September 27, 2022
I recently read an engrossing book – “The Wisdom of Wolves: Lessons From the Sawtooth Pack”. The book is written by a couple who coexisted closely with a pack of wolves over a span of 6 years. The authors reflect on the numerous “human-like” virtues they observed while living as a part of wolf society. Among the wild animals, wolves are normally demonized for their ferocious behavior, however this book shares a different perspective. It brings to light a meaningful thought process behind their actions. As one example, wolves carefully organize and plan their attacks – contrary to popular belief, they do not attack every animal that crosses their path. In particular, wolves take the following approach when dealing with risk:
Much like wolves have built-in mechanisms to evaluate risks based on context and intelligently balance the costs of risk vs. action, a well-designed proactive cybersecurity program is no different in this regard. Caught between the mountains of vulnerabilities detected in their environments on one hand, and limited remediation capacity on the other, vulnerability management teams must triage and prioritize where to focus precious energy and resources. For every high-priority vulnerability that is remediated today or this week, there are often far more that are left unaddressed.
So how should security teams handle unremediated vulnerabilities?
In this blog, we explore that question and focus on two key concepts – why vulnerability risk acceptance is necessary in certain situations and how Balbix can help InfoSec teams stay on top of these risks in a structured way.
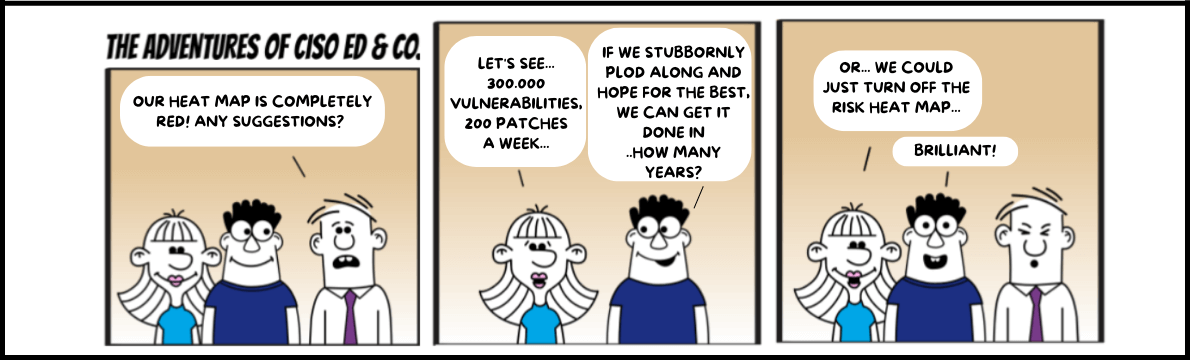
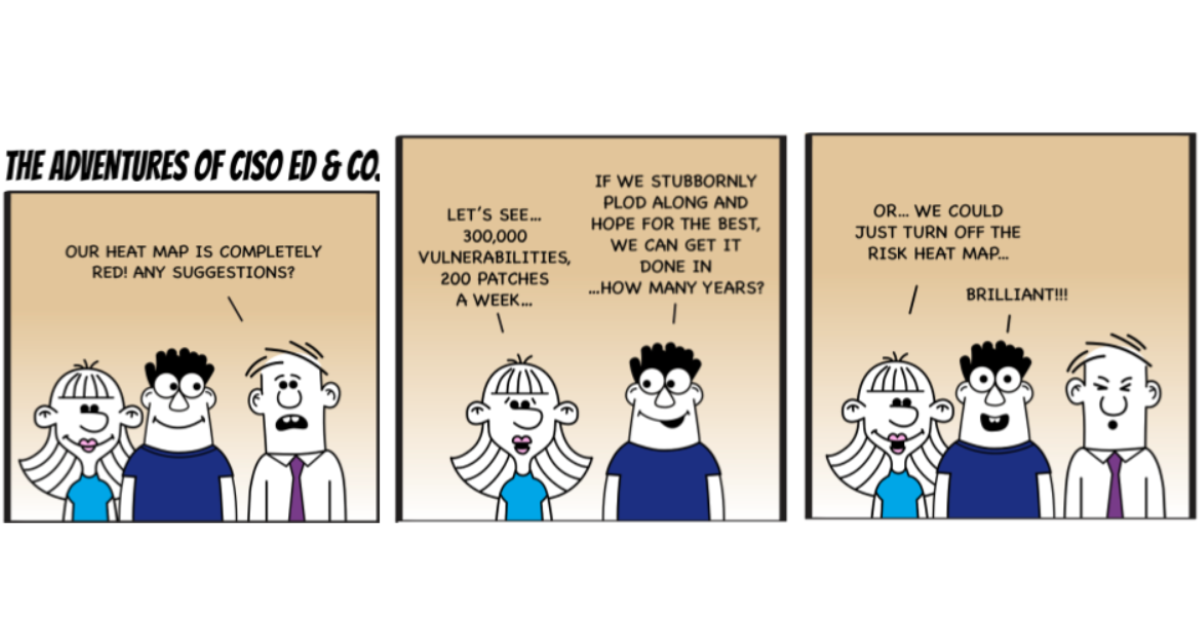
Many cybersecurity organizations find themselves in the following predicament:
