Security teams today face an enormous challenge. Thousands of vulnerabilities are discovered in enterprise environments yearly, and new threats emerge almost daily. With limited resources, fixing every issue is impossible. The key to truly reducing risk is how an organization structures its vulnerability prioritization strategy.
Understanding how to choose the right vulnerability prioritization solution is essential for CISOs, security analysts, and IT managers. This guide will explain the importance of prioritization, what to look for in a platform, and how to integrate it into your long-term cybersecurity strategy.
What Is Vulnerability Prioritization?
Vulnerability prioritization is the practice of ranking identified weaknesses based on their likelihood of exploitation and potential impact on the business. Instead of trying to fix everything, security teams focus on the vulnerabilities that matter most.
Below is a comparison chart comparing vulnerability prioritization to more traditional methods:
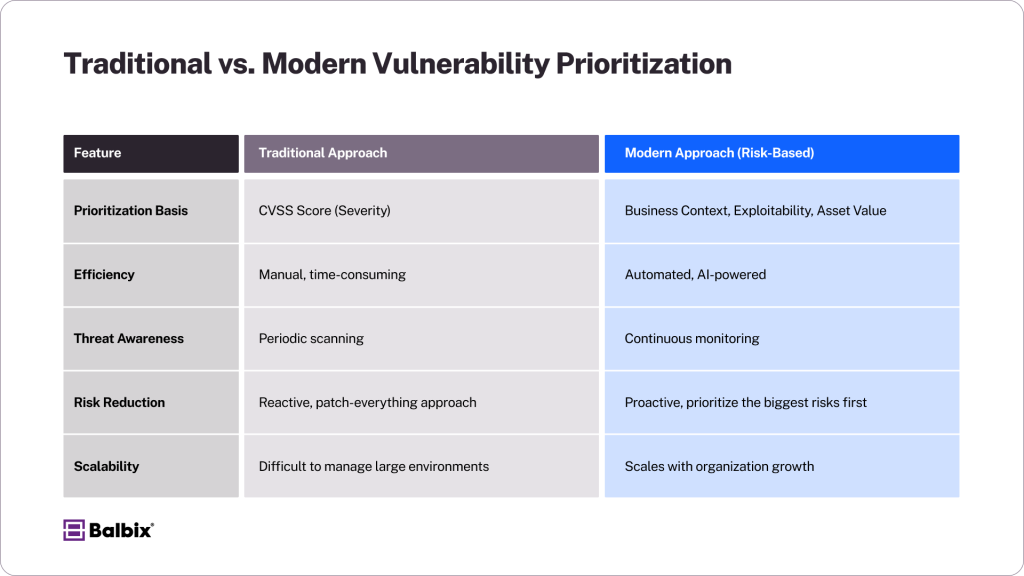
The Importance of Vulnerability Prioritization
Traditional vulnerability management approaches often use severity scores as a baseline to address issues. However, this doesn’t always reflect the actual risk to your organization since the scores lack context around asset criticality & existing security controls. Instead of reactive, resource-intensive firefighting, prioritization allows you to:
- Reduce high-impact risks before they are exploited.
- Protect critical assets, such as customer data or network operations.
- Use resources efficiently, saving hours of manual investigation and unnecessary patching efforts.
Benefits of Effective Vulnerability Prioritization
- Enhanced Risk Management: Take a proactive approach to identifying and addressing vulnerabilities that pose the greatest threats to your systems and data. By prioritizing the most critical risks, you can minimize potential damage and ensure your organization is better prepared.
- Improved Efficiency: Streamline your workflows by concentrating on high-value tasks that contribute to your overall goals. Avoid wasting time and resources on low-priority or irrelevant issues, allowing your team to focus on what truly matters.
- Stronger Resilience: Develop a robust and proactive cybersecurity strategy that fortifies your critical systems against potential breaches. By staying ahead of threats, you can reduce downtime, prevent financial losses, and maintain trust with your stakeholders.
Key Considerations When Evaluating a Vulnerability Prioritization Solution
Choosing the right vulnerability management solution is critical to strengthening your organization’s security posture. An effective solution identifies vulnerabilities and helps you focus on what truly matters, improving efficiency and reducing risk. Here’s what you need to keep in mind when making your decision:
1. Risk-Based Approach
Not all vulnerabilities carry the same level of urgency. A strong solution should go beyond surface-level severity scores and prioritize vulnerabilities based on real, contextual risk to your organization. This means focusing on factors such as:
- Asset Importance: Does the vulnerability impact a highly sensitive or business-critical system? For example, a flaw in your payment processing system may be more urgent than one in a test server.
