretical physics. It’s rapidly becoming a groundbreaking technology poised to redefine how we approach data, algorithms, and cybersecurity. Particularly for IT managers, cybersecurity professionals, and tech enthusiasts, understanding how quantum computing reshapes the cybersecurity landscape isn’t just fascinating; it’s essential.
This post will unpack the basics of quantum computing, its role in cybersecurity, and actionable steps for preparing your organization for the quantum era. Whether you’re looking to enhance threat detection or protect sensitive data, quantum computing offers opportunities and risks that demand attention today.
What is Quantum Computing?
At its core, quantum computing uses the fundamental principles of quantum mechanics—such as qubits, superposition, and entanglement—to process data at significantly faster rates than classical computers for certain types of problems.
Quantum computers use principles of quantum mechanics to solve specific problems much faster than classical computers, particularly those involving optimization, cryptography, and complex simulations.
Key Differences from Classical Computing
Traditional computers store information in binary bits of 0s or 1s. Quantum computers, however, use qubits (quantum bits), which can represent both 0 and 1 simultaneously due to superposition—a fundamental principle of quantum mechanics where a particle exists in multiple states until measured. This capability allows quantum computers to perform multiple calculations at once.
Furthermore, qubits leverage entanglement, a phenomenon where two or more qubits become correlated so that the state of one instantly influences the state of the other, regardless of distance. These properties enable quantum computers to solve problems exponentially faster than classical machines.
Below is a comparison table between Traditional (Classical) Computing and Quantum Computing that breaks down each by specific features:
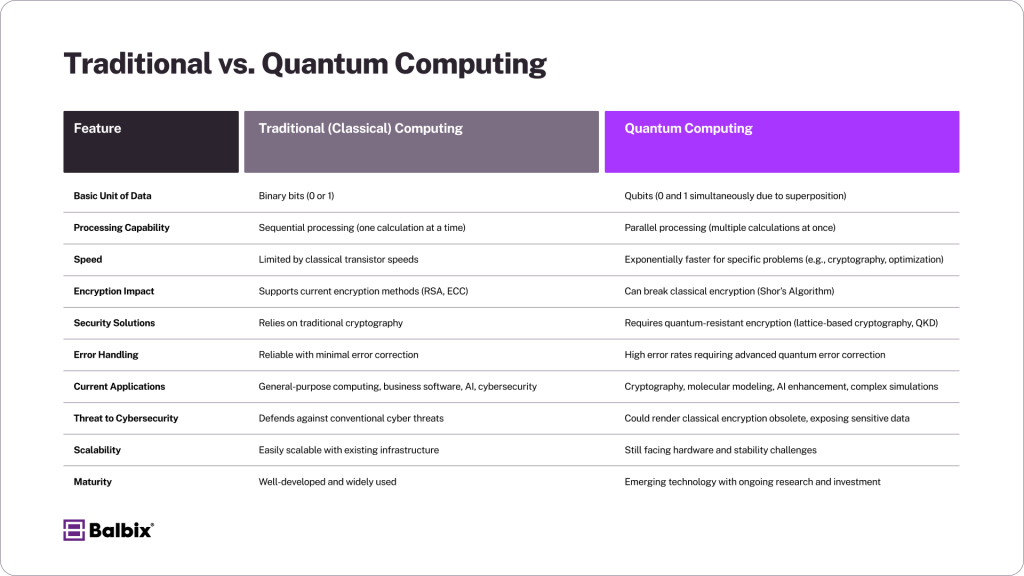
Impact on Computational Speed
The ability to process multiple calculations simultaneously gives quantum computers a significant edge in speed for specific problems. Problems that require billions or even trillions of computations—such as optimizing complex systems, modeling molecular interactions, or breaking encryption algorithms—can be solved significantly less by a quantum computer. In contrast, traditional machines would require decades or even longer to reach the same results. This leap in processing power has profound implications across various fields.
For example, in cybersecurity, quantum computers could crack traditional encryption methods, necessitating the development of quantum-resistant cryptographic systems. However, it’s important to note that quantum speedup applies to specific types of problems, and for many tasks, classical computers still outperform quantum systems.
