What are Cybersecurity Incidents?
A cybersecurity incident is any event that compromises the confidentiality, integrity, or availability of an organization’s information systems. These incidents can range from malware infections to large-scale data breaches, affecting businesses of all sizes.
Common Types of Cybersecurity Incidents
- Malware Attacks: Malicious software designed to infiltrate and damage systems or steal data.
- Phishing Attacks: Deceptive emails or messages tricking users into revealing sensitive information.
- Denial-of-Service (DoS) Attacks: Flooding a system with traffic to disrupt services.
- Insider Threats: Employees or partners who intentionally or accidentally expose data.
Key Attack Vectors
Cybercriminals exploit various weaknesses to breach security defenses, including:
- Compromised Credentials: Stolen passwords or credentials obtained via phishing.
- Software Vulnerabilities: Unpatched software and zero-day exploits.
- Social Engineering: Manipulating individuals through impersonation, baiting, or pretexting.
What Is Cybersecurity Incident Response?
Cybersecurity incident response is the structured approach organizations take to detect, manage, and recover from security incidents. Think of it as a digital emergency plan that ensures quick action to minimize damage and protect critical systems.
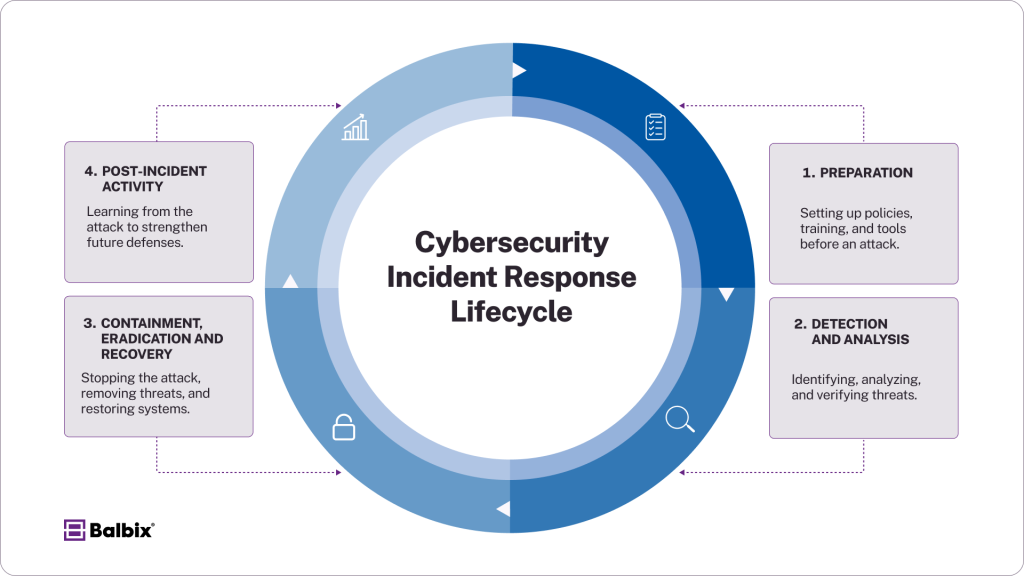
The Four Phases of Incident Response
- Preparation: Establishing policies, tools, and trained personnel.
- Detection & Analysis: Identifying threats and assessing their impact.
- Containment, Eradication & Recovery: Stopping the attack, removing threats, and restoring normal operations.
- Post-Incident Activity: Learning from the event to improve security defenses.
 We discuss each of these phases in detail later in this guide.
We discuss each of these phases in detail later in this guide.
Why Incident Response Is Essential for Organizations
The Rising Threat of Cyber Incidents
Cyberattacks are no longer rare occurrences—they’re an everyday challenge for businesses. In the past year alone, 39% of organizations reported experiencing a cyberattack. But the real concern isn’t just the frequency of attacks—it’s their impact. A single breach can lead to financial losses, reputational damage, and operational shutdowns.
Organizations risk chaos when a breach occurs without a structured incident response plan. Unclear responsibilities, delayed decision-making, and disorganized responses allow attackers to cause even greater harm. Beyond financial losses, a poorly managed response erodes customer trust and stakeholder confidence, leaving long-term damage. Finally, many regulatory and compliance frameworks mandate a documented and regularly tested Incident Response plan and will levy fines and prevent business if not followed.