- Exploitability: Is the vulnerability actively being exploited in the wild, or is it likely to become a target soon? Platforms that utilize threat intelligence can provide valuable insights here.
- Business Context: Does resolving this vulnerability align with your organization’s broader risk management goals? For instance, fixing an issue in alignment with a high-priority compliance objective may take precedence over other tasks. A good solution will help align vulnerability management with overall business objectives.
2. Automation & Scalability
Manual vulnerability management is slow, error-prone, and inefficient, especially as organizations grow. To streamline your processes and handle growing workloads, ensure your platform includes:
- Automated triage workflows to remove repetitive tasks and allow your team to focus on strategic efforts.
- Seamless integrations with existing tools such as SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation, and Response), and endpoint protection software. These integrations ensure that your vulnerability management fits seamlessly into your overall security ecosystem.
- Scalability to support enterprise environments, ensuring the solution can handle large, complex infrastructures without performance issues. A solution that grows with your organization is essential for long-term success.
3. Real-Time Data and Insights
Relying on outdated information can leave you exposed to emerging threats. A good vulnerability management platform should provide:
- Continuous updates to ensure prioritized vulnerabilities reflect the most current threat landscape. This means accessing the latest intelligence on active exploits, zero-day vulnerabilities, and emerging attack patterns.
- Real-time monitoring to alert teams to new risks as they arise, reducing the window of exposure and allowing for quick remediation. This feature is particularly crucial for organizations facing rapidly evolving threats.
- Analytics and trend reporting to give insight into your organization’s vulnerability management performance over time, helping you identify areas for improvement and measure progress.
4. Ease of Use
A vulnerability prioritization solution should enhance productivity, not add complexity. It must be intuitive and accessible for all stakeholders, from technical teams to executives. Look for features like:
- Intuitive Dashboards: Clear, user-friendly visuals that make it easy to track, rank, and report vulnerabilities at a glance. The ability to customize views based on user roles further simplifies workflows.
- Customizable Reports: Tailored outputs suited to different audiences, such as technical details for IT teams, high-level summaries for executives, and compliance-focused reports for audit committees.
- Quick Deployment and Onboarding: A solution that is easy to set up and integrates smoothly into your existing environment ensures faster adoption by your team.
5. Compliance Support
With regulatory frameworks such as SOC 2, ISO 27001, PCI-DSS, and NIST serving as standards benchmarks for organizations, robust compliance support is a must-have feature. The right platform should:
- Help maintain compliance through features such as automated reporting and documentation that align with regulatory frameworks.
- Simplify audits by providing built-in tools for tracking and recording remediation efforts, ensuring you can demonstrate your security practices clearly and efficiently.
- Track compliance status in real-time so you can quickly identify and address gaps before they become issues.
Must-Have Features to Look For In a Vulnerability Prioritization Solution
When evaluating different tools for your organization, it’s essential to prioritize solutions that offer advanced capabilities, going beyond the basics to deliver real value. Here are some key features to focus on:
AI-Powered Risk Quantification
Look for tools with AI capabilities that identify vulnerabilities and calculate the real business risks associated with them. This allows you to prioritize threats based on their potential impact on your organization, ensuring smarter and faster decision-making.
Integration Capabilities
The tool should integrate seamlessly with your existing security infrastructure, such as SIEM platforms, endpoint management systems, and other critical tools. This ensures that the tool enhances your current workflows without causing disruptions or requiring redundant processes.
Multi-Metric Prioritization Framework
Effective tools should evaluate vulnerabilities using a more robust framework instead of solely on numerical CVSS scores. This framework should include factors like exploitability, business context, asset criticality, and potential harm to your organization, providing a more comprehensive risk assessment.
Centralized Visibility
A unified, easy-to-use dashboard is crucial for managing vulnerability prioritization, setting resolution deadlines, and tracking progress. This centralized view streamlines workflows reduces oversight, and ensures all team members are aligned on priorities and objectives.
Questions to Ask Vendors Before Choosing a Tool
Engaging directly with vendors is a vital step before committing to any solution. A clear understanding of how a platform aligns with your specific needs can save time, money, and potential setbacks in the future. To make an informed decision, consider asking the following questions:
- How does this tool prioritize vulnerabilities specific to my business model? Understanding how the platform tailors its approach to your industry and unique challenges is critical to ensuring effective protection.
- Does it integrate with our current security stack? Seamless integration with your existing tools and systems minimizes disruption and ensures a more streamlined workflow.