Quantum computing is still in its infancy, with challenges like error correction, scalability, and hardware development to overcome. However, its potential to reshape industries and solve previously unsolvable problems continues to drive significant research and investment worldwide.
Quantum Computing in Cybersecurity
Quantum computing blends significant breakthroughs with inherent risks in cybersecurity. Here’s a breakdown of its current applications and threats:
Current Use Cases
1. Encryption and Decryption
Classical encryption methods, such as RSA and Elliptic Curve Cryptography (ECC), rely on complex mathematical problems, like factoring large numbers or solving discrete logarithm problems, which are computationally infeasible for traditional computers to break. ECC uses the algebraic structure of elliptic curves over finite fields to create secure cryptographic keys.
However, future large-scale quantum computers could break these encryption standards by leveraging Shor’s Algorithm, a quantum algorithm that efficiently factors large prime numbers and computes discrete logarithms, rendering RSA and ECC encryption vulnerable.
Threat: Sensitive data, financial systems, and networks protected by these encryption technologies could become exposed to quantum-enabled attacks.
Solution: Quantum-resistant encryption algorithms, such as lattice-based cryptography, are being developed to mitigate this risk. Lattice-based cryptography is currently considered quantum-resistant because known quantum algorithms, including Shor’s Algorithm, do not efficiently solve its underlying mathematical problems.
The Role of NIST in Quantum-Resistant Cryptography
Recognizing the urgency of quantum threats, the National Institute of Standards and Technology (NIST) has been leading a global initiative to develop quantum-resistant cryptographic standards. As part of its Post-Quantum Cryptography (PQC) Standardization Project, NIST has been evaluating and selecting encryption algorithms designed to withstand attacks from quantum computers.
These post-quantum cryptographic algorithms, such as lattice-based cryptography, are built on mathematical problems that remain infeasible for quantum computers to solve efficiently—even with advancements like Shor’s Algorithm. NIST has already identified promising candidates for public-key encryption and digital signatures, which are expected to replace current standards like RSA and ECC in the coming years.
For cybersecurity professionals, organizations must begin transitioning towards quantum-safe encryption sooner rather than later. Businesses and government agencies should monitor NIST’s progress and plan migration strategies to ensure that sensitive data remains secure in a post-quantum world.
2. Advanced Threat Detection
With real-time data processing, quantum computers excel at analyzing massive datasets rapidly. AI-powered cybersecurity solutions are improving, and while quantum-enhanced machine learning is still in the early stages, researchers are exploring quantum computing’s potential to accelerate AI algorithms.
Example: AI-powered threat detection is enhancing security today, and in the future, quantum computing may improve AI’s ability to analyze vast amounts of data faster, flagging potential threats before they escalate.
3. Quantum Key Distribution (QKD)
Unlike traditional key exchange protocols, Quantum Key Distribution (QKD uses quantum mechanics to securely exchange cryptographic keys. Any attempt to intercept a QKD transmission disturbs the quantum state, making the attack detectable and preventing undetected eavesdropping.
A key feature of QKD is its inherent security: any eavesdropping attempt disturbs the quantum state of the key, making unauthorized interception detectable and preventing data from being compromised. However, QKD does not address vulnerabilities in classical infrastructure or endpoint security.
Use Case: Secure communications for governments, financial institutions, and highly regulated industries.
Potential Cybersecurity Risks with Quantum Computing
Quantum computing offers immense potential but also introduces significant cybersecurity risks, particularly in the wrong hands. As quantum technology advances, current cryptographic defenses may become obsolete, exposing sensitive information and critical infrastructure to unprecedented threats. Consider these extreme cases of misuse:
- Compromising Financial Systems: A bad actor with access to a quantum computer could decrypt previously secure transaction records, disrupt banking and trading platforms, or manipulate global payment systems. The financial sector, which relies on encryption for securing transactions and customer data, could face severe instability and fraud risks if quantum-powered attacks bypass existing security measures.
- Private Data Breach: Many encryption standards, including RSA and ECC, protect sensitive user information such as healthcare records, government communications, and corporate intellectual property. If quantum computers break these encryption methods, personal data could be exposed on a massive scale, leading to identity theft, espionage, and financial fraud.