Given this situation, risk-based vulnerability management (RVBM) is the approach organizations should take in order to focus their limited remediation capacity on those vulnerabilities that present the greatest business risk. Here, Balbix helps organizations operate best-in-class RBVM programs, driving down MTTP (mean-time-to-patch) for critical systems from many weeks or months to mere days.
But let’s return to the topic of those vulnerabilities that were not selected for remediation. How should we manage the backlog of these outstanding vulnerabilities in a holistic and consistent way? How should teams most effectively manage the process considering key stakeholders such as executives, operational IT teams and auditors?
Stakeholders expect the vulnerability management team to provide relevant status, clear ownership and consistent process for addressing each vulnerability.
Let’s look at the goals that matter most to each group:
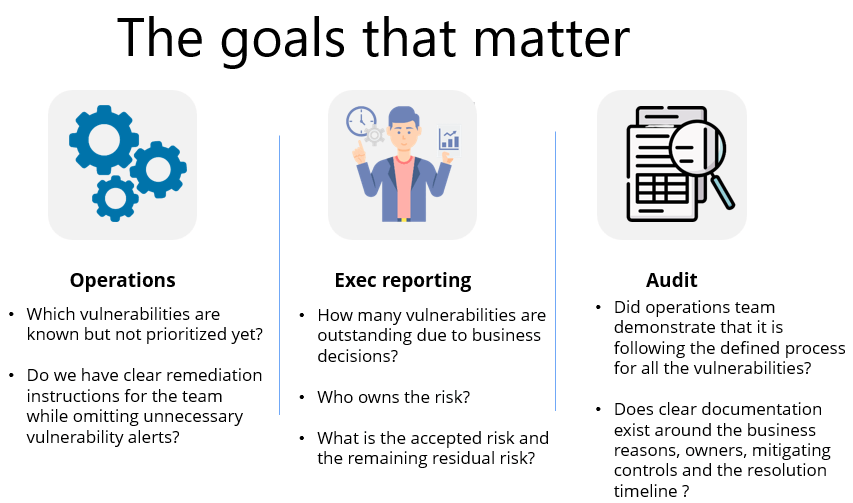
In order to serve the diverse needs of these stakeholders, an effective vulnerability management program needs to
Therefore, a well-designed risk acceptance process is a core enabler to address these requirements. Note that there can be a variety of valid reasons for triggering this process and accepting risks related to a given vulnerability.
Many organizations undergo an standardized testing process to determine if a given fix will cause problems (e.g. breaking an app, incompatibility issues) for their unique combination of hardware, software and configuration settings. Testing typically follows a defined cycle (Dev ➞ QA ➞ Production) in a controlled setting. Risk owners may choose to temporarily accept the associated vulnerability risks to account for this business process.