The Competitive Advantage of Preparedness
A robust incident response plan mitigates risks and strengthens an organization’s reputation. Businesses that confidently assure clients, partners, and regulators of their cyber resilience gain a competitive edge. Proactive preparation signals trustworthiness and reliability, crucial factors in maintaining long-term relationships.
Beyond immediate containment, incident response drives strategic improvements. Post-incident analysis identifies:
- Weak points in security infrastructure
- Gaps in employee cybersecurity training & communication
- Emerging threats that need proactive mitigation
These insights create a stronger, more resilient cybersecurity posture, ensuring the organization is better prepared for future challenges.
The Importance of Incident Response
Business Continuity and Reputation Management
An effective cybersecurity incident response (CIR) plan ensures swift recovery from cyberattacks, minimizing downtime and financial losses. For example, the city of Mission, Texas, had to declare a state of emergency after a cyberattack disrupted essential services—highlighting the critical need for preparedness.
Cyber incidents also pose a serious reputational risk. Recent research has shown that more than half (58%) of consumers believe brands that get hit with a data breach are not trustworthy, and 70% would stop shopping with a brand that suffered a security incident. A well-executed response protects sensitive data and helps maintain customer confidence and brand credibility.
Regulatory and Compliance Considerations
Navigating regulatory requirements is crucial in cybersecurity incident response. Failure to comply with laws like GDPR and CCPA can lead to fines, reputational damage, and loss of trust.
For example, GDPR mandates breach notifications within 72 hours and requires informing affected individuals if their data is at risk, with fines of up to €20 million or 4% of global revenue. Similarly, the CCPA requires businesses to notify impacted consumers promptly, and individuals can sue for damages even without proof of harm. Emerging regulations, like the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), further complicate compliance.
Organizations facing multi-jurisdictional breaches must adhere to overlapping regulations (e.g., GDPR, CCPA, HIPAA) by adopting a unified incident response framework that incorporates data breach notification requirements, ensuring compliance during high-pressure situations.
The Cost of Poor Incident Response
The financial impact of a cyberattack is significantly higher for organizations without an effective response strategy. According to IBM’s Cost of a Data Breach Report, companies with strong incident response plans save an average of $2.66 million per breach compared to those without one.
Challenges in Incident Response: Common Pitfalls and How to Avoid Them
Even with a solid plan, incident response teams face challenges that hinder effectiveness. Recognizing these obstacles ensures continuous improvement.
- Unclear Roles and Responsibilities: In crises like a phishing attack, confusion over who handles specific tasks can delay response. To avoid this, create clear playbooks with defined roles and conduct regular tabletop exercises.
- Over-Reliance on Manual Processes: Relying on manual mitigation, such as scanning systems during a ransomware attack, slows response time. Automation tools like SOAR can quickly isolate infected systems or block malicious IPs, speeding up the process.
- Neglecting Communication: Poor communication, both internally and externally, can worsen reputational damage. Implement communication protocols and use pre-drafted templates to ensure timely, transparent notifications.
- Skipping Post-Incident Analysis: Focusing only on recovery without analyzing what went wrong misses valuable lessons. Regular post-incident reviews are essential for improving defenses and preventing future breaches.
Let’s detail how to build and execute an incident response team, plan, and processes.
Building an Effective Incident Response Team (IRT)
A strong Incident Response Team (IRT) is the backbone of an organization’s cybersecurity defense. When a cyber incident occurs, a structured and well-trained IRT ensures a swift, coordinated, and effective response to cybersecurity incidents. This minimizes downtime, reduces financial and reputational damage, and strengthens cyber resilience.
Key Roles and Responsibilities
An effective IRT consists of multidisciplinary experts who work together to manage incidents efficiently. Each role plays a critical part in mitigating cyber threats. Here are a few suggested team members, but the final list may vary depending on your organization and its unique needs and roles:
- Incident Response Manager: Oversees the response process, coordinates team actions, and ensures alignment with organizational policies.
- Security Analysts: Investigate and analyze security threats, assess vulnerabilities, and recommend remediation steps.
- IT Support & Engineering Teams: Provide technical remediation, restore affected systems and patch vulnerabilities.
