September 10, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 86 CVEs, including 5 republished CVEs. Overall, Microsoft announced 2 Zero-Day, 9 Critical, and 73 Important vulnerabilities.

From an Impact perspective, Escalation of Privilege vulnerabilities accounted for 44%, while Remove Code Execution for 27% and Information Disclosure for 16%.
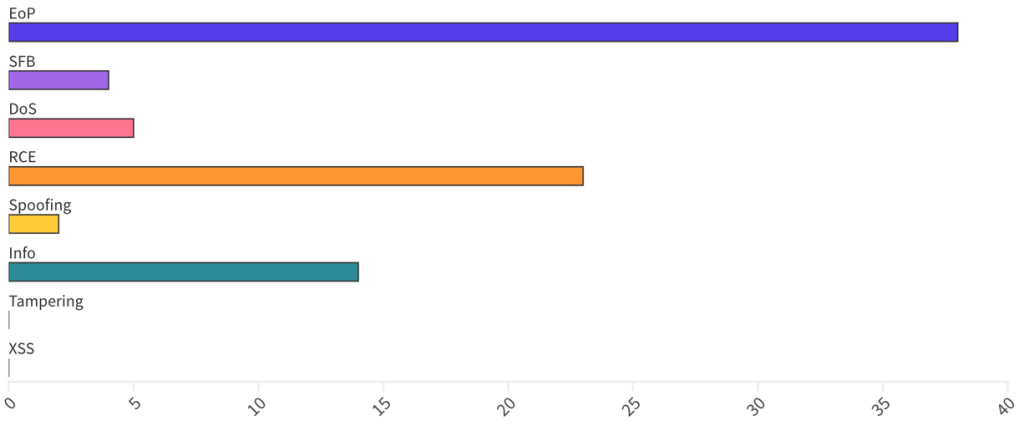
Patches for this month cover components for the following areas:
Here’s a closer look at the most interesting Microsoft CVEs:
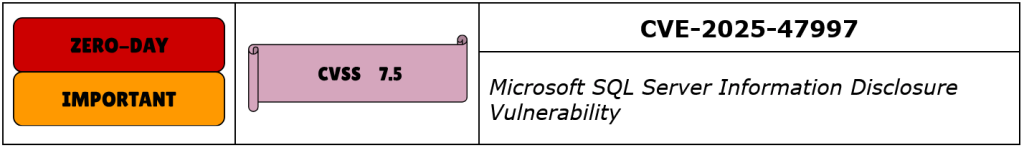
CVE-2025-47997 is an information disclosure vulnerability in Microsoft SQL Server, caused by a race condition (CWE-362) in the SQL engine’s handling of Dynamic Management Views (DMVs). Specifically, concurrent execution using shared resources with improper synchronization allows an authenticated attacker to access sensitive information from other user sessions.
The vulnerability arises when a low-privileged user queries DMVs such as sys.dm_exec_requests or sys.dm_exec_sql_text. Due to a timing flaw in how SQL Server synchronizes access to internal memory buffers, the attacker may retrieve the text of SQL statements currently being executed by other sessions. This violates session isolation and exposes potentially sensitive data, including credentials, PII, or proprietary logic embedded in SQL queries.
The attack requires:
The vulnerability does not impact integrity or availability, but it does result in high confidentiality impact, earning a CVSS v3.1 score of 6.5 (Medium).
Microsoft addressed the issue with a security update (SQL Server 2022 CU20 and SQL Server 2019 GDR KB5065223), which improves synchronization logic and restricts unintended exposure of DMV data.
Mitigation recommendations include:
This vulnerability is cataloged under CWE-362 (Race Condition) and CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor).
CVE-2025-55234 is an elevation of privilege (EoP) vulnerability in the Windows Server Message Block (SMB) protocol. The flaw arises from insufficient hardening against NTLM relay attacks, which can allow an unauthenticated attacker to impersonate a legitimate user and gain elevated privileges under specific conditions.
This vulnerability affects environments where SMB servers are not configured with Extended Protection for Authentication (EPA) or SMB signing, both of which are designed to mitigate relay attacks. Without these protections, an attacker positioned on the network can intercept and relay NTLM authentication messages between a client and server, effectively authenticating as the victim user.
