
September 26, 2025
The call came from a Fortune 20 customer yesterday morning.
“Hey, Vinay, we’re getting flooded with noise about these two new Cisco ASA/FTD vulnerabilities that CISA posted the emergency advisory on.
We are seeing a ton of inconsistent information, would like something to put it together for an exec view.
Some enterprises are shutting down their ASAs while they figure it out, but we aren’t seeing it yet.
My team just wants clarity: are we exposed, and what should we do first?”
I’ve had that type of call many times before. Usually, it means days of the analysts on the Balbix dashboard, combing through vendor docs, slack threads full of speculation, and long nights before anyone has a clear, confident plan.
But this time, I had something special to offer…
I ran CVE-2025-20333 and CVE-2025-20362 through our new Deep Research system.
Balbix Deep Research (BDR) is a new capability we’ve been building to take vulnerability analysis to the next level. While Balbix already deduplicates, analyzes and scores vulnerabilities and exposures based on risk, BDR goes further by generating focused, campaign-level analysis on emerging threats. A “What-if” engine explores CVE chaining and mitigation effectiveness, analyzing how specific attacks could unfold in your environment. By combining exploit details, threat actor TTPs, and vulnerability intelligence with your enterprise cybersecurity, IT, and business context, BDR delivers insights that are specific and actionable.
A few minutes later, and for about forty cents of compute cost, I had a full report. I sent it to the customer and got back a “Love it, Thanks!”
Let me show you what the report looked like.
The overall structure of the Balbix Deep Research output report for an emerging threat is this.

The BDR report starts with a crisp summary:

Instead of just listing CVEs, the report from BDR laid out the attacker’s path:

The report didn’t stop at arrows. and included exploitation details, like this snippet:
Step 1: Authentication Bypass via CVE-2025-20362
Vulnerability: VPN Web Server Missing Authentication Authorization
Attack Vector: T1078 – Valid Accounts, T1550.001 – Application Access Token
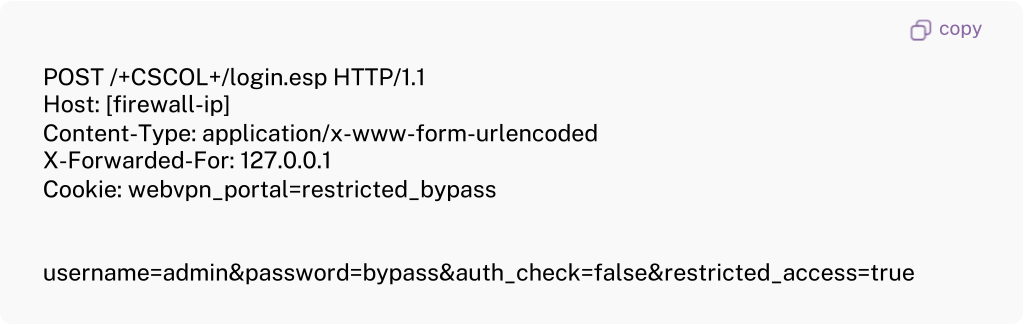
Exploitation Process:
Result: Unauthenticated administrative access to restricted VPN web server endpoints
followed by this one for Step 2.
Step 2: Remote Code Execution via CVE-2025-20333
Vulnerability: VPN Web Server Remote Code Execution
Exploitation: T1059.004 – Unix Shell, T1203 – Exploitation for Client Execution

That’s how attackers chained access into persistence. Two bugs weren’t just “two bugs” — they were a campaign playbook.
Following this, the BDR report had information about Advanced Exploitation, Sophisticated Attack Variations including Reconnaissance & Initial Exploitation, Persistence/Evasion and Network Pivoting & Command/Control techniques associated with this campaign.
The report then split the risk by device family:
And it tied this to product lifecycle of the affected asset types.
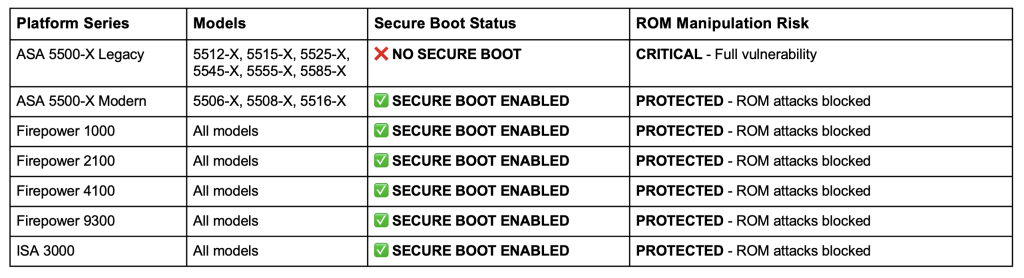
Several legacy models, ASA 5525-X, 5545-X, 5555-X, 5585-X, all hit end of support on September 30, 2025. That meant patching alone wasn’t going to be enough; they needed to be retired.
This distinction changes everything. Legacy ASA meant permanent compromise. Secure Boot devices? Still vulnerable, but survivability was blocked.
Then came my favorite part. Instead of saying “check if Secure Boot is enabled,” the report provided a playbook for cyber defenders.