- Legal Advisors & Compliance Officers: Ensure regulatory compliance with laws like GDPR, CCPA, and HIPAA while guiding the organization on legal risks.
- Public Relations & Communications: Manage external communications, ensuring clear messaging to customers, stakeholders, and the media.
Essential Skills and Training for an Incident Response Team
To effectively handle cyber incidents, an IRT must possess a diverse skill set, combining technical expertise, strategic thinking, and communication abilities. A single team member does not need to possess all necessary skills; collectively, all skills should be covered.
Core Skills Needed:
- Technical Proficiency: Deep understanding of network architectures, operating systems, cybersecurity tools, and threat intelligence.
- Analytical Thinking: The ability to assess attack patterns, perform forensic analysis, and implement effective mitigations.
- Crisis Management: Quick decision-making under pressure to contain threats and minimize damage.
- Communication & Reporting: Clear and concise reporting to executives, stakeholders, and regulatory bodies.
- Regulatory Knowledge: Familiarity with data protection laws and industry-specific compliance requirements.
Best Practices for Incident Response Training
Continuous training ensures that incident response teams remain prepared for real-world attacks. Leading organizations follow these best practices to enhance readiness:
- Regular Tabletop Exercises: Simulated attack scenarios that help teams refine response procedures and decision-making processes.
- Red-Team/Blue-Team Drills: Hands-on attack simulations where red teams (attackers) test defenses, and blue teams (defenders) respond in real-time.
- Quarterly Incident Response Training: Conducting training quarterly helps keep processes and skills top of mind and also allows for any changes or updates to be readily available.
- Cross-Department Collaboration – Ensuring IT, legal, PR, and leadership teams understand their roles in a crisis.
Phase 1: Developing a Comprehensive Incident Response Plan (IRP)
An Incident Response Plan (IRP) is an essential component for organizations aiming to safeguard against cyber threats. A well-structured IRP outlines the specific steps to take before, during, and after a security incident, ensuring a well-coordinated, effective response that minimizes damage and maintains business continuity.
Key Components of an Effective Incident Response Plan
A comprehensive IRP includes several key components, each of which plays a critical role in guiding teams through the incident response process. These components are vital to ensure an effective response to cybersecurity incidents:
1. Incident Classification and Response Protocols
Classifying incidents based on severity helps organizations prioritize responses. Different types of threats, such as ransomware, phishing, and internal data leaks, each require tailored response steps to ensure a swift and appropriate resolution.
2. Incident Severity Levels
Not every cybersecurity alert demands immediate attention. Categorizing incidents by severity levels ensures that resources are allocated efficiently and response actions are proportional to the impact. For example, a phishing attempt caught early may require minimal effort, while a full-scale ransomware attack demands urgent containment.
3. Communication Protocols
Clear communication is critical during a cybersecurity crisis. Internal communication ensures team members are aligned, while external communication with stakeholders, customers, and regulators helps maintain trust. Having pre-drafted communication templates, such as email templates for notifications or press releases, ensures timely and accurate messaging.
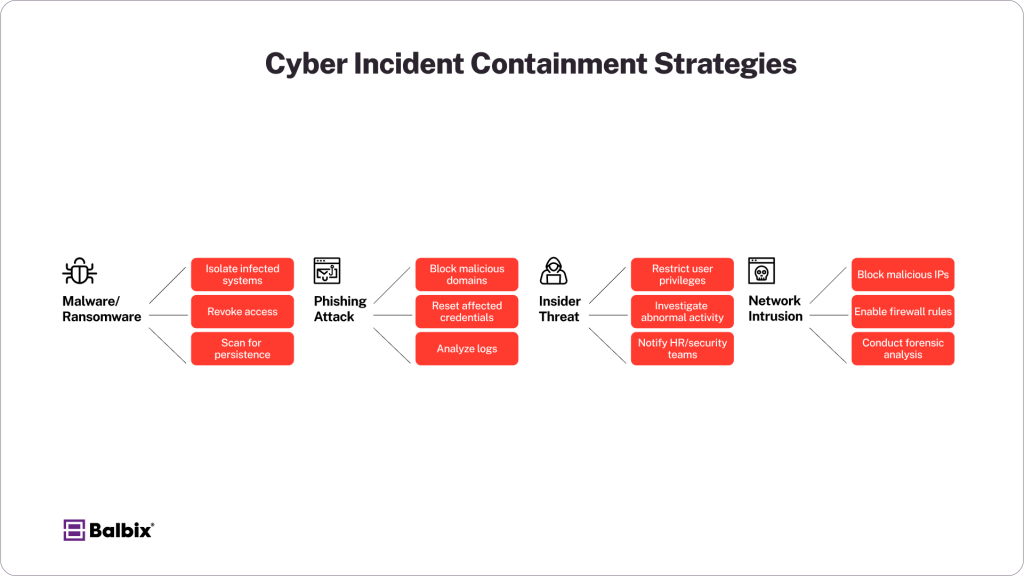
4. Containment Strategies
Once a threat is confirmed, containing the attack quickly is crucial to prevent further damage. Containment strategies should include short-term measures, such as disabling compromised accounts and blocking malicious IP addresses, and long-term measures like patching vulnerabilities.