Microsoft released CVE-2025-55234 to help organizations audit and assess their SMB configurations prior to enforcing stricter hardening measures, introducing new audit capabilities that allow administrators to detect devices or software that may be incompatible with EPA or SMB signing, which are required to fully mitigate this vulnerability.
Key technical attributes:
This vulnerability does not stem from a flaw in the SMB protocol itself, but rather from misconfigured or insufficiently hardened deployments. It was publicly disclosed prior to patch availability, increasing the urgency for remediation.
Mitigation guidance includes:
CVE-2025-55234 is part of a broader effort to reduce exposure to relay attacks across Windows systems and underscores the importance of enforcing modern authentication protections in SMB deployments.
CVE-2025-54918 is an elevation of privilege vulnerability in the Windows NT LAN Manager (NTLM) authentication protocol. The flaw is caused by improper authentication logic (CWE-287), which allows an attacker with valid credentials to escalate privileges over the network under specific conditions.
The vulnerability affects Windows systems where NTLM is still enabled for compatibility with legacy services and applications. NTLM authentication relies on challenge-response mechanisms that, if not properly validated or bound to secure channels, can be exploited to impersonate users or obtain elevated access. In this case, the protocol fails to correctly enforce identity binding during the authentication exchange, allowing an attacker to gain unauthorized access to higher-privilege resources.
Key technical attributes:
The vulnerability does not require user interaction and can be triggered remotely by an attacker with low privileges. It does not involve code execution but enables unauthorized access to sensitive resources, making it a critical concern in enterprise environments where NTLM is still in use.
Microsoft released a fix for CVE-2025-54918 in this Patch Tuesday update, which includes hardened authentication logic to prevent privilege escalation via NTLM. Organizations are strongly advised to:
This vulnerability underscores the ongoing risks associated with legacy authentication protocols and the importance of enforcing modern security controls in Windows environments.
CVE-2025-54910 is a heap-based buffer overflow vulnerability (CWE-122) in Microsoft Office that allows an attacker to execute arbitrary code locally. The flaw occurs when Office document parsers allocate memory on the heap and subsequently write more data than the allocated buffer can hold, leading to memory corruption and potential control-flow hijacking.
This vulnerability affects multiple Office components—including Word, Excel, PowerPoint, and Visio—when processing specially crafted documents containing malformed embedded objects, OLE streams, or shape metadata. Common triggers include:
When exploited, the overflow can corrupt adjacent heap metadata or overwrite function pointers and vtable entries. If the attacker controls the overwritten data, they may redirect execution to attacker-controlled memory, resulting in arbitrary code execution within the context of the Office process.
Key technical attributes:
The vulnerability does not require elevated privileges or user interaction, making it particularly dangerous in scenarios where Office documents are processed automatically or in background services. It is exploitable via local access, such as opening a malicious document on the target system.
Microsoft addressed CVE-2025-54910 in this Patch Tuesday update, which includes hardened memory allocation routines and stricter bounds checking in affected Office parsers. Mitigation guidance includes:
This vulnerability reinforces the importance of secure memory handling in document parsers and the need for layered defenses against file-based exploitation.
CVE-2025-55224 is a local code execution vulnerability in the Windows Win32K graphics subsystem (GRFX), caused by a race condition in concurrent execution using shared resources. The flaw is classified under CWE-362 (Improper Synchronization) and CWE-416 (Use After Free), and it allows an authorized attacker to execute arbitrary code on the affected system.
The vulnerability arises when multiple threads within the Win32K GRFX component access shared memory structures without proper synchronization. Under specific timing conditions, this can lead to a use-after-free scenario, where a memory object is freed by one thread while still being accessed by another. If the attacker can control the timing and contents of the freed memory, they may redirect execution flow and achieve code execution within the context of the current user.
Key technical attributes:
The vulnerability requires local access and low privileges, but no user interaction. Due to the scope change, successful exploitation may allow the attacker to escape sandboxed environments or elevate privileges across security boundaries.
