

May 3, 2024
Recently, I wrapped up my first work trip with Balbix—a whirlwind tour of customer roundtables in Singapore, Melbourne and Sydney. We were joined by local EY teams that have been working with us for almost an entire year to explore the topic of Cyber Risk Management in the region. EY has launched a new managed service offering—Continuous Threat Exposure Management (CTEM)—with Balbix providing the underlying AI engine and tech platform.
Over the last two months, I’ve met or spoken with almost 70 security teams around what I believe is a topic that is top of mind for most security professionals – how can Artificial Intelligence (AI) help identify and reduce my company’s cyber risk exposure. A decent proxy for the success of any risk management organization is whether they are at an acceptable level of risk. Gone are the days of confidence level scores (high, medium, low) or when security teams could only talk about how much investment they have made in security controls or how many tools they have implemented. In summary, can you answer a simple question: Are you adequately fortified against cyber-attacks?
In 2024, the rejoinder is encouraging as security teams are beginning to weave AI solutions into their day-to-day operations to finally get smart on prioritizing the most material assets against the most likely vulnerabilities and avert disaster.
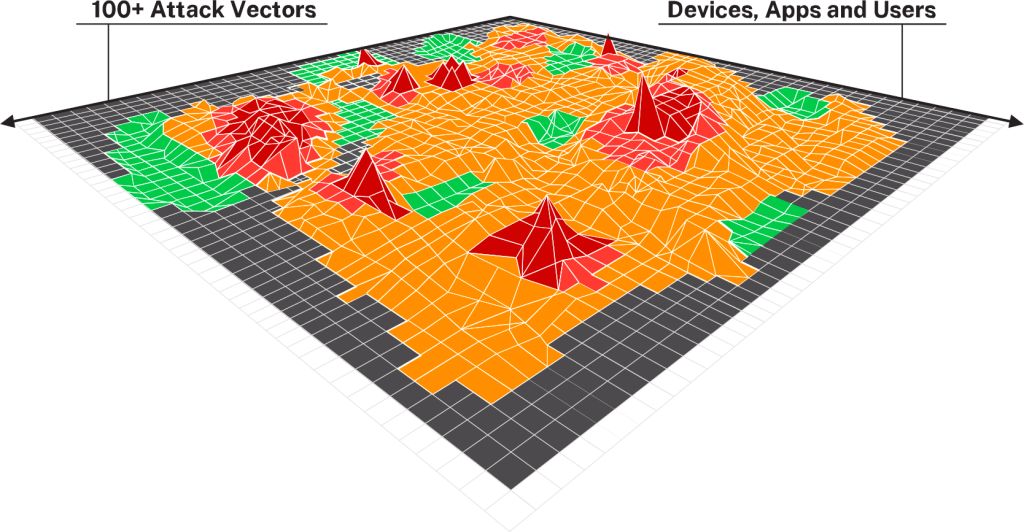
Risk management issues are no different in Asia Pacific than they are in the rest of the world. As we dove into the topic of risk quantification, we tried to peel back the onion on how organizations approach quantification of cyber risk today, Why organizations cannot afford to miscalculate this risk and what approach security teams are taking to burn down risk to acceptable levels quickly? Particularly, we discussed the concept of a continuous threat and exposure management program to create a repeatable process around risk management and how organizations can leapfrog the arduous process of prioritizing and patching the most critical vulnerabilities across their asset base.
Three themes emerged during our conversations across the board:
Cyber risk can no longer be ignored and is on par with financial and/or supply chain risk during board discussions. Leadership doesn’t just want to know about the number of tools and policies in their organization but rather wants a tangible common currency to talk about risk. Historically, this has been extremely difficult and time-consuming as it requires managing an immense amount of data, analyzing trends and driving correlations in a traditional spreadsheet fashion.
However, data management and risk calculation methodology using AI was the singular topic on which we spent most of our discussion during these roundtables. Security professionals want to better understand the underlying logic of how the AI system recognizes assets and allocates priority to them—a very critical step preceding the adoption of AI systems, explained in detail in this blog – Balbix’s Approach to Cyber Risk Quantification Supercharged by AI.
