October 15, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 196 CVEs, including 21 republished CVEs. Overall, Microsoft announced 3 Zero-Day, 17 Critical, and 164 Important vulnerabilities.

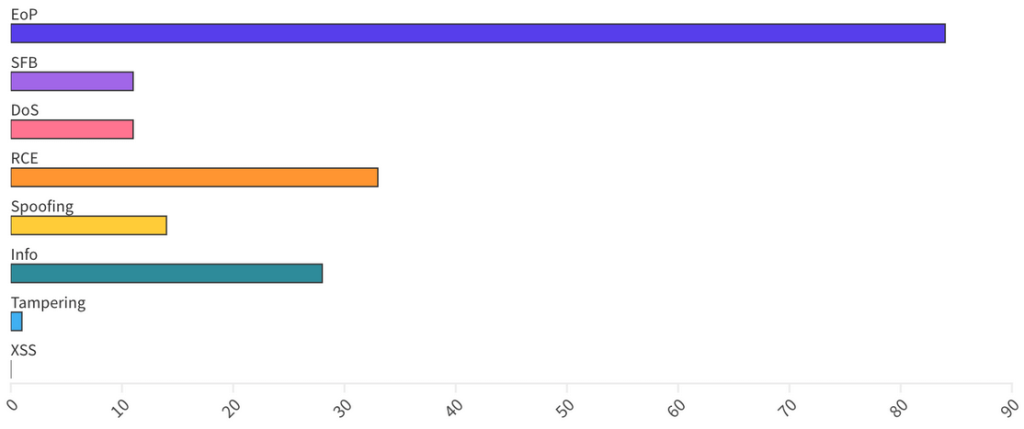
From an Impact perspective, Escalation of Privilege vulnerabilities accounted for 46%, while Remove Code Execution for 18% and Information Disclosure for 15%.
Patches for this month cover components for the following areas:
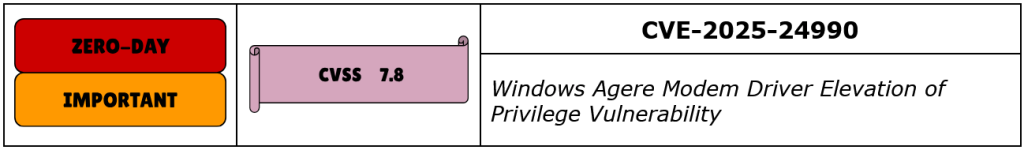
CVE-2025-24990 is an elevation-of-privilege vulnerability in a third-party Agere modem driver that ships with affected Windows releases. Microsoft describes the issue as an untrusted pointer dereference in the Agere modem driver and states that the impacted driver has been removed in the October 2025 cumulative update.
The vulnerability affects the Agere modem driver – the legacy ltmdm64.sys component that shipped with some Windows systems. Microsoft reports that an attacker with the ability to run code locally can trigger the driver to dereference attacker-controlled pointers, leading to elevation of privileges to SYSTEM. Microsoft additionally reports evidence of exploitation in the wild for CVE-2025-24990. CISA included CVE-2025-24990 in its Known Exploited Vulnerabilities catalog, and multiple industry reports confirm Microsoft’s remediation approach of removing the vulnerable driver in the October 14, 2025 Patch Tuesday updates.
Key technical attributes and impact that are stated in vendor reporting: the flaw is characterized as an untrusted pointer dereference that can be abused by a local attacker to gain administrative (SYSTEM) privileges on affected systems. Microsoft’s published fix for this issue in the October 2025 updates removes the vulnerable Agere modem driver from affected Windows releases; Microsoft warns that removing the driver will cause legacy fax/modem hardware that depends on that driver to stop functioning. Industry reporting and vendor guidance assign CVSS v3.1 a base score of 7.8 for this issue and classify it as Important; Microsoft marks the vulnerability as having been exploited in the wild.
