
June 14, 2023
As technology relentlessly progresses, we witness a continuous stream of newer, more innovative tools replacing their antiquated counterparts. Rotary phones gave way to smartphones, not just replacing a dial with a touch screen, but fundamentally altering how we communicate, work, and entertain ourselves. The replacement of cathode ray tube monitors with flat-screen LED monitors signified an improvement not just in aesthetics, but also in the clarity and quality of the viewing experience. Similarly, the journey from floppy disks to USB drives, and eventually to cloud storage, wasn’t just about offering larger storage spaces, but enhancing data safety and providing universal access. Each of these shifts is a testament to the fact that technological evolution is not solely about obsolescence and replacement, but also about an escalation in customer value.
This principle extends to the realm of cybersecurity as well. The process of maturity here isn’t simply about discarding the old to embrace the new, but about elevating the efficacy and value of our cybersecurity posture. Cutting-edge innovations in cybersecurity aren’t just about novel tech, they are about improving our defenses, increasing their robustness, and providing solutions that seamlessly integrate into our digital ecosystems.
As organizations continue to grow and evolve, managing cybersecurity has become a complex and daunting task. The increasing complexity of IT environments, as organizations become more digitally interconnected along with the massive adoption of cloud technologies, has made managing cybersecurity risks with traditional methods challenging.
In this blog, we’ll guide enterprises in evaluating their position on the cybersecurity maturity curve. Furthermore, we’ll illuminate the path toward a more advanced, data-driven, and automated cybersecurity posture.
Despite a wide range of cybersecurity tools available today, organizations still struggle to manage their cybersecurity risks due to a fragmented and disjointed approach. We’ve observed our customers, including Fortune 100 and large enterprises, facing several issues:
As is evident from the list of issues, the fragmented nature of the current cybersecurity landscape, which creates significant obstacles in addressing threats, necessitates a radical transformation. This shift begins by taking a critical look at the existing cybersecurity infrastructure and identifying areas for improvement and eliminating redundancies to enhance overall efficiency and effectiveness. Drawing from our detailed observations from working with our customers, we discovered that it’s a journey of maturity, moving from a disjointed approach to a consolidated, strategic one – a journey that can be guided by a maturity model. But what are the implications when organizations, in their pursuit of maturity, excessively rely on familiar tools instead of seeking out the most effective solutions?
The cybersecurity market is indeed crowded and noisy, with many organizations overly-dependent on familiar tools. This tendency aligns with the principle of Maslow’s hammer. This cognitive bias makes individuals resort to tools they’re most familiar with or those easily accessible, irrespective of their aptness or effectiveness for the ongoing task. In cybersecurity, this manifests as organizations favoring the use of trusted tools to tackle emerging challenges without exploring potentially more effective alternatives.
A related compounding issue is the tendency to approach cybersecurity as a series of isolated projects rather than as a unified strategy. Organizations often find themselves with a cybersecurity posture that is a mishmash of point products, each designed to address a specific security ‘project.’ This project-oriented approach often lacks insight into the overall impact on the organization’s security posture. As a result, teams deploy products from various vendors without realizing the limited overall security improvement these point solutions offers. The interoperability issues between these disparate tools further intensify the fragmentation of cybersecurity efforts.
Our findings indicate that adopting a strategy of tool consolidation is both effective and essential in optimizing the efficiency and effectiveness of cybersecurity programs. By consolidating different cybersecurity point products, organizations can achieve improved visibility, streamlined processes, and more efficient responses to threats and vulnerabilities. Moreover, consolidation results in cost savings, simplified management, increased agility, and a proactive security stance. Overall, the benefits of tool consolidation make it a strategic approach for organizations looking to enhance their cybersecurity posture.
To embrace a successful journey, it’s important to know where you are starting from and where you’re going. As a security leader, this principle applies to improving your organization’s security posture. To help identify the next steps forward, here’s a simple and actionable maturity model that CISOs can leverage.