Microsoft addressed CVE-2025-55224 in this Patch Tuesday update, which includes memory management hardening and improved synchronization logic within the Win32K GRFX subsystem. Mitigation guidance includes:
This vulnerability highlights the importance of robust concurrency control and memory safety in any kernel-level component.
| CVE | Severity | Type | CVSS | Exploitation |
|---|---|---|---|---|
| CVE-2025-47997 | Important | DoS | 7.5 | KNOWN EXPLOIT |
| CVE-2025-49692 | Important | Info | 6.5 | Unlikely |
| CVE-2025-49734 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53791 | Important | EoP | 7 | Less Likely |
| CVE-2025-53796 | Important | Info | 6.5 | Unlikely |
| CVE-2025-53797 | Important | Info | 6.5 | Unlikely |
| CVE-2025-53798 | Important | Info | 6.5 | Unlikely |
| CVE-2025-53799 | Critical | Info | 5.5 | Unlikely |
| CVE-2025-53800 | Critical | EoP | 7.8 | Less Likely |
| CVE-2025-53801 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53802 | Important | EoP | 7 | Less Likely |
| CVE-2025-53803 | Important | Info | 5.5 | More Likely |
| CVE-2025-53804 | Important | Info | 5.5 | More Likely |
| CVE-2025-53805 | Important | DoS | 7.5 | Unlikely |
| CVE-2025-53806 | Important | Info | 6.5 | Unlikely |
| CVE-2025-53807 | Important | EoP | 7 | Less Likely |
| CVE-2025-53808 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-53809 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-53810 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-54091 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54092 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54093 | Important | EoP | 7 | More Likely |
| CVE-2025-54094 | Important | EoP | 6.7 | Unlikely |
| CVE-2025-54095 | Important | Info | 6.5 | Unlikely |
| CVE-2025-54096 | Important | Info | 6.5 | Unlikely |
| CVE-2025-54097 | Important | Info | 6.5 | Unlikely |
| CVE-2025-54098 | Important | EoP | 7.8 | More Likely |
| CVE-2025-54099 | Important | EoP | 7 | Less Likely |
| CVE-2025-54101 | Important | RCE | 4.8 | Less Likely |
| CVE-2025-54102 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54103 | Important | EoP | 7.4 | Less Likely |
| CVE-2025-54104 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-54105 | Important | EoP | 7 | Less Likely |
| CVE-2025-54106 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-54107 | Important | SFB | 4.3 | Less Likely |
| CVE-2025-54108 | Important | EoP | 7 | Unlikely |
| CVE-2025-54109 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-54110 | Important | EoP | 8.8 | More Likely |
| CVE-2025-54111 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54112 | Important | EoP | 7 | Unlikely |
| CVE-2025-54113 | Important | RCE | 7.5 | Unlikely |
| CVE-2025-54114 | Important | DoS | 7 | Less Likely |
| CVE-2025-54115 | Important | EoP | 7 | Less Likely |
| CVE-2025-54116 | Important | EoP | 7.3 | Unlikely |
| CVE-2025-54894 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54895 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54896 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-54897 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-54898 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54899 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-54900 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-54901 | Important | Info | 5.5 | Less Likely |
| CVE-2025-54902 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54903 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54904 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54905 | Important | Info | 7.1 | Less Likely |
| CVE-2025-54906 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54907 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54908 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-54910 | Critical | RCE | 8.4 | Less Likely |
| CVE-2025-54911 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-54912 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-54913 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-54915 | Important | EoP | 6.7 | Unlikely |
| CVE-2025-54916 | Important | RCE | 7.8 | More Likely |
| CVE-2025-54917 | Important | SFB | 4.3 | Less Likely |
| CVE-2025-54918 | Critical | EoP | 8.8 | More Likely |
| CVE-2025-54919 | Important | RCE | 7.5 | Less Likely |
| CVE-2025-55223 | Important | EoP | 7 | Less Likely |
| CVE-2025-55224 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-55225 | Important | Info | 6.5 | Less Likely |
