Static application security testing (SAST)
What is SAST?
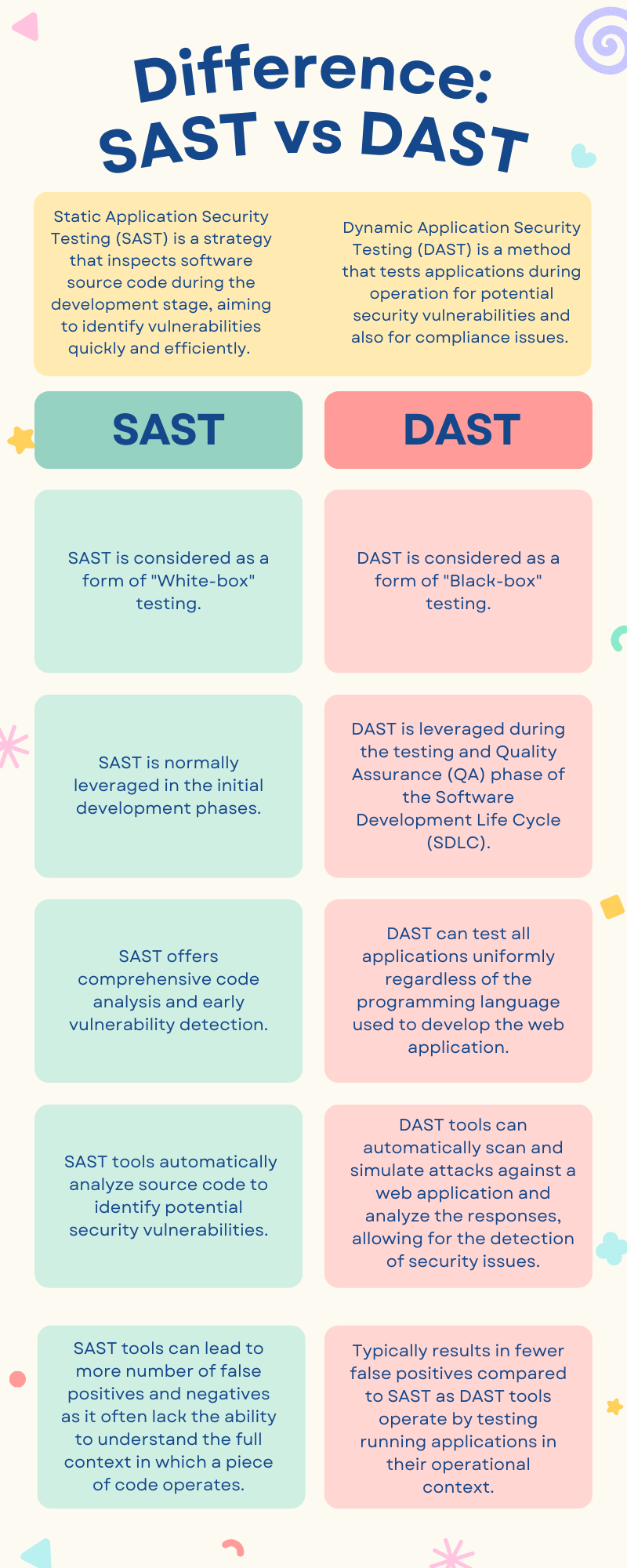
- Static Application Security Testing (SAST) is an AppSec testing strategy that inspects software source code during the development stage, aiming to identify vulnerabilities quickly and efficiently. SAST is also often referred to as “white-box” testing. White-box, as the name suggests, is about transparency – the tester gets a look under the system’s hood. Think of white-box testing as having a full architectural plan of the house before you enter it. By studying the plan, you gain the knowledge of where the doors, windows and other vulnerable entry points to the house are. In cybersecurity terms, this means accessing and scrutinizing a system’s source code to catch security issues early on. This practice of static source code analysis is as old as computing itself. The technique spread to security in the late 90s, with the first public discussion of SQL injection in 1998 when Web applications began integrating new technologies.
SAST Advantages
- Early Vulnerability Detection: SAST tools help identify the security vulnerabilities during the early stages of development. The earlier the issues are detected, the lower is the cost of fixing vulnerabilities.
- Comprehensive Code Analysis: SAST tools are typically designed to analyze the complete codebase and help identify the issues more reliably than a human can. It ensures that potential security issues are found timely.
- Precise Issue Pin-Pointing: SAST tools simplifies the remediation process by helping pinpoint the exact areas where vulnerabilities exist in the code. This allows the developers to fix the issues promptly, saving time and effort.
- Real-Time Feedback and Visual Reports: SAST provides immediate feedback on detected issues, often including visual representations. This instant response allows developers to correct errors on the go. Customizable reports also facilitate tracking and management of identified vulnerabilities.