5. Eradication and Recovery
Eradicating threats involves removing malicious code, deleting infected files, and applying patches. The recovery process includes restoring systems from clean backups, verifying system integrity, and resuming business operations.
Example Incident Response Frameworks
Several recognized frameworks can help organizations build a structured IRP. These frameworks guide all stages of the response process:
- NIST’s Computer Security Incident Handling Guide: A comprehensive approach to handling incidents that include preparation, identification, containment, eradication, recovery, and post-incident review.
- SANS Incident Response Process: A five-phase approach covering Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned.
Preparation: Building a Strong Foundation
Preparation is the cornerstone of an effective IRP. Without preparation, responding to a cyberattack is akin to fighting a fire without knowing where the hoses are. Here’s how you can prepare effectively:
- Create an Incident Response Playbook: This document should clearly define roles, responsibilities, and response steps for different types of incidents, such as ransomware, phishing, or insider threats. This “assembly guide” ensures your response team acts swiftly and efficiently when a crisis occurs.
- Conduct Regular Risk Assessments: Identify potential vulnerabilities and weaknesses in your infrastructure and systems, allowing your team to prepare accordingly.
- Stay Up-to-Date with Threat Intelligence: Review emerging threats regularly and update your playbook to account for evolving attack vectors.
For instance, during the SolarWinds supply chain attack, organizations with predefined incident response guidelines could quickly triage and isolate affected systems, minimizing the impact. Those without an IRP struggled to understand the attack vector, slowing their response and exacerbating the breach’s effects.
Continuous Review and Improvement
Preparation isn’t a one-time task—it’s an ongoing process. Regularly reviewing and updating your incident response playbook ensures your team is always ready to tackle new threats.
Effective preparation builds resilience, allowing organizations to respond quickly, reduce downtime, and minimize damage during cyberattacks. By investing in continuous improvement, organizations can enhance their response capabilities over time, ensuring they are always ready for the next cyber threat.
A comprehensive Incident Response Plan (IRP) is more than just a set of procedures—it’s a critical playbook that ensures your organization is prepared for any cyber crisis.
Phase 2: Incident Detection and Analysis
Effective incident detection and analysis are essential for minimizing the damage caused by cyberattacks. Rapid identification of a potential threat, followed by thorough analysis, can mean the difference between addressing a minor issue or managing a full-scale data breach.
Key Indicators of a Security Incident
Detecting a security incident begins with recognizing unusual activity in your systems. Common indicators include:
- Unusual login attempts or unauthorized access: Multiple failed login attempts or logins from unfamiliar locations may be reconnaissance activity or lateral movement attempts by bad actors.
- High outbound network traffic: Unusual spikes in traffic may indicate data exfiltration.
- Unexpected system behavior or slowdowns: Performance issues may signal the presence of malware or an ongoing attack.
Leveraging AI and Automation in Incident Detection
As cyber threats become more sophisticated, relying on traditional detection methods alone is no longer sufficient. AI-powered Security Information and Event Management (SIEM) solutions offer a powerful way to detect threats in real-time.
AI-powered threat detection tools analyze vast amounts of data, identifying patterns and anomalies that could signify an attack. These solutions help automate incident response actions, significantly reducing response times.
