March 18, 2023
Microsoft disclosed a Microsoft Outlook Vulnerability (an RCE – remote code execution) titled “Microsoft Outlook Elevation of Privilege Vulnerability” and designated as CVE-2023-23397 with its patch Tuesday release (March 14th 2023).
This vulnerability is an elevation-of-privilege (EoP) vulnerability in Microsoft Outlook. This means that when the vulnerability is exploited the application gains rights or privileges that should not normally be available to it. In this instance, this increased privilege could allow an attacker to obtain the victim’s password hash.
This vulnerability is being highlighted due to the ease of its exploit and wide usage of Outlook and Office.
Background
The vulnerability identified by CVE-2023-23397, has been patched by Microsoft on 14 March, 2022 with it’s Patch Tuesday releases. This was originally identified in cooperation with CERT-UA (the Computer Emergency Response Team for Ukraine). This vulnerability, according to Microsoft, has been used in attacks to target and breach the networks of fewer than 15 Russian and EU government, military, energy, and transportation organizations between mid-April and December 2022.
How It Works
The exploit for this vulnerability is triggered when an attacker sends a specially crafted email using an extended MAPI (Microsoft Outlook Messaging Application Programming Interface) property containing the UNC (Universal Naming Convention) path of an attacker-controlled SMB (Server Message Block) share (running on TCP port 445).
When the victim’s Outlook client receives the malicious message, it attempts to authenticate itself to the attacker controlled SMB share using the victim’s NTLM (New Technology Lan Manager, Windows’ Challenge/Response Authentication mechanism) hash. It is at this point that the victim’s NTLM hash is stolen. This hash could then be used for authentication to other systems within the victim’s network, thus allowing lateral movement within the environment by the attacker.
This is not a new exploitation methodology, specifically, it is one known as an NTLM Relay Attack. A very thorough examination of how NTLM Relay attacks work has been posted by security blogger “pixis”.
MAPI and the Vulnerable Parameter Exploited
“MAPI provides the messaging architecture for Microsoft Outlook 2013 and Outlook 2016, MAPI for Outlook provides a set of interfaces, functions, and other data types to facilitate the development of Outlook messaging applications. Applications and transports use MAPI to manipulate email data, to create email messages and the folders to store them in, and to support notifications of changes to existing MAPI-related data.”
(Reference: Learn More About Outlook MAPI Reference on Microsoft Docs)
Specifically for this vulnerability (CVE-2023-23397)the ExtendedProperty MAPI parameter that is used for the exploit is the “PidLidReminderFileParameter” property. This property is used to specify the audio file name that should be played by an Outlook client when a reminder becomes overdue for a specific object. As this property can accept a filename, it is possible that the file name could be a UNC path causing NTLM authentication to be triggered and thus the beginning of the exploitation of the vulnerability. It has also been suggested in various discussions that the parameter “task.file.msg_data.reminderFileParameter”, may be used to trigger this exploit as well.
Direct Microsoft Links to Microsoft Fixes
The vulnerability can be remediated through Microsoft provided patches which can be obtained in several ways:
| Outlook / Office Version | Microsoft KB Article (fix) |
| Microsoft Outlook 2016 (32-bit edition) | 5002254 |
| Microsoft Outlook 2016 (64-bit edition) | 5002254 |
| Microsoft Outlook 2013 Service Pack 1 (32-bit editions) | 5002265 |
| Microsoft Outlook 2013 Service Pack 1 (64-bit editions) | 5002265 |
| Microsoft Outlook 2013 RT Service Pack 1 | 5002265 |
| Microsoft Office 2019 for 32-bit editions | See Release Notes |
| Microsoft Office 2019 for 64-bit editions | See Release Notes |
| Microsoft 365 Apps for Enterprise for 32-bit Systems | See Release Notes |
| Microsoft 365 Apps for Enterprise for 64-bit Systems | See Release Notes |
| Microsoft Office LTSC 2021 for 32-bit editions | See Release Notes |
| Microsoft Office LTSC 2021 for 64-bit editions | See Release Notes |
Mitigation Strategy if Patching is Not Possible
If patching is not immediately possible, Microsoft suggests adding users to the Protected Users group in Active Directory and blocking outbound SMB traffic on TCP port 445. These measures may help to limit the impact of the CVE-2023-23397 vulnerability.
Vulnerability Exposure Detection
To determine if your organization was targeted by actors attempting to use this vulnerability, Microsoft is providing documentation and a script for detection at Microsoft’s Script Documentation for CVE-2023-23397. The script is designed to scan emails, calendar entries, and task items and to verify if they have the exploitable property. The script allows administrators to locate elements in their environment that have this exploitable property and subsequently remove them or delete them permanently.