SAST Limitations
- False Positives and Negatives: One of the limitations of the SAST tools is the possibility of a higher number of false positives and negatives. A false positive occurs when the SAST tool flags a piece of code as a vulnerability, but in reality, it’s not a security risk. A false negative happens when the SAST tool does not detect a real vulnerability that exists in the code. This leads to developers spending additional resources to validate the accuracy.
- Language-Dependence: SAST tools are generally programming language-dependent, which means a different tool may be required for each programming language used. This can result in operational challenges, complicating the maintenance and management of these tools.
- Cannot Detect Runtime Issues: Since SAST analyzes the codebase without executing the code, it cannot identify runtime issues like authentication problems or server misconfigurations.
Dynamic application security testing (DAST)
What is DAST?
- Dynamic Application Security Testing (DAST), also referred to as “black-box” testing, is a AppSec testing method that tests applications during operation for potential security vulnerabilities and also for compliance issues. DAST operates from the outside in, interacting with the web front-end without any need for source code or binaries. This is its key point of differentiation from SAST, which requires access to source code. Think of black-box testing technique as something that treats the system under test as an opaque box – the inner workings are not visible to the person testing. Hence the tester interacts directly with the application’s front-end (instead of the source code), simulating attacks to identify potential vulnerabilities. It’s similar to testing a locked safe by trying different combinations rather than examining the lock mechanism.
- DAST tools are typically used during the testing and Quality Assurance (QA) phase of the Software Development Life Cycle (SDLC). They work by introducing faults, which are potential vulnerabilities or weaknesses, into an application to test different code paths. These faults can include various scenarios and inputs that may be exploited by attackers. For example, a DAST tool may introduce a fault by sending unexpected or malicious input to a web application’s login page. This input could include SQL injection queries or cross-site scripting payloads, which are common attack vectors. By doing so, the DAST tool tests whether the application properly handles and sanitizes user inputs. Essentially, DAST tools simulate attacks on the application to uncover potential security flaws and architectural weaknesses, making them an integral part of a comprehensive cybersecurity strategy.
DAST Advantages
- Issue Detection at Runtime: DAST tools analyze a running application, making it possible to identify issues like authentication and server configuration flaws that only arise during runtime. This is something static testing methods can’t do.
- Programming Language Independent: DAST is not dependent on the programming languages used to develop the web application. It can test all applications uniformly, whether built with off-the-shelf or customized frameworks.
- Extensive System Evaluation: DAST not only tests the application but also middleware systems such as web servers, databases, and proxies. This comprehensive analysis helps identify vulnerabilities in the broader infrastructure, not just within the application.
- Help with Encryption Testing: DAST tools attempt to break encryption algorithms from the outside, ensuring that your application’s encryption measures are robust and effective.
- Less False Positives: DAST typically results in fewer false positives, making the security testing process more efficient and reliable. It also provides a less complex and cost-effective alternative to SAST, making it more accessible for smaller teams or projects.
Interactive application security testing (IAST)
What is IAST?
- Interactive Application Security Testing (IAST) is an innovative approach to AppSec testing, blending elements from Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) to reveal software vulnerabilities. The analogy that comes closest to explain how IAST works is that of a bilingual interpreter who understands and translates two languages. Similarly, IAST interacts with the program and utilizes sensors integrated within the application to identify potential issues during its operation. This approach is similar to how DAST operates, but it is important to note that IAST’s sensors are specifically built within the application server itself.
- IAST tools employ a software instrumentation strategy to evaluate the application’s performance and uncover vulnerabilities. They function like vigilant security guards, where agents and sensors persistently oversee the application’s operations during both automated and manual testing processes.
Guide
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

IAST Advantages
- Early Detection of Issues: IAST tools promote a “Shift-left” approach, meaning testing is performed during the early stages of the project lifecycle. This early detection of vulnerabilities helps minimize costs and delays.
- Detailed Vulnerability Insights: IAST provides detailed information about the root of vulnerabilities, including the exact location in the code, making it easier for security teams to address specific flaws promptly.
- Integration with CI/CD Tools: IAST can seamlessly integrate with continuous integration and continuous development (CI/CD) tools, enabling continuous security testing and making it ideal for modern, agile development processes.
- Broad Range of Testing Capabilities: Combining the strengths of SAST and DAST, IAST allows for a more comprehensive security analysis, identifying a wider range of vulnerabilities. It even allows API testing, crucial for products using microservices.
IAST Limitations
- Proprietary Tools: IAST tools are often proprietary, meaning there could be a high reliance on the specific supplier for ongoing support and updates.
- Limited Language Support: Unlike DAST, IAST may not support as wide a range of programming languages, which could limit its usability across different development environments.
- Performance Impact: As IAST tools require the installation of security sensors and agents within the web application, this could potentially slow down the application’s performance.
- Coverage Responsibility: Since IAST tools analyze the features of an application that are executed, developers are tasked with creating comprehensive tests to ensure the entire application is covered.
- Cost: IAST tools tend to be more expensive compared to SAST and DAST tools, which could make them less accessible for some organizations.
Differences between SAST and DAST include