| CVE-2025-55226 | Critical | RCE | 6.7 | Less Likely |
| CVE-2025-55227 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-55228 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-55232 | Important | RCE | 9.8 | Less Likely |
| CVE-2025-55234 | Important | EoP | 8.8 | KNOWN EXPLOIT |
| CVE-2025-55236 | Critical | RCE | 7.3 | Less Likely |
| CVE-2025-55243 | Important | Spoofing | 7.5 | Less Likely |
| CVE-2025-55245 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-55316 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-55317 | Important | EoP | 7.8 | Unlikely |
| CVE-2024-21907 | High | DoS | 7.5 | Unlikely |
| CVE-2025-9864 | High | RCE | 8.8 | More Likely |
| CVE-2025-9865 | Medium | Spoofing | 5.4 | More Likely |
| CVE-2025-9866 | High | SFB | 8.8 | More Likely |
| CVE-2025-9867 | Medium | SFB | 5.4 | More Likely |
DOCKER – CVE-2025-9074 is a critical vulnerability in Docker Desktop that allows local Linux containers to access the Docker Engine API via the default subnet (typically 192.168.65.7:2375), even when Enhanced Container Isolation (ECI) is enabled or the “Expose daemon on tcp://localhost:2375 without TLS” option is disabled. This exposure enables containers to issue privileged commands to the Docker Engine, such as creating, modifying, or deleting other containers, managing images, and in some configurations — particularly Docker Desktop for Windows with WSL backend — mounting host drives with the same privileges as the user running Docker Desktop. The vulnerability stems from improper resource isolation (CWE-668), and has been assigned a CVSS v4.0 base score of 9.3 (Critical).
GOOGLE / APPLE / WHATSAPP – We usually don’t cover things like WhatsApp, but this one deserves attention, as it’s being used by many. In general, zero-day vulnerabilities are the most critical type of flaw because they are actively exploited before a patch is available. The public discussion and media coverage around these are exceptionally high due to the involvement of major consumer tech companies (Google and Apple) and a widely used application (WhatsApp), making it a top concern for millions of users. The no-user-interaction “zero-click” nature of the WhatsApp exploit makes it especially dangerous.
CVE-2025-55177 is an incorrect authorization vulnerability (CWE-863) in WhatsApp for iOS, WhatsApp Business for iOS, and WhatsApp for Mac. Prior to versions 2.25.21.73 and 2.25.21.78 respectively, linked device synchronization messages were insufficiently validated, allowing an unrelated user to trigger processing of arbitrary URLs on a target device. This flaw was exploited in a sophisticated zero-click attack chain alongside CVE-2025-43300, an Apple OS vulnerability, to deliver advanced spyware to high-value targets. Meta patched the issue in late August 2025, and it is now listed in CISA’s Known Exploited Vulnerabilities Catalog.
CVE-2025-48543 is a use-after-free vulnerability (CWE-416) in the Android Runtime (ART) component that enables local privilege escalation. The flaw allows a malicious app to escape the Chrome sandbox and interact with system_server, bypassing key security boundaries. It requires no user interaction and no additional execution privileges, making it highly exploitable. The vulnerability affects Android versions 13 through 16 and has been actively exploited in targeted attacks. Google patched the issue in the September 2025 Android Security Bulletin, and it has been added to CISA’s Known Exploited Vulnerabilities Catalog.
CVE-2025-38352 is a race condition vulnerability in the Android kernel’s CPU timer subsystem that can lead to memory corruption or system instability during process termination. The issue occurs when multiple threads interact with timer-related resources at the same time, without proper synchronization. Under specific timing conditions—particularly when a process is exiting and its timers are being cleaned up—one thread may prematurely release or modify memory that another thread is still accessing. This can result in use-after-free scenarios, crashes, or potential exploitation for privilege escalation. The vulnerability has been actively exploited in targeted attacks and was addressed in the September 2025 Android Security Bulletin. It affects multiple Android versions and has been added to CISA’s Known Exploited Vulnerabilities Catalog.