Efficient Detection and Analysis: Reducing Human Error
Once a threat is detected, it’s critical to conduct a thorough analysis to understand its scope and origins. This process typically involves using tools like intrusion detection systems (IDS) and log analyzers to trace the activity and identify patterns. With a well-defined incident response playbook, your team can follow predefined protocols for analyzing data efficiently, reducing the risk of human error and ensuring that each step is taken in the right order.
One common challenge during this phase is the occurrence of false positives—alerts triggered by non-incident activity. These false alarms can waste valuable time and distract teams from real threats. Integrating threat intelligence platforms can help address this.
These platforms combine data on known attacks with your organization’s internal information, prioritizing threats based on severity. This allows your team to focus on high-priority incidents, reducing the likelihood of missing a critical event.
Phase 3: Incident Containment and Eradication
Once a cybersecurity incident has been confirmed, the immediate priority is to contain the threat. Effective containment prevents attackers from moving laterally within the network, minimizing the potential damage. Whether it’s a ransomware attack, data breach, or insider threat, containing the incident quickly is crucial to protecting your organization’s assets and reputation.
Immediate Steps to Contain an Attack
Containing a cyberattack involves taking swift action to stop the threat from escalating. Immediate containment steps include:
- Disconnecting affected systems: Isolate infected devices from the network to prevent the spread of malware or unauthorized access.
- Applying firewall rules: Block malicious IP addresses to prevent further communication with the attacker.
- Resetting compromised credentials: Immediately reset passwords and enforce multi-factor authentication (MFA) to stop unauthorized access and limit the attacker’s control.
By taking these actions quickly, organizations can prevent the attack from spreading to other systems, reducing the overall impact.
Containment Strategies: Short-Term vs. Long-Term
Containment strategies can be broken down into short-term and long-term actions.
- Short-term strategies: These immediate measures are essential for stopping the attack in its tracks. They might include disconnecting affected systems, disabling compromised accounts, or blocking certain IP addresses.
- Long-term strategies: After the immediate threat is contained, the focus shifts to reinforcing vulnerabilities and strengthening the organization’s defenses to prevent future attacks. This could involve applying software patches, updating security protocols, and conducting thorough vulnerability assessments.
During this phase, it’s also critical to preserve forensic evidence for legal or compliance purposes. Collecting and securing evidence is vital for future investigations and helps ensure your organization meets legal obligations in case of a data breach.
Eradication: Removing the Threat
Once the threat is contained, the next step is eradication—removing all traces of the malicious activity to ensure the attack can’t recur. Eradicating the threat might include:
- Removing malicious code: Deleting or quarantining infected files, programs, or malware to prevent reinfection.
- Patching affected systems: Applying security patches to fix the vulnerabilities exploited by the attacker.
- Cleaning up network infrastructure: Ensuring that any compromised systems or software are restored to a clean state.
The incident response playbook we discussed above plays a key role here, providing specific steps and technical guidelines for the eradication process. Following these steps ensures that no malicious activity is overlooked, minimizing the risk of a recurring attack.
Containment and eradication are critical phases in the incident response lifecycle. The faster you contain the threat and eliminate the risk, the less damage your organization will suffer.
Phase 4: Post-Incident Recovery and Lessons Learned
The recovery phase of incident response focuses on restoring operations to normal while addressing the security vulnerabilities the attacker exploits. This phase is vital for recovering systems and rebuilding trust with stakeholders, customers, and partners. A strong recovery plan ensures the organization can bounce back quickly and effectively from a cyberattack, minimizing long-term consequences.
Recovery Steps: Restoring Systems and Securing Data
Recovery begins by restoring systems from backups and ensuring all affected systems are fully secure. Key recovery steps include:
- Forensic analysis: A thorough investigation to understand the attack vectors and the extent of the breach. This helps identify vulnerabilities and prevent similar incidents in the future.
- Implementing security patches: Applying patches to address the vulnerabilities exploited during the attack. This is critical in securing your infrastructure and preventing attackers from regaining access.
- Restoring data from clean backups: Ensure all critical data is restored from secure, unaffected backups. Verifying the integrity of data before restoration is essential to prevent the introduction of malicious files or malware.
Reflection and Continuous Improvement
The recovery phase is also an opportunity to learn from the incident. Reflecting on the attack helps organizations understand what went wrong and how to improve. Post-incident reviews should focus on the following:
- Identifying weaknesses in the incident response process, infrastructure, or employee training.