Quick Reference:
followed by a detailed verification steps section structured like:
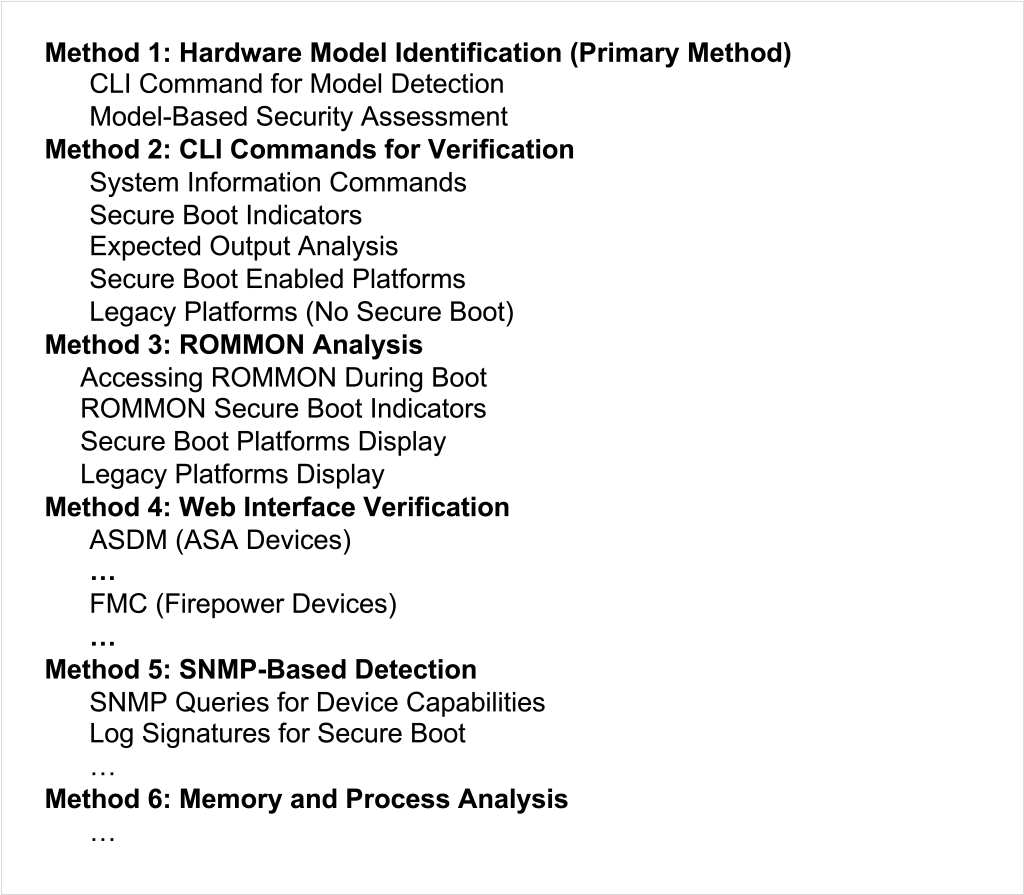
With Method 1, for example, the CLI instructions provided for Model Detection:
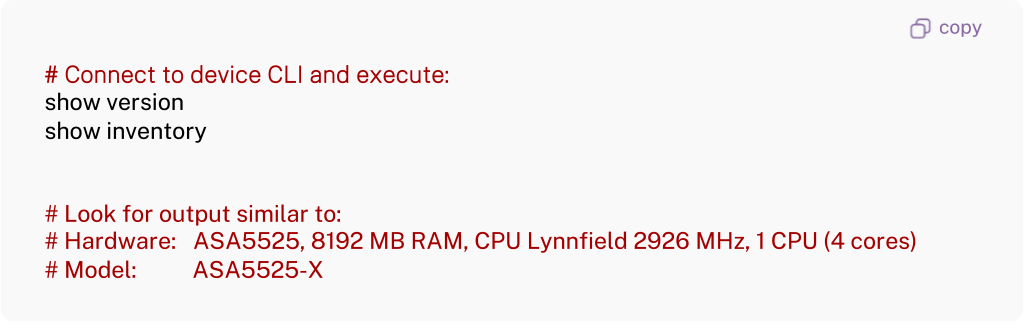
and for Security Assessment:
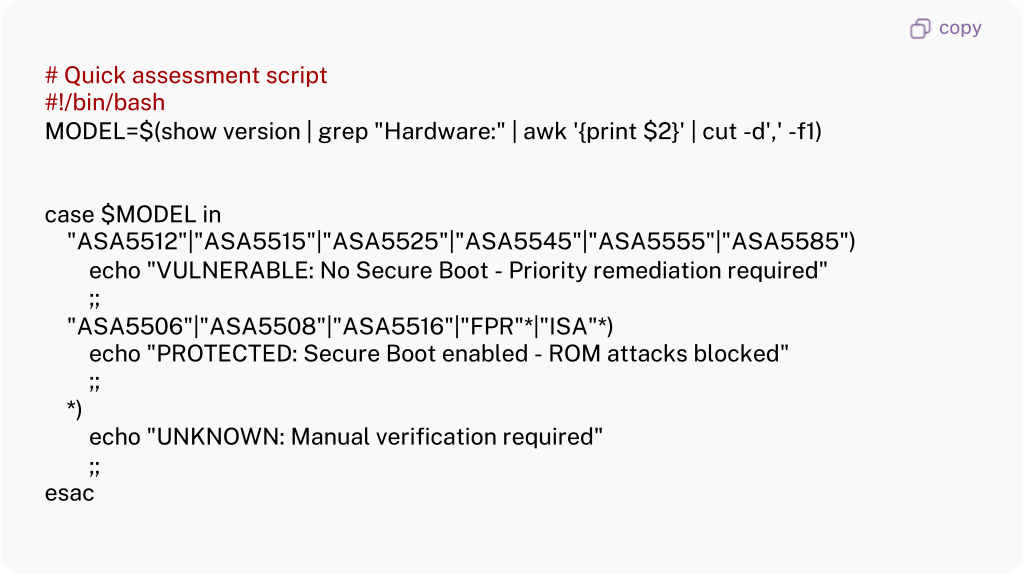
Other methods are provided as alternatives in case Method 1 is not practical for some reason.