Mitigation and remediation guidance (vendor-verified): apply the Microsoft October 14, 2025 security updates that remove the vulnerable ltmdm64.sys driver. If your environment depends on legacy modem/fax hardware that used that driver, plan for loss of that hardware’s functionality and migrate away from the dependency before applying the update or implementing compensating controls. Additional hardening recommendations include enforcing least privilege, restricting local code execution opportunities through application control (for example, Defender Application Control or AppLocker), and monitoring for post-exploitation behavior with endpoint detection tools. These mitigation steps and the removal of the driver are documented by Microsoft and reflected in multiple vendor advisories.
CVE-2025-59230 is an elevation-of-privilege vulnerability in the Windows Remote Access Connection Manager (RasMan) service that can be abused by a local attacker to gain SYSTEM privileges. Microsoft describes the underlying fault as an improper access control condition in the Remote Access Connection Manager component and reports evidence of exploitation in the wild; Microsoft issued a fix as part of the October 14, 2025 Patch Tuesday updates.
The flaw affects the Windows Remote Access Connection Manager service (RasMan) on supported Windows releases when an attacker can execute code locally and invoke the vulnerable RasMan code path. According to Microsoft’s advisory summary and multiple industry write-ups, exploitation involves an attacker invoking functionality in RasMan that lacks proper access checks; after successful exploitation a local, authorized actor can elevate privileges to SYSTEM. Microsoft and multiple vendors characterize the required attacker access as local and note that exploitation required an attacker to invest some measurable preparation or execution effort (for example, to obtain local code execution or call the vulnerable interface).
Key technical attributes and impact (vendor-verified): the issue is classified by Microsoft as an Elevation-of-Privilege (EoP) caused by improper access control in the Windows Remote Access Connection Manager. Microsoft assigns a CVSS v3.1 base score of 7.8 and rates the issue as Important. Successful exploitation permits a local attacker to gain SYSTEM privileges on affected systems, producing a change in scope to the system level and a high impact on confidentiality, integrity, and availability when successfully exploited. Microsoft confirms in-the-wild exploitation for this CVE. Microsoft’s advisory language does not publish a specific CWE identifier for this issue in the public advisory text; the vendor characterization in the advisory is “improper access control.”
Mitigation and remediation (vendor-verified): Microsoft fixed CVE-2025-59230 in the October 14, 2025 security updates for Windows that address Remote Access Connection Manager. The vendor guidance is to apply the October 14, 2025 Patch Tuesday updates from Microsoft to affected systems. As complementary mitigations, organizations should limit opportunities for local code execution (for example, via application control or least-privilege policies), monitor and alert for signs of privilege-escalation activity with EDR/telemetry, and apply standard hardening and segmentation to reduce the blast radius of a compromised local account. CISA added this vulnerability to its Known Exploited Vulnerabilities catalog, signaling prioritization for remediation in enterprise environments.
CVE-2025-47827 is a Secure Boot bypass vulnerability in IGEL OS (affecting IGEL OS versions prior to 11) that stems from improper cryptographic signature verification in the igel-flash-driver kernel module. Public vulnerability records and the original researcher’s disclosure show that the driver fails to correctly validate the signature on SquashFS root filesystem images, which can allow a crafted, unverified SquashFS image to be mounted during the boot process.
The flaw specifically impacts the igel-flash-driver code path used to verify and mount SquashFS-based root filesystems on affected IGEL OS releases. According to the public advisory and follow-up technical writeups, an attacker who can supply a malicious SquashFS image to the device (for example, via local media, network-attached storage, or an attacker-controlled provisioning image) can cause the system to accept and mount that image without a valid cryptographic signature. Mounting an attacker-controlled root filesystem in this way defeats UEFI Secure Boot protections because the chain-of-trust for the root filesystem is not enforced by the vulnerable driver.
Public analysis and the researcher’s proof-of-concept confirm that the practical consequence of successful exploitation is the ability to boot or mount an attacker-controlled root filesystem and therefore to run untrusted kernel or userspace code that would normally be blocked by Secure Boot policies. Multiple vendor and research writeups assigned a high severity rating and report an associated CVSS v3.1 base score in the high range; public advisories (including the GitHub advisory record and NVD entry) list the issue as a Secure Boot bypass and document the availability of exploit details and proof-of-concept code in the public disclosure.