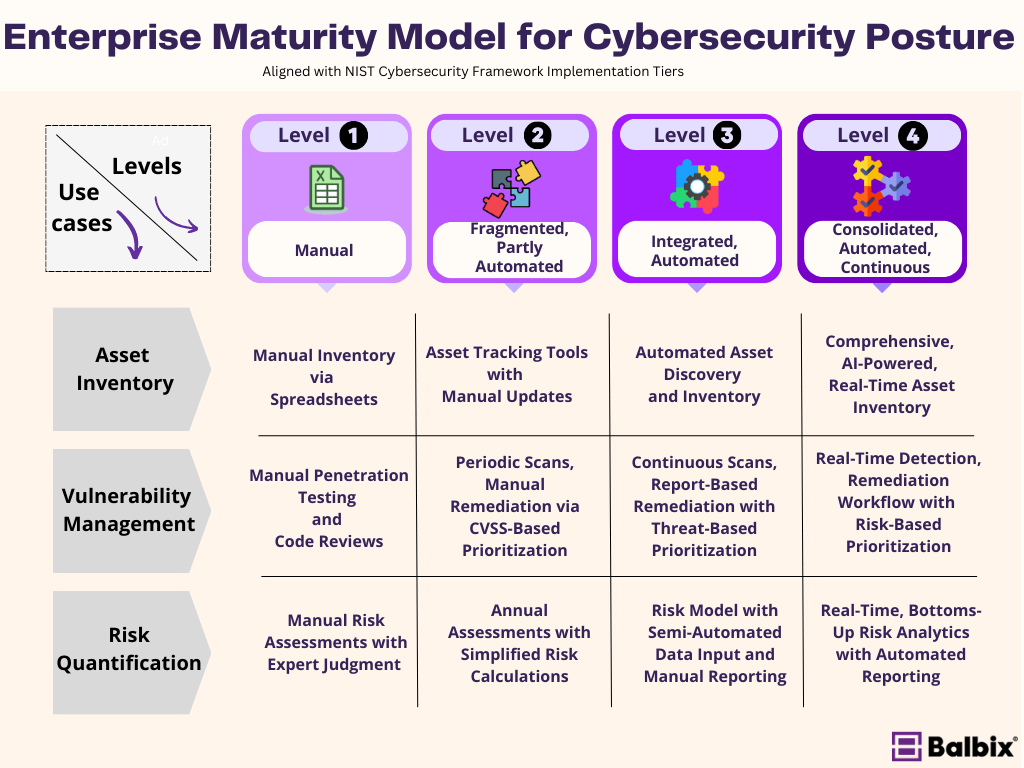
The proposed Enterprise Maturity Model for Cybersecurity Posture (EMM), a concept developed by Balbix, assists organizations, particularly security leaders, in identifying their current cybersecurity maturity stage and the subsequent steps needed for advancement. This model is inspired by and complements the NIST Cybersecurity Framework and essentially forms a strategic roadmap for enhancing an organization’s security posture.
Level 1 (Manual) pertains to organizations that mainly use manual methods, such as maintaining spreadsheets manually for asset inventory and employing human-driven penetration testing and static code reviews for vulnerability management. Risk assessment at this level primarily relies on expert judgment.
Level 2 (Fragmented, Partly Automated) represents organizations that employ asset tracking tools and scheduled vulnerability scans, albeit still requiring manual updates and performing basic risk prioritization. At this stage, vulnerabilities are remediated using CVSS-based prioritization methods. Risk assessments occur at irregular intervals and rely on relatively straightforward calculations. The assessment coverage, often unvalidated, may harbor gaps, overlaps, or conflicts, potentially leading to inaccuracies in the risk profile.
Level 3 (Integrated, Automated) describes organizations that have adopted automated asset discovery and inventory, along with continuous vulnerability scanning. Remediation at this level is handled via threat-based prioritization. Semi-automated data input and manual reporting are used for risk quantification within their formally structured cybersecurity programs.
Finally, Level 4 (Consolidated, Automated, Continuous) embodies organizations that maintain a comprehensive, real-time, and unified asset inventory that is clean, normalized, and de-duplicated using advanced practices. They also leverage AI-powered risk-based vulnerability prioritization and automated risk analytics. These organizations employ continuous monitoring and improvements in their mature cybersecurity programs, integrating real-time risk analytics with automated reporting.
To summarize, here are the steps you can take to transform your cybersecurity posture:
Navigating the path to mature and unified cybersecurity involves moving beyond fragmentation and over-reliance on familiar tools. By adopting a comprehensive strategy and consolidating tools, organizations gain visibility, streamline processes, and respond efficiently to threats. The proposed Enterprise Maturity Model for Cybersecurity Posture (EMM), in tune with the NIST Cybersecurity Framework, helps chart this journey.