Many of my friends know that I work for a security company, and every once in a while I will get a question that goes like: “Hey Vinay– this thing called SambaCry, should I be worried?”
For the most part, the question comes from someone who is a business leader, entrusted with some level of corporate responsibility, and who is often technically savvy, but feels lost or overwhelmed in the constantly changing world of security attacks and jargon. As business people, they also have a simple emotional response to all of the daily cyber-security related stimuli– what is my risk?
Let’s talk about SambaCry…
Increasingly, attackers are infecting IoT NAS devices, servers and workstations by exploiting a 7-year-old critical remote code execution vulnerability within Samba networking software. Once breached, hackers take full control of these assets remotely—a nightmare scenario for organizations across the globe. The folks over at F5 have a good writeup on SambaCry. SambaCry is a “cousin” of the famous wannacry malware that recently got a lot of press.
How can your enterprise proactively assess risk for SambaCry and take mitigation steps to prevent an attack? The risk of SambaCry is unfortunately specific to your environment– there is no one answer for everyone. You need to do this calculation yourself, taking into account knowledge of your network and organization.
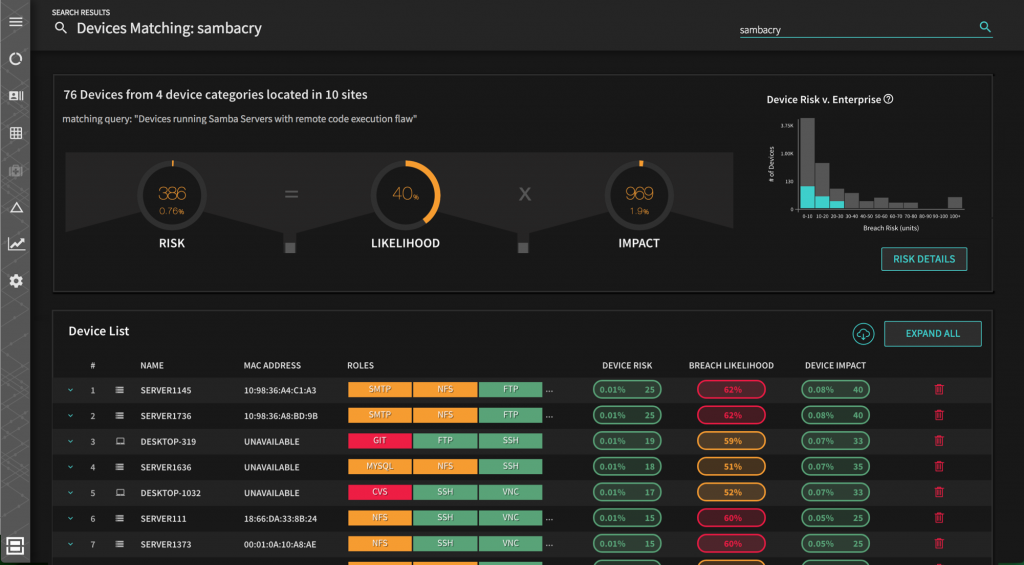
Get started: discover your attack surface
Understanding that your digital attack surface is vast, hyper-dimensional and rapidly increasing is the first step in warding off an attack. Given the proliferation of devices and applications connected to your network, a propagation point of entry for SambaCry can exist just about anywhere on your network — including (mostly unmanaged) assets such as opaque NAS devices and Cloud servers.
Locating for a specific set of system vulnerabilities along hundreds of risk dimensions in your extended network requires a systematic and deliberate approach. Here’s how:
- Understand the specific vectors that SambaCry uses to attack your network, gain a toehold, and then propagate across your network (yes, you must do this).
- Analyze your enterprise network activity and identify all assets that are running Samba. This might be Linux servers, or appliances and cloud services running some flavor of Linux and Samba.
- Uncover information about the active Samba versions by examining network behavior and configuration, and narrow down the list of assets running vulnerable versions of Samba.
- Categorize vulnerable assets according to type of device — server, workstation or an IoT NAS device. These distinctions will help you define and prioritize your mitigation actions accordingly.
Next: calculate likelihood and business impact of SambaCry
After discovering your attack surface, you need to identify those assets that are most susceptible to an attack due to various factors such as Internet connectivity, password hygiene, and so on. Next, examine your network traffic activity (and traffic history) for each asset to determine the likelihood of an external adversary gaining access to the targeted device and dropping a malicious Samba payload.
Additionally, you must evaluate the business impact of relevant devices to prioritize mitigation actions for assets that pose a high risk to your enterprise. Essentially, you need to sort your various systems vulnerable to SambaCry in order of importance to your business. As your business changes you must do this calculation again, and you must understand the intricate details of how your business systems rely on your infrastructure pieces.
Now you are ready to start looking at these systems in order of business risk, and applying whatever updates or fixes that may be applicable. Clearly, since time is of the essence, you want to mitigate risk to your most important systems first, and lesser systems later, if you have time.
Go further: assess risk from variants of SambaCry
Given the success of SambaCry, it is inevitable that new malware variants will emerge that seek to target similar or parallel Samba vulnerabilities. To assess your risk for similar malware and avoid costly triage efforts, repeat the steps listed above for all existing versions of Samba deployed in your enterprise and across every known set of vulnerabilities present within those versions.
How many variants are possible? I don’t know…
Vinay – is this a joke? Do you really want me to do this?
Yeah right! This is how you estimate your risk from SambaCry.
As you might imagine, this systematic approach is not practical for most people. Maybe JP Morgan Chase has enough money and people to proactively understand variants of XYZ attack that has happened and is about to happen. There are too many moving parts in your network, and too many dimensions of risk to do this risk calculation by hand.
This is why we started Balbix!
Let’s make it easy: automated and continuous risk assessment from Balbix
Balbix’s predictive breach risk platform continuously and automatically discovers and categorizes every asset connected to your network, making it simple to assess threats like SambaCry, and proactively calculate the likelihood of compromise across hundreds of attack vectors. Balbix also determines the business impact for each device, app and user, making uncovering your specific business risk and figuring out what you need to do to defend your enterprise against attacks as simple as typing a search query in Balbix, for example: “breach risk from SambaCry” or more “what’s my risk from ShadowBrokers”.
Now how easy it that?
In fact, Balbix will continuously watch what’s going on in your network and offer tactical and strategic prescriptions to improve your resilience– these are very specific and actionable things you can do. We try hard to give you the capabilities of dozens of security experts and powerful automation, as your personal assistant.
Happy to demo anytime.