CISCO – CVE-2025-20265 is a critical remote code execution vulnerability in Cisco Secure Firewall Management Center (FMC) Software, stemming from improper input handling during RADIUS authentication. An unauthenticated attacker can exploit this flaw by sending specially crafted credentials to the FMC’s web-based or SSH management interface when RADIUS is configured, allowing arbitrary shell commands to be executed with elevated privileges. The vulnerability is classified under CWE-74 (Improper Neutralization of Special Elements in Output Used by a Downstream Component) and carries a CVSS v3.1 base score of 10.0 (Critical), making immediate patching essential for exposed systems.
FORTINET – CVE-2025-25256 is a critical pre-authentication command injection vulnerability in Fortinet FortiSIEM, affecting versions 7.3.0 through 7.3.1, 7.2.0 through 7.2.5, 7.1.0 through 7.1.7, 7.0.0 through 7.0.3, and all versions prior to 6.7.9. The flaw stems from improper input sanitization in the handleStorageArchiveRequest function of the phMonitor service, which listens on TCP port 7900 and uses a custom RPC protocol wrapped in TLS. Classified under CWE-78 (Improper Neutralization of Special Elements in OS Command), the vulnerability allows unauthenticated remote attackers to send crafted XML payloads — such as malicious values in the archive_nfs_archive_dir parameter — to execute arbitrary commands on the system. The root cause was traced to Fortinet’s use of the ShellCmd::addParaSafe function, which inadequately escaped input, and has since been replaced with stricter routines in patched versions. With a CVSS v3.1 score of 9.8 (Critical), this vulnerability has been exploited in the wild and poses a severe risk to enterprise SOC environments.
PALO ALTO NETWORKS – CVE-2025-2183 is a medium-severity vulnerability in the Palo Alto Networks GlobalProtect App, caused by insufficient certificate validation that can lead to privilege escalation. Specifically, when GlobalProtect is configured to validate portal or gateway certificates using a full certificate chain — either pushed via the portal or enabled through the FULLCHAINCERTVERIFY option—an attacker on the same subnet or a local non-administrative user can install a malicious root certificate. This allows the GlobalProtect App to connect to attacker-controlled servers, potentially enabling the installation of software signed by the rogue certificate. The flaw is categorized under CWE-295 (Improper Certificate Validation) and carries a CVSS v4.0 base score of 7.4 (High). Palo Alto Networks addressed the issue in GlobalProtect App versions 6.3.3-h2 and 6.2.8-h3 for Windows and Linux, and recommends auditing certificate trust configurations to ensure secure deployment.
CITRIX – CVE-2025-7775 is a critical memory overflow vulnerability in Citrix NetScaler ADC and NetScaler Gateway that allows remote code execution and denial of service when configured in specific roles. The flaw affects systems operating as Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy), AAA virtual server, or load balancing (LB) virtual servers of type HTTP, SSL, or HTTP_QUIC bound to IPv6 services or service groups—including DBS IPv6 configurations. It stems from improper restriction of operations within the bounds of a memory buffer (CWE-119), and has been actively exploited in the wild, prompting its inclusion in CISA’s Known Exploited Vulnerabilities Catalog. Citrix released patches for affected versions across branches 12.1, 13.1, and 14.1, and administrators are urged to apply mitigations immediately, restrict external access to vulnerable services, and follow BOD 22-01 guidance for federal systems.
TREND MICRO – CVE-2025-54948 and CVE-2025-54987 are two closely related critical vulnerabilities in the Trend Micro Apex One (on-premise) management console for Windows, both enabling pre-authenticated remote code execution via OS command injection. These flaws stem from improper neutralization of special elements used in operating system commands (CWE-78), allowing unauthenticated attackers to upload malicious payloads and execute arbitrary commands on affected installations. While CVE-2025-54948 targets standard x86/x64 deployments, CVE-2025-54987 affects systems running on alternate CPU architectures, but both share the same root cause and exploitation method. The vulnerabilities are remotely exploitable over the network without requiring user interaction or prior access, making them exceptionally dangerous in exposed enterprise environments. Each carries a CVSS v3.1 base score of 9.8 (Critical), and both have been added to CISA’s Known Exploited Vulnerabilities Catalog due to confirmed exploitation in the wild. Trend Micro issued patches and mitigation guidance via Security Advisory KA-0020652, urging administrators to apply updates immediately, restrict external access to the management console, and follow BOD 22-01 directives for federal systems.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by automation and AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix risk scores.