- Threats to National Security: Governments store classified intelligence, defense strategies, and critical infrastructure blueprints behind layers of encryption. A quantum-enabled cyberattack could dismantle these defenses, giving adversaries access to confidential military operations, surveillance data, and diplomatic communications.
- Destabilization of Global Communications: Secure online communications, including email encryption, virtual private networks (VPNs), and messaging apps, rely on cryptographic protocols that quantum computing could eventually render ineffective. This could lead to widespread privacy violations, corporate espionage, and loss of trust in digital communication channels.
Practical Applications for Cybersecurity Professionals
The emergence of quantum computing presents an opportunity to strengthen every layer of cybersecurity. Here are actionable strategies to help teams begin adapting early:
- Invest in Quantum-Resistant Algorithms: Start exploring quantum-safe encryption standards. Organizations like NIST (National Institute of Standards and Technology) are working to standardize post-quantum cryptography that is resistant to potential quantum decryption methods.
- Collaborate with Research Institutions: Partnering with academic or research organizations helps businesses stay informed about cutting-edge quantum advancements. Many institutions provide frameworks tailored specifically for enterprises preparing for the quantum future.
- Adopt Proactive Threat Monitoring: Enrich your cybersecurity arsenal with tools that leverage AI and new technologies to detect and respond to sophisticated threats. Being able to adapt quickly is invaluable.
- Upskill Your Team: Invest in employee training to inform your IT and cybersecurity teams on quantum developments. Encourage certifications or courses focusing on quantum computing’s role in network security.
- Evaluate AI Integration: Many AI-powered tools are compatible with current cybersecurity infrastructure. Pair your AI tools with emerging quantum capabilities to improve incident response and reduce recovery times.
The Future of Quantum Computing in Cybersecurity
Quantum computing in cybersecurity may sound like an abstract concept today, but it is quickly becoming tangible. With its dual capacity for immense computational capabilities and the potential to upend existing encryption techniques, quantum computing sits at the center of a high-risk, high-reward scenario for businesses globally.
Start protecting your organization by investing in quantum-safe encryption, exploring real-time threat detection tools, and collaborating with quantum leaders across academia and industry. Waiting until the quantum era is underway could leave your organization vulnerable to significant risks.
Frequently Asked Questions
- What is quantum computing, and how does it differ from classical computing?
-
Quantum computing is a revolutionary technology that leverages the principles of quantum mechanics to process information in ways classical computers cannot. While classical computers use bits (0s and 1s) to represent data, quantum computers use qubits, which can exist in multiple states simultaneously thanks to superposition.
Additionally, entanglement allows qubits to be correlated, enabling faster and more complex computations. This unique approach makes quantum computers exceptionally powerful for tasks like cryptography, optimization, and simulations.
- What is quantum-resistant cryptography, and why is it necessary?
-
Quantum-resistant cryptography, also known as post-quantum cryptography (PQC), consists of encryption methods designed to withstand attacks from quantum computers.
Classical encryption methods like RSA rely on the difficulty of factoring large prime numbers—a problem quantum computers could solve exponentially faster using Shor’s Algorithm. In response, institutions like NIST (National Institute of Standards and Technology) are developing quantum-safe encryption standards, such as lattice-based cryptography, which remains resistant to quantum decryption.
- What is Quantum Key Distribution (QKD), and how does it enhance cybersecurity?
-
Quantum Key Distribution (QKD) is a secure communication method that uses quantum mechanics to encrypt data. Unlike traditional key exchange protocols, QKD ensures that any attempt to intercept the transmission alters the quantum state of the key, making the intrusion immediately detectable. This makes QKD highly secure for transmitting sensitive data, particularly in industries like finance, government, and healthcare.
- What industries are most at risk from quantum cyber threats?
-
Industries heavily reliant on encryption, such as finance, healthcare, government, and telecommunications, face the greatest risk from quantum cyber threats. If quantum computers break current encryption protocols, sensitive financial transactions, patient records, government intelligence, and secure communications could be exposed. Organizations in these sectors must prioritize adopting quantum-resistant encryption to safeguard their digital assets.