Key technical attributes and impact drawn only from public vendor and researcher reporting are as follows. The vulnerability is a Secure Boot bypass caused by improper cryptographic signature verification in the igel-flash-driver module. The affected products are IGEL OS releases before version 11. The required attacker capabilities reported in public advisories are the ability to supply or cause the device to load a crafted SquashFS root filesystem image; exploitation is not a remote code execution vulnerability in the sense of a network-initiated remote exploit of a running service, but it permits execution of attacker-controlled code during boot if the attacker can deliver the crafted image. Public records list the issue as a high-severity Secure Boot bypass and link to the researcher’s PoC demonstrating the mount of an unverified SquashFS image.
Vendor remediation and mitigation that are documented in the public advisories are that IGEL OS users should upgrade to IGEL OS 11 (or later maintained releases) where the vulnerable igel-flash-driver behavior has been corrected, and that organizations should treat devices running IGEL OS versions prior to 11 as at elevated risk until they are upgraded or otherwise protected. Public guidance from security researchers and downstream advisories also recommends restricting physical and provisioning access to IGEL devices, verifying boot configuration and image sources, and monitoring for unauthorized filesystem or boot image changes while applying vendor patches or upgrades. CISA and other vulnerability trackers have cataloged the issue and flagged it for prioritization in enterprise inventories.
CVE-2025-55680 is an elevation-of-privilege vulnerability in the Windows Cloud Files Mini Filter Driver (a kernel-mode file-system mini-filter) that Microsoft and multiple industry trackers describe as a time-of-check time-of-use (TOCTOU) race condition. The flaw allows a local, authenticated attacker who can race the vulnerable code path to cause improper validation or use of file/permission state, which in turn can be abused to elevate privileges to SYSTEM.
The vulnerability specifically impacts the Cloud Files Mini Filter Driver component used by Windows to integrate cloud-backed filesystems with the OS. Public vendor summaries indicate the underlying issue is a race condition where an attacker must “win” a timing window to cause the driver to act in a stale or improperly-checked state; successful exploitation results in escalation of privileges from a local account to SYSTEM. Industry patch notes and analysts assign this issue a CVSS v3.1 base score of 7.8 (Important) and describe the exploitability requirement as a local race (TOCTOU) that increases complexity compared with a simple local code execution bug, but which is nevertheless practicable under the right conditions.
Microsoft addressed CVE-2025-55680 in the October 14, 2025 Patch Tuesday security updates for Windows; public write-ups from multiple security vendors note Microsoft’s remediation and rate the issue among the Important elevation-of-privilege fixes in that release. Because exploitation requires a local race, recommended mitigations are to apply the October 14, 2025 security updates immediately, reduce opportunities for local code execution through application control and least-privilege policies (for example Defender Application Control or AppLocker), and monitor endpoints for post-exploitation behaviors using EDR tooling. Multiple patch analyses also flag this class of Cloud Files mini-filter defects as “Exploitation More Likely” for this Patch Tuesday cycle, reinforcing the priority for remediation.
Key technical attributes (vendor-sourced): CWE: race condition / TOCTOU (time-of-check time-of-use) leading to elevation-of-privilege. CVSS v3.1 Base Score: 7.8 (Important). Vector: Local; Attack Complexity: Requires winning a race condition; Privileges Required: Local authenticated user; User Interaction: Not required beyond local access/interaction needed to trigger the race; Scope: Changed (system-level privilege gain on success); Impact: High for Confidentiality, Integrity, and Availability when exploited. Microsoft’s public guidance is to apply the October 14, 2025 Windows security updates.
CVE-2025-49708 is a use-after-free vulnerability (CWE-416) in the Microsoft Graphics Component that can be abused to achieve remote code execution and elevation of privileges on affected Windows systems. Microsoft’s Security Update Guide lists the vulnerability in the October 14, 2025 Patch Tuesday release, and vendor and analyst write-ups describe the root cause as a use-after-free in the graphics processing path that an attacker can trigger remotely; successful exploitation can lead to code execution with SYSTEM-level impact.