- How often does it update vulnerability intelligence? Frequent updates are essential to staying ahead of emerging threats and maintaining robust security measures.
- What scalability options are available for future organizational growth? As your business grows, the platform must be able to adapt and handle increased demands without compromising performance.
- How does the platform handle compliance requirements for audits and reporting? Meeting industry regulations and ensuring audit readiness are key to avoiding legal issues and maintaining trust with stakeholders.
Asking these questions and carefully evaluating the answers will give you confidence in the platform’s ability to address both your current and future security needs, ensuring your investment is a strategic one.
From Prioritization to Prediction: The Next Leap in Vulnerability Management
Vulnerability prioritization has evolved rapidly—but the next frontier is prediction.
Modern enterprises can no longer afford to wait until vulnerabilities are published, scored, and triaged. AI-native platforms like Balbix are redefining this process by predicting which exposures are likely to be exploited next, weeks before attackers act.
Here’s how predictive vulnerability management transforms outcomes:
- AI-Driven Forecasting: Balbix analyzes billions of signals—from exploit feeds, code patterns, and attack behaviors—to forecast which vulnerabilities will trend next.
- Contextual Correlation: It automatically links vulnerabilities to assets, controls, and business impact, helping teams act before the window of exploitation opens.
- Explainable Decisions: Through the Balbix BIX assistant, analysts can ask, “Why is this vulnerability high-risk?” and get transparent, defensible reasoning for every prioritization.
- Continuous Learning: Each remediation improves model accuracy, allowing prioritization to get sharper, faster, and more adaptive over time.
The shift from reactive to predictive prioritization doesn’t just reduce noise—it changes how organizations defend. It means fewer surprises, faster action, and measurable risk reduction that scales with your environment.
The Role of Vulnerability Prioritization in Long-Term Cybersecurity Strategy
A strong vulnerability prioritization solution goes beyond simply patching high-risk issues. It becomes a key pillar in building a long-term cybersecurity strategy by:
- Proactively Reducing Risks: Security teams get ahead of exploits rather than simply reacting to them.
- Preventing Financial Damage: Costly breaches are less likely when high-risk vulnerabilities are identified and resolved before they are exploited.
- Fostering Collaboration: A good platform aligns IT, security, and business leaders under one risk management approach.
By integrating vulnerability prioritization into your overall strategy, you can create a more resilient posture for your organization.
Take the Next Step with Balbix
If you’re ready to move beyond basic vulnerability management, Balbix provides the advanced tools you need to strengthen your security posture.
With AI-powered risk quantification, you can focus on the vulnerabilities that truly matter, while real-time insights keep you updated on evolving threats through continuous monitoring. Seamless integrations ensure Balbix connects effortlessly with your existing SIEM, patch management, and endpoint tools, and compliance-ready reporting simplifies audits and regulatory alignment.
Don’t wait for minor vulnerabilities to escalate into major breaches—request a demo today and see how Balbix enhances risk prioritization across your organization.
Frequently Asked Questions
- What is vulnerability prioritization, and why is it important?
-
Vulnerability prioritization is the process of ranking security weaknesses based on their likelihood of exploitation and potential business impact. It helps organizations focus on the most critical vulnerabilities first, reducing risk efficiently and preventing resource overload on low-priority issues.
- How does risk-based vulnerability prioritization differ from traditional methods?
-
Traditional vulnerability management often relies on severity scores (e.g., CVSS) without considering real-world exploitability or business impact. Risk-based vulnerability prioritization incorporates asset importance, active exploit activity, and compliance requirements, ensuring security teams first address the most pressing threats.
- What features should I look for in a vulnerability prioritization solution?
-
An effective vulnerability prioritization solution should include AI-powered risk quantification, automation for scalability, real-time threat intelligence, seamless integrations with existing security tools, and compliance tracking to support audits and regulatory requirements.
- How can automation improve vulnerability prioritization?
-
Automation helps security teams streamline the vulnerability management process by automatically categorizing, scoring, and prioritizing threats. This reduces manual effort, minimizes human error, and ensures faster response times to high-risk vulnerabilities.
- How does vulnerability prioritization fit into an overall cybersecurity strategy?
-
Vulnerability prioritization is a key pillar of cybersecurity strategy, enabling organizations to proactively manage risks, prevent breaches, improve operational efficiency, and maintain regulatory compliance. By integrating it with continuous monitoring and risk management practices, businesses can strengthen their security posture long-term.


