

April 30, 2024
In the chaotic and ever-changing world of cybersecurity, the line between a good Chief Information Security Officer (CISO) and a top-tier one often boils down to one crucial skill: ruthless prioritization. But how do these elite CISOs navigate the complex landscape of cyber threats and operational demands with such precision?
Enter the Eisenhower Decision Matrix, a timeless tool for time management and prioritization attributed to General and US President Dwight D. Eisenhower. This matrix, also known as the Urgent-Important Matrix, serves as a guiding principle for leaders, including CISOs, to discern between tasks that demand immediate attention and those that can wait.
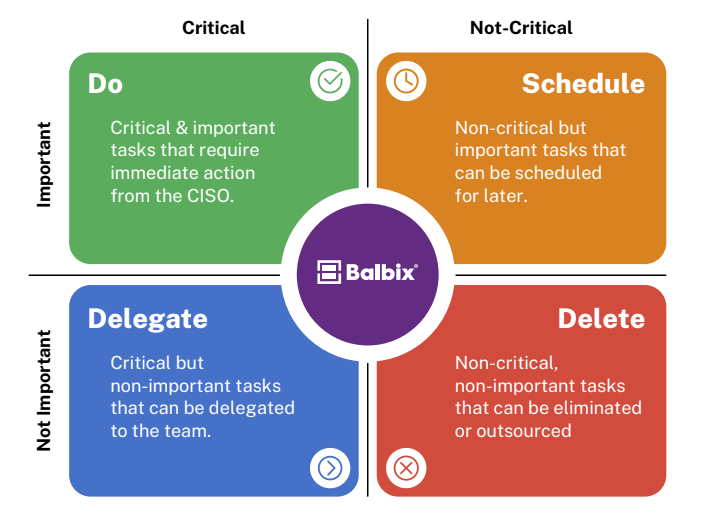
The top quadrant of the matrix, for example, represents tasks that are both urgent and important, requiring immediate action. In our recent survey of Fortune 1000 CISOs, we asked: What activities demand urgent attention for an effective cyber risk management program?
These findings underscore the critical nature of immediate action and personal oversight by CISOs in the face of active threats and compliance requirements. Responding to breaches showcases the necessity of swift, decisive action to mitigate damage, while the emphasis on board reports and SEC filings highlights the strategic aspect of the CISO role.
At Balbix, we understand the urgency of these high-priority tasks. That’s why we enable CISOs to quickly address them by:
Please check out our eBook for insights into the other quadrants from our survey.