The flaw affects the Microsoft Graphics Component used by Windows to process images and other graphics content. Public advisories and multiple incident analyses report that an attacker who can send specially crafted graphics content to a vulnerable host (over the network) and who meets the low privilege requirements noted by vendors can trigger the use-after-free to corrupt memory and redirect execution. Multiple high-quality coverage pieces and vendor summaries indicate the vulnerability is exploitable over the network and that exploitation can result in a scope change to system-level privileges; Microsoft included the fix for this issue in the October 14, 2025 security updates.
Key technical attributes: CWE ID: CWE-416 — Use-After-Free. CVSS v3.1 Base Score and severity as published in public advisories and aggregations: 9.9 (Critical) with vector CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H as shown in the GitHub advisory and reflected in vendor summaries. Attack Vector: Network (remote). Attack Complexity: Low. Privileges Required: Low (an attacker is required to have at most low privileges per the published vector). User Interaction: None. Scope: Changed (successful exploitation can impact system-level resources). Impact: High across Confidentiality, Integrity, and Availability.
Mitigation and remediation guidance (vendor-verified): apply the October 14, 2025 Microsoft security updates that address CVE-2025-49708 as soon as possible. Microsoft’s Security Update Guide lists the CVE and the October 2025 fixes; multiple industry analyses and patch summaries likewise recommend immediate installation of the relevant Windows updates and emphasize prioritization because the issue enables remote, network-accessible code execution with SYSTEM impact. As complementary controls until patches are applied, organizations should reduce the attack surface exposed to untrusted graphics content (for example, block or filter untrusted network ingestion of image/graphics payloads at network edges and gateways), enforce least privilege and application control to limit local attack vectors, and monitor endpoint telemetry for suspicious post-exploitation behavior.
| CVE | Severity | Type | CVSS | Exploitation |
|---|---|---|---|---|
| CVE-2025-24052 | Important | EoP | 7.8 | More Likely |
| CVE-2025-24990 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-25004 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-47979 | Important | Info | 5.5 | Less Likely |
| CVE-2025-47989 | Important | EoP | 7 | Unlikely |
| CVE-2025-48004 | Important | EoP | 7.4 | More Likely |
| CVE-2025-48813 | Important | Spoofing | 6.3 | Less Likely |
| CVE-2025-49708 | Critical | RCE | 9.9 | Less Likely |
| CVE-2025-50152 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-50174 | Important | EoP | 7 | Less Likely |
| CVE-2025-50175 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-53139 | Important | SFB | 7.7 | Less Likely |
| CVE-2025-53150 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53717 | Important | EoP | 7 | Less Likely |
| CVE-2025-53768 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-53782 | Important | EoP | 8.4 | Less Likely |
| CVE-2025-55240 | Important | EoP | 7.3 | Unlikely |
| CVE-2025-55247 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-55248 | Important | Info | 4.8 | Less Likely |
| CVE-2025-55315 | Important | SFB | 9.9 | Less Likely |
| CVE-2025-55320 | Important | EoP | 7.2 | Less Likely |
| CVE-2025-55321 | Critical | Spoofing | 8.7 | Less Likely |
| CVE-2025-55325 | Important | Info | 5.5 | Less Likely |
| CVE-2025-55326 | Important | RCE | 7.5 | Less Likely |
| CVE-2025-55328 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-55330 | Important | SFB | 6.1 | Less Likely |
| CVE-2025-55331 | Important | EoP | 7 | Unlikely |
| CVE-2025-55332 | Important | SFB | 6.1 | Less Likely |
| CVE-2025-55333 | Important | SFB | 6.1 | Less Likely |
| CVE-2025-55334 | Important | SFB | 6.2 | Less Likely |
| CVE-2025-55335 | Important | EoP | 7.4 | Less Likely |
| CVE-2025-55336 | Important | Info | 5.5 | Less Likely |