Once tested, patch deployment often happens in multiple waves depending on the organization’s policies. This process may run into several weeks. To avoid flagging vulnerabilities that are in process of being patched, the risk owner may temporarily accept the risk.
Most security teams have time-bound SLA (service level agreement) business policies outlining the number of days they may take to fix affected systems, depending on vulnerability severity and threat level, asset type, or other factors. To avoid unnecessary escalations, particularly when vulnerabilities are still within SLA timelines, organizations often want the flexibility to accept associated risks until the permitted target date.
There may be important operational considerations for affected systems that limit any changes to periodic maintenance or reboot windows, particularly for OT, manufacturing or regulated environments. A risk owner may need to accept associated risks for 2 weeks until the next maintenance window is available.
Sometimes vulnerability scanners generate false positives, particularly when running unauthenticated scans. Risk owners need the ability to mark these false positives accordingly, effectively choosing the option “Don’t show this to me again.”
There are often situations where security teams already have effective controls in place via administrative process or prior investments in cybersecurity tools, e.g., virtual patching, firewall, or IPS (intrusion prevention system), which would prevent an adversary from exploiting a given vulnerability. In particular, security personnel typically rely on mitigations when high visibility zero-day vulnerabilities are detected and patches are either not yet available or cannot be quickly deployed. Under these circumstances, vulnerabilities may be accepted until ultimately remediated, relying on appropriately documented mitigations.
Balbix is the leading cybersecurity posture automation company. Balbix Risk-based Vulnerability Management (Balbix RBVM) uses automation and AI to help you align your vulnerability management programs with business priorities and reduce business risk faster.
To identify and prioritize vulnerabilities, Balbix RBVM automatically ingests vulnerability and asset data from your existing tools, fills in data gaps, adds business context and uses sophisticated AI algorithms to calculate your overall risk based on breach likelihood. You can then view risk issues by site, business unit, risk owner, asset class, attack vector and CVEs to further align security and business leaders. Security teams can operationalize high velocity risk reduction and make better decisions faster.
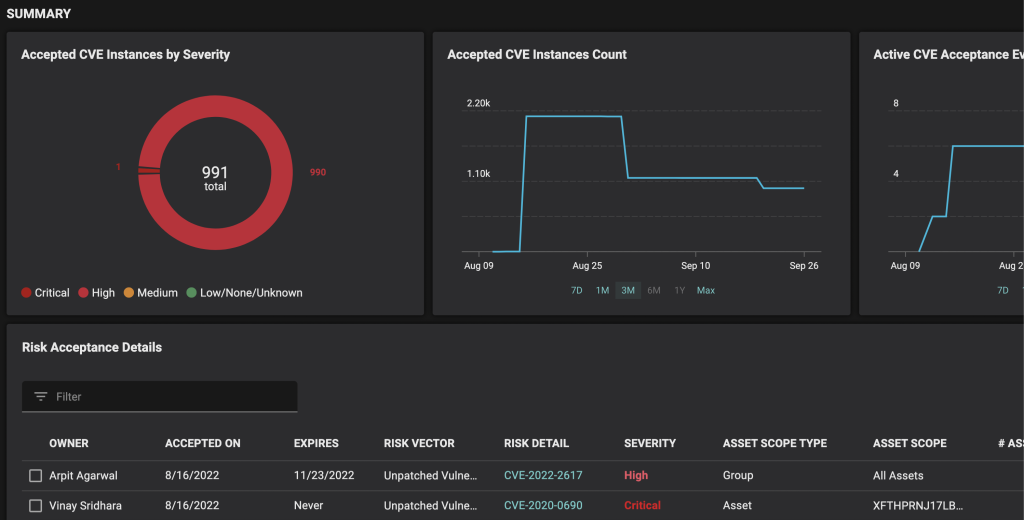
The Balbix product team recently introduced a powerful new enhancement to our Risk Acceptance capability. With just a few clicks, the user can select vulnerabilities (CVEs) of interest, assign the risk owner, select and document the reason for risk acceptance and time-bound the acceptance with an expiry target date. From this point, these vulnerability instances are identified as ‘accepted’ throughout the Balbix dashboards.