This type of information is what turns guidance into action. An ops engineer could paste these commands into their terminal tonight and know which devices to triage.
Finally, the report laid out actions with urgency and clarity:
Immediate (0–24h):
“Follow CISA ED 25-03 core dump collection procedures immediately before any remediation attempts to preserve forensic evidence.”
“Isolate legacy ASA devices from high-value networks immediately — ROM persistence makes these highest risk.”
“Prepare for complete factory reset procedures post-patching due to potential ROM compromise.”
Short-Term (days):
“Permanently disconnect legacy ASA devices with end-of-support dates on or before September 30, 2025.”
Long-Term:
“Accelerate replacement of legacy ASA with Secure Boot-enabled platforms. Implement Zero Trust to reduce dependency on perimeter devices.”
Not just “patch now,” but a roadmap: preserve evidence, patch, retire, and modernize.
Here’s where the Balbix special sauce comes in. Balbix Deep Research produced a tailored playbook because it already had Balbix context:
Without this context, you’d get a generic write-up. With it, you get a playbook matched to your environment.
Balbix Deep Research is also available in BIX.
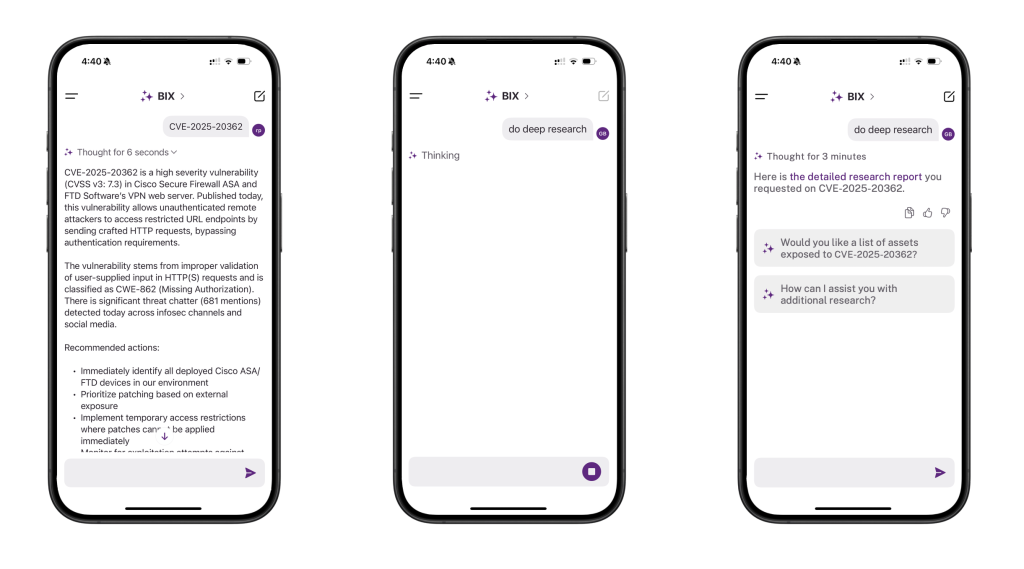 A simple query triggers Deep Research, giving you clarity on critical threats in minutes, even if you’re at dinner or waiting at the airport.
A simple query triggers Deep Research, giving you clarity on critical threats in minutes, even if you’re at dinner or waiting at the airport.
The Economics of Clarity
And all of this cost forty cents to generate.
Traditionally, a team of analysts would spend days performing this analysis and creating a report like this, at a cost of thousands of dollars, all while adversaries were already exploiting the chain. Balbix Deep Research did it in under 3 minutes.
So, when that Fortune 20 customer asked me if they were exposed and what they should do first, this time I had something special to offer.
Balbix Deep Research gave the Balbix customer:
That’s what Balbix delivers: clarity in the middle of chaos.
If you are a Balbix customer and would like to use Balbix Deep Research, please reach out to your Balbix support contact.
If you are not a customer yet, you can request a demo here.