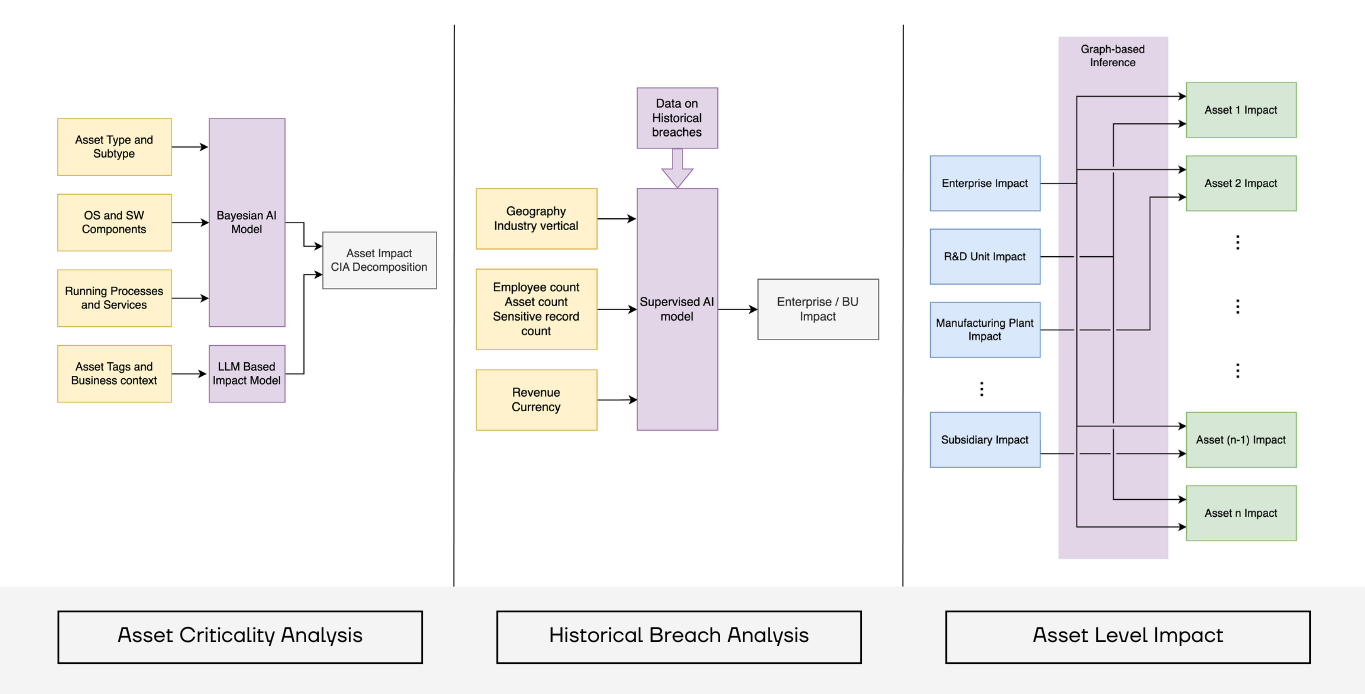
These discussions on uncovering the logic and understanding the number of machine learning models within our system were particularly impactful in demonstrating the level of complexity involved in driving accurate risk calculations.

The second core takeaway for me was how security teams are beginning to realize that point solutions that contribute to risk quantification need to work together to create a seamless platform that not only informs risk burn down efforts but also allows practitioners to understand better how asset mapping, vulnerability identification and risk calculations are interconnected.
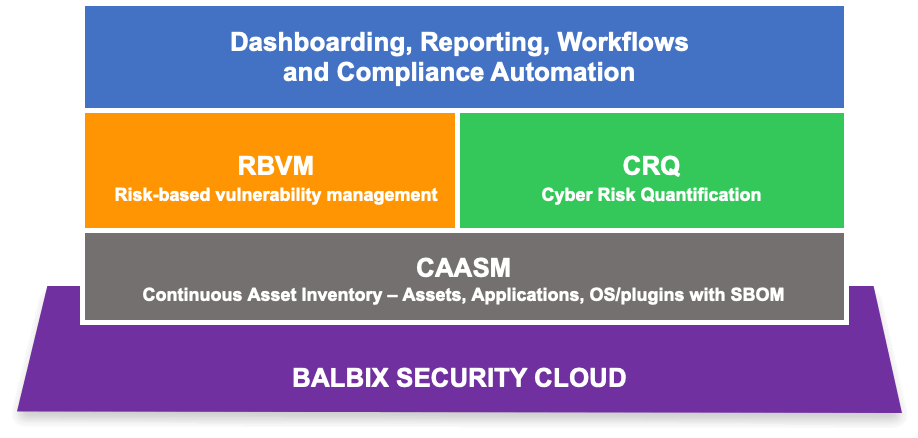
As organizations begin deploying a CTEM methodology for risk management, we will see the rise of a common metric (either in dollar terms or something as simple as a scale of 1 to 100) to talk about cyber risk. Cyber risk will soon become everyone’s responsibility and it won’t be just security teams talking about mitigating risk. A simple view of how much risk each business unit carries will be sufficient for an org-level alignment on core priorities and actions across stakeholders
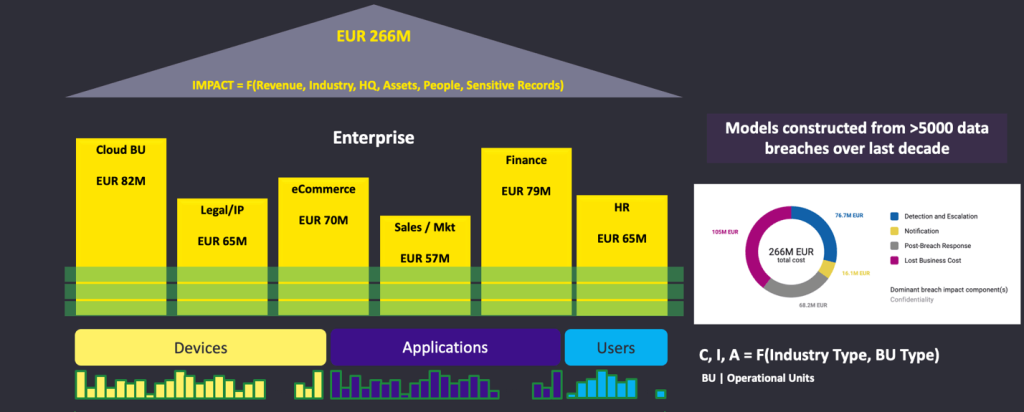
Anyone who has worked in Asia or spent any time in this part of the world knows how passionate the teams here are about becoming early adopters of new technology, and this is what I am most excited about. The conversations with customers here have left me energized, and I am intrigued by how security teams in this region will utilize AI to transform their risk management offices.
A big thank you to our partners at EY, who have created a fantastic CTEM offering. We are already starting to see real, tangible benefits (reduced opex for vulnerability management and cost avoidance in the tech stack) with our joint solution.
Request a demo to learn how Balbix can help you reduce cyber risk by prioritizing the most critical assets and vulnerabilities with the highest likelihood of attack.