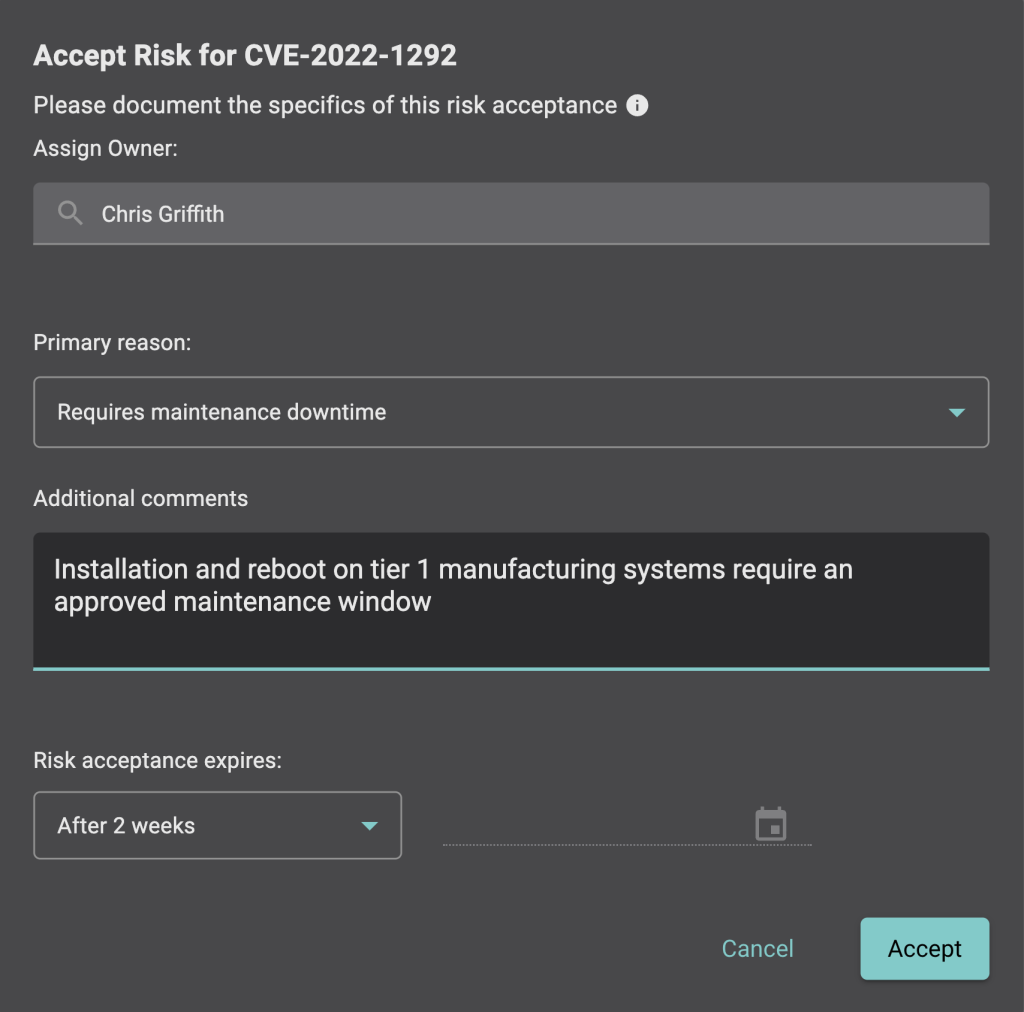
Balbix handles all of the tracking around acceptance events automatically, providing a comprehensive summary dashboard for reporting on vulnerability instances with risk acceptances, trends, severity analytics, and all associated detail. The result is clear, concise, efficient and audit-ready vulnerability acceptance for your CVEs to keep all of your stakeholders on the same page without resorting to offline spreadsheets and dozens of emails.
Keep those “cyber wolves” at bay and start your own journey to security posture automation by scheduling a 30-minute demo with Balbix.