| CVE-2025-55337 | Important | SFB | 6.1 | Less Likely |
| CVE-2025-55338 | Important | SFB | 6.1 | Less Likely |
| CVE-2025-55339 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-55340 | Important | SFB | 7 | Unlikely |
| CVE-2025-55676 | Important | Info | 5.5 | More Likely |
| CVE-2025-55677 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-55678 | Important | EoP | 7 | Less Likely |
| CVE-2025-55679 | Important | Info | 5.1 | Unlikely |
| CVE-2025-55680 | Important | EoP | 8.4 | More Likely |
| CVE-2025-55681 | Important | EoP | 7 | More Likely |
| CVE-2025-55682 | Important | SFB | 6.1 | Less Likely |
| CVE-2025-55683 | Important | Info | 5.5 | Less Likely |
| CVE-2025-55684 | Important | EoP | 7 | Less Likely |
| CVE-2025-55685 | Important | EoP | 7 | Less Likely |
| CVE-2025-55686 | Important | EoP | 7 | Less Likely |
| CVE-2025-55687 | Important | EoP | 7.4 | Less Likely |
| CVE-2025-55688 | Important | EoP | 7 | Less Likely |
| CVE-2025-55689 | Important | EoP | 7 | Less Likely |
| CVE-2025-55690 | Important | EoP | 7 | Less Likely |
| CVE-2025-55691 | Important | EoP | 7 | Less Likely |
| CVE-2025-55692 | Important | EoP | 7.8 | More Likely |
| CVE-2025-55693 | Important | EoP | 7.4 | More Likely |
| CVE-2025-55694 | Important | EoP | 7.8 | More Likely |
| CVE-2025-55695 | Important | Info | 5.5 | Unlikely |
| CVE-2025-55696 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-55697 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-55698 | Important | DoS | 7.7 | Less Likely |
| CVE-2025-55699 | Important | Info | 5.5 | Less Likely |
| CVE-2025-55700 | Important | Info | 6.5 | Less Likely |
| CVE-2025-55701 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-58714 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-58715 | Important | EoP | 8.8 | Unlikely |
| CVE-2025-58716 | Important | EoP | 8.8 | Unlikely |
| CVE-2025-58717 | Important | Info | 6.5 | Less Likely |
| CVE-2025-58718 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-58719 | Important | EoP | 4.7 | Unlikely |
| CVE-2025-58720 | Important | Info | 7.8 | Less Likely |
| CVE-2025-58722 | Important | EoP | 7.8 | More Likely |
| CVE-2025-58724 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-58725 | Important | EoP | 7 | Less Likely |
| CVE-2025-58726 | Important | EoP | 7.5 | Less Likely |
| CVE-2025-58727 | Important | EoP | 7 | Less Likely |
| CVE-2025-58728 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-58729 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-58730 | Important | RCE | 7 | Unlikely |
| CVE-2025-58731 | Important | RCE | 7 | Unlikely |
| CVE-2025-58732 | Important | RCE | 7 | Unlikely |
| CVE-2025-58733 | Important | RCE | 7 | Unlikely |
| CVE-2025-58734 | Important | RCE | 7 | Unlikely |
| CVE-2025-58735 | Important | RCE | 7 | Unlikely |
| CVE-2025-58736 | Important | RCE | 7 | Unlikely |
| CVE-2025-58737 | Important | RCE | 7 | Unlikely |
| CVE-2025-58738 | Important | RCE | 7 | Unlikely |
| CVE-2025-58739 | Important | Spoofing | 6.5 | Less Likely |
| CVE-2025-59184 | Important | Info | 5.5 | Less Likely |
| CVE-2025-59185 | Important | Spoofing | 6.5 | Less Likely |
| CVE-2025-59186 | Important | Info | 5.5 | Less Likely |
| CVE-2025-59187 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59188 | Important | Info | 5.5 | Less Likely |
| CVE-2025-59189 | Important | EoP | 7.4 | Unlikely |
| CVE-2025-59190 | Important | DoS | 5.5 | Unlikely |
| CVE-2025-59191 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59192 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59193 | Important | EoP | 7 | Less Likely |
| CVE-2025-59194 | Important | EoP | 7 | More Likely |
| CVE-2025-59195 | Important | DoS | 7 | Less Likely |
| CVE-2025-59196 | Important | EoP | 7 | Unlikely |
| CVE-2025-59197 | Important | Info | 5.5 | Less Likely |
| CVE-2025-59198 | Important | DoS | 5 | Unlikely |
| CVE-2025-59199 | Important | EoP | 8.4 | More Likely |
| CVE-2025-59200 | Important | Spoofing | 7.7 | Less Likely |
| CVE-2025-59201 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59202 | Important | EoP | 7 | Less Likely |