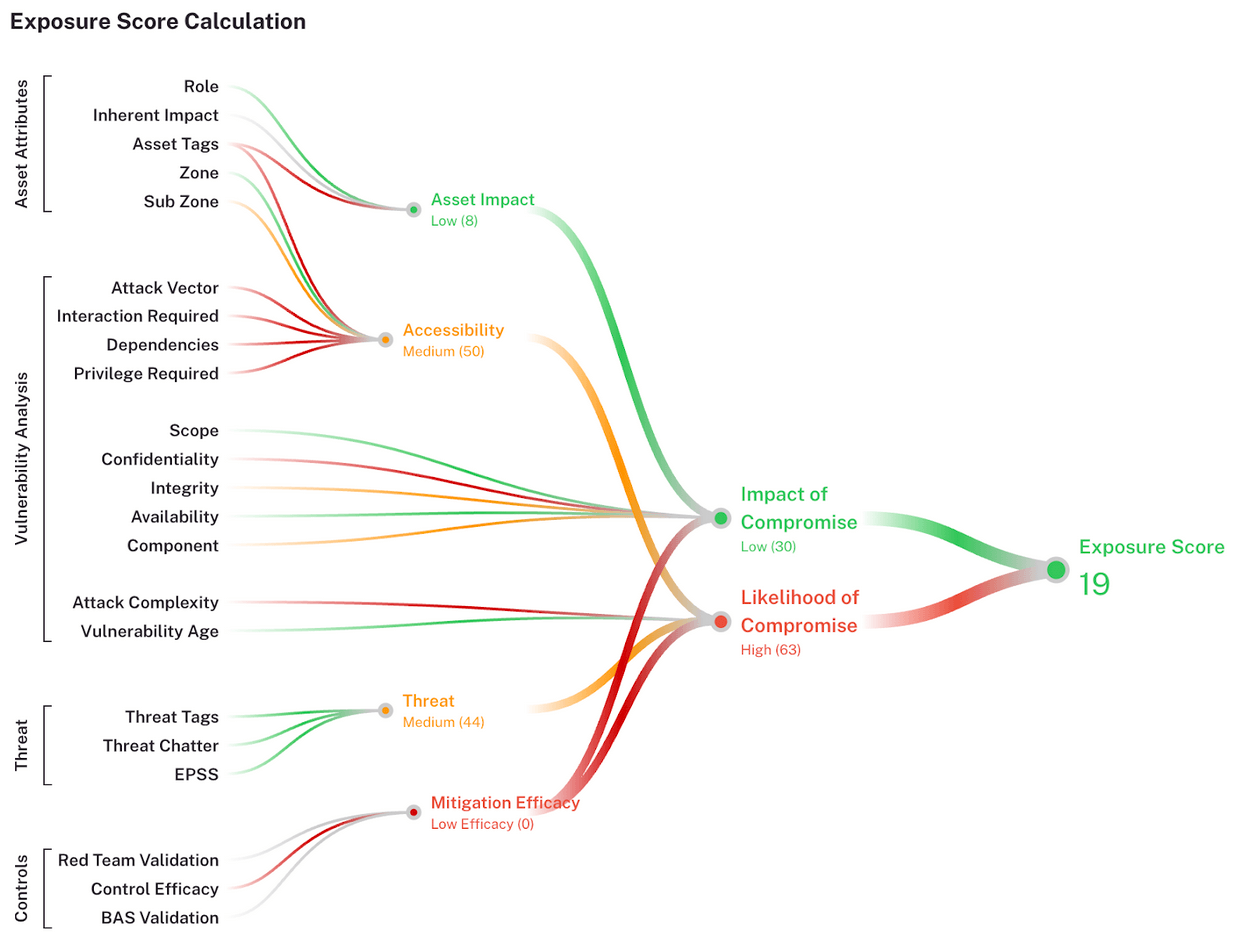
This way, Risk-Based Prioritization is proactively done, saving precious time & reducing the risk. This allows Balbix customers to simply start a Remediation Project workflow to automate, drive and manage the entire patching process – automatically calculating what patches that need to be installed on assets, cutting tickets, measuring patching progress and remediation KPIs.