- Updating the incident response playbook: Lessons learned from the breach should be integrated into the incident response plan (IRP) to improve future readiness.
- Strengthening defenses: Organizations that continuously improve their security posture based on past incidents reduce the risk of future attacks.
The Importance of Regular Updates
Recovery isn’t a one-time event; it’s an ongoing continuous improvement process. Updating your IRP based on lessons learned from each incident is crucial for adapting to the evolving cybersecurity landscape. A dynamic, regularly updated recovery plan ensures that your organization remains agile and prepared to respond to future cyber threats quickly and effectively.
Tools and Technologies for Effective Incident Response
Incident Detection Tools
Early threat detection is essential for effective incident response. Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools play a key role by aggregating logs and identifying unusual activity.
For example, an SIEM tool flagging unusual file access during non-working hours helps teams detect insider threats or compromised accounts. Endpoint Detection and Response (EDR) tools like CrowdStrike Falcon and SentinelOne offer visibility into endpoint activities, enabling proactive monitoring.
AI-driven detection tools are also on the rise, utilizing behavioral analysis to identify anomalies in real time. For instance, Darktrace uses self-learning AI to detect network traffic anomalies, significantly reducing detection times.
Forensic Analysis Tools
Once an incident is contained, forensic tools like EnCase and FTK are essential for investigating the root cause. These tools analyze logs, files, and system artifacts to trace an attacker’s steps without damaging original data. In data breaches, they help determine if sensitive information was accessed or exfiltrated, supporting regulatory compliance.
Additionally, memory analysis tools like Volatility are used to detect advanced attacks such as fileless malware, which operates entirely in memory, evading traditional detection methods.
Automation in Incident Response
With the increasing complexity of cyberattacks, automation is vital. Platforms like Palo Alto Networks Cortex XSOAR and Splunk SOAR streamline containment and remediation tasks. For example, an automated system can isolate infected systems and block malicious IP addresses in seconds, preventing further spread.
Machine learning (ML) enhances automation by learning from past incidents to predict vulnerabilities and attack vectors. For example, Microsoft Sentinel uses behavioral analytics to identify threats that rule-based systems may miss.
Conclusion
Effective incident response is critical to minimizing damage, restoring operations, and strengthening security posture.
Addressing key challenges, such as unclear roles, overreliance on manual processes, and communication breakdowns, can help organizations respond more efficiently and reduce risk. Leveraging the right tools, frameworks, and continuous improvement strategies ensures a swift, coordinated response.
Balbix can help enhance your incident response by providing actionable insights, streamlining automation, and supporting continuous risk assessment. With Balbix, your team can stay ahead of cyber threats and respond confidently, minimizing any impact of any security incident.
Frequently Asked Questions
- What is the main goal of cybersecurity incident response?
-
The primary goal of cybersecurity incident response is to detect, contain, and mitigate security threats to minimize damage, ensure business continuity, and prevent future incidents. A well-structured incident response plan helps organizations respond quickly and effectively to cyberattacks.
- What are the key steps in an incident response plan?
-
A cybersecurity incident response plan typically follows four key phases: Preparation, Detection & Analysis, Containment, Eradication & Recovery, and Post-Incident Activity. These steps help organizations manage security incidents efficiently and improve their defenses over time.
- Why is incident response important for businesses?
-
Incident response is crucial because cyberattacks can lead to data breaches, financial losses, reputational damage, and regulatory penalties. A strong incident response plan reduces downtime, protects sensitive data, and ensures compliance with frameworks like GDPR and CCPA.
- What tools help with cybersecurity incident response?
-
Organizations use various tools for incident response, including Security Information and Event Management (SIEM) solutions, Endpoint Detection and Response (EDR) platforms, Security Orchestration, Automation, and Response (SOAR) tools, and threat intelligence feeds to detect, analyze, and mitigate cyber threats efficiently.
- How can companies improve their cybersecurity incident response?
-
To strengthen cybersecurity incident response, businesses should conduct regular risk assessments, perform tabletop exercises, invest in incident response automation, and continuously update their response plans based on evolving threats. Training employees and fostering a security-first culture also play a critical role in reducing cyber risks.