| CVE-2025-59203 | Important | Info | 5.5 | Less Likely |
| CVE-2025-59204 | Important | Info | 5.5 | Unlikely |
| CVE-2025-59205 | Important | EoP | 7 | Less Likely |
| CVE-2025-59206 | Important | EoP | 7.4 | Unlikely |
| CVE-2025-59207 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59208 | Important | Info | 7.1 | Less Likely |
| CVE-2025-59209 | Important | Info | 5.5 | Unlikely |
| CVE-2025-59210 | Important | EoP | 7.4 | Unlikely |
| CVE-2025-59211 | Important | Info | 5.5 | Unlikely |
| CVE-2025-59213 | Important | EoP | 8.4 | Less Likely |
| CVE-2025-59214 | Important | Spoofing | 6.5 | Unlikely |
| CVE-2025-59218 | Critical | EoP | 9.6 | Less Likely |
| CVE-2025-59221 | Important | RCE | 7 | Unlikely |
| CVE-2025-59222 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-59223 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-59224 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-59225 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-59226 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-59227 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-59228 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-59229 | Important | DoS | 5.5 | Unlikely |
| CVE-2025-59230 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-59231 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-59232 | Important | Info | 7.1 | Unlikely |
| CVE-2025-59233 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-59234 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-59235 | Important | Info | 7.1 | Unlikely |
| CVE-2025-59236 | Critical | RCE | 8.4 | Unlikely |
| CVE-2025-59237 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-59238 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-59241 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59242 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59243 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-59244 | Important | Spoofing | 6.5 | Less Likely |
| CVE-2025-59246 | Critical | EoP | 9.8 | More Likely |
| CVE-2025-59247 | Critical | EoP | 8.8 | Less Likely |
| CVE-2025-59248 | Important | Spoofing | 7.5 | Less Likely |
| CVE-2025-59249 | Important | EoP | 8.8 | Unlikely |
| CVE-2025-59250 | Important | Spoofing | 8.1 | Less Likely |
| CVE-2025-59252 | Critical | Spoofing | 6.5 | Less Likely |
| CVE-2025-59253 | Important | DoS | 5.5 | Less Likely |
| CVE-2025-59254 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-59255 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-59257 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-59258 | Important | Info | 6.2 | Less Likely |
| CVE-2025-59259 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-59260 | Important | Info | 5.5 | Less Likely |
| CVE-2025-59261 | Important | EoP | 7 | Unlikely |
| CVE-2025-59271 | Critical | EoP | 8.7 | Less Likely |
| CVE-2025-59272 | Critical | Spoofing | 6.5 | Less Likely |
| CVE-2025-59275 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59277 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59278 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59280 | Important | Tampering | 3.1 | Less Likely |
| CVE-2025-59281 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59282 | Important | RCE | 7 | Unlikely |
| CVE-2025-59284 | Important | Spoofing | 3.3 | Less Likely |
| CVE-2025-59285 | Important | EoP | 7 | Unlikely |
| CVE-2025-59286 | Critical | Spoofing | 6.5 | Less Likely |
| CVE-2025-59287 | Critical | RCE | 9.8 | More Likely |
| CVE-2025-59288 | Moderate | Spoofing | 5.3 | Less Likely |
| CVE-2025-59289 | Important | EoP | 7 | Less Likely |
| CVE-2025-59290 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59291 | Critical | EoP | 8.2 | Less Likely |
| CVE-2025-59292 | Critical | EoP | 8.2 | Less Likely |
| CVE-2025-59294 | Important | Info | 2.1 | Unlikely |
| CVE-2025-59295 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-59494 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-59497 | Important | DoS | 7 | Less Likely |
| CVE-2025-59502 | Important | DoS | 7.5 | More Likely |
| CVE-2016-9535 | Critical | RCE | 4 | Unlikely |
| CVE-2025-0033 | Critical | RCE | 8.2