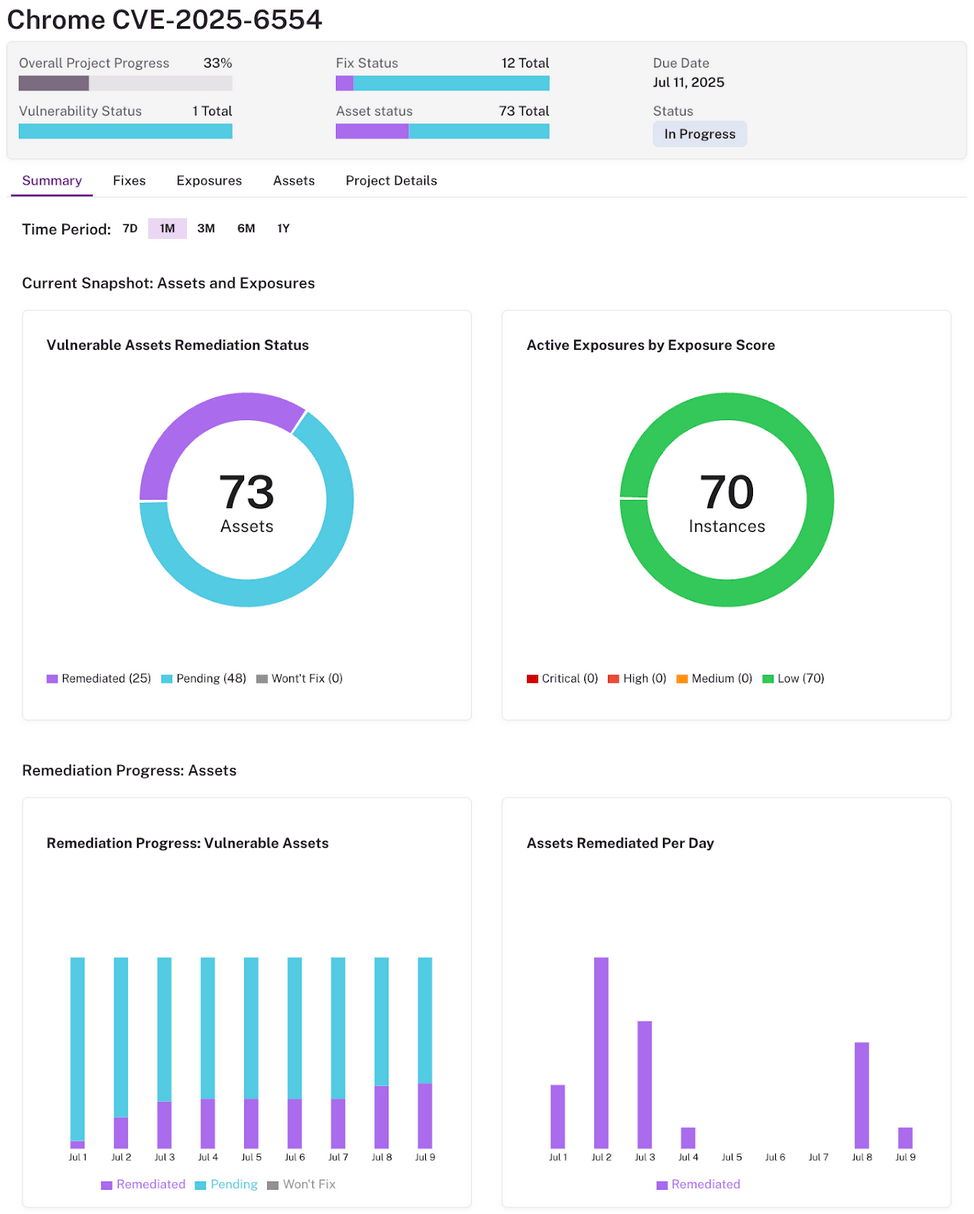
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.