Balbix Detection and Risk Identification
Balbix vulnerability and risk platform continuously identifies and prioritizes any new vulnerabilities in your environment. With this, our customers can not only detect the assets vulnerable to this CVE, but quickly identify in one place the CVE data metrics, affected assets, affected software, appropriate remediations/mitigations, threat information and the priority of resolution.
This enables remediation teams to confidently focus on deploying fixes that will reduce the greatest amounts of risk in their environments at high velocity.
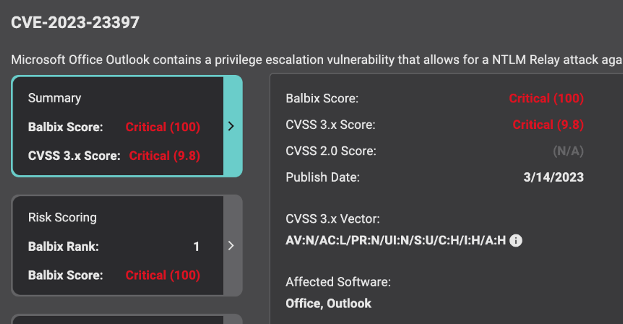
CVE Details
A quick summary provides complete details of the raw CVSS scoring and attack vector data, as provided by NVD (National Vulnerability Database) and Microsoft.
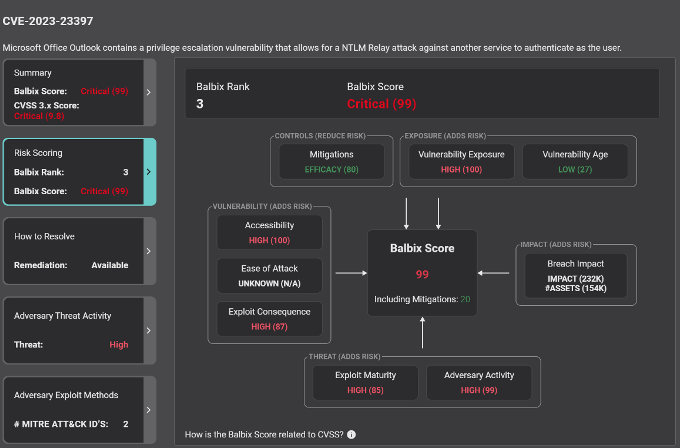
Vulnerability Manifestation and Analysis
Balbix provides an analysis of the CVE relevant to the customer-specific environment. Balbix uses five general categories to create the environment specific risk score for this CVE. This risk score factors in security controls in place (Controls), the exposure of the vulnerability at large (Exposure), the specific properties of the CVE (Vulnerability), the adversary activity related to the vulnerability (Threat) and the business context (Impact) of the assets that are affected.
This enables an accurate and actionable understanding of how this manifests itself in your environment.
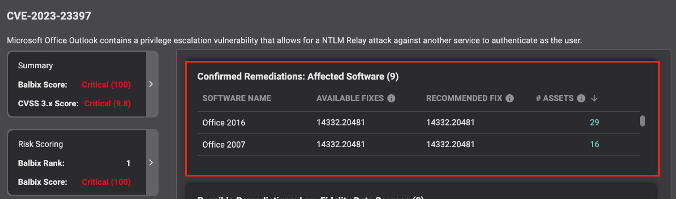
Get accurate and actionable remediation Information
Balbix also provides complete and comprehensive information on how to resolve the vulnerability within your environment. It includes specific Software and Versions affected, links to any patches available as well as an analysis of how broad the exposure is within your environment in terms of number of assets.
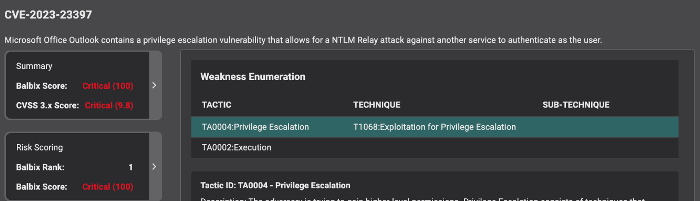
Be confident about your analysis, and prioritization with automated MITRE ATT&CK mapping
Utilizing the MITRE ATT&CK® enumeration, Balbix will map the CVE to the relevant weakness enumeration. MITRE ATT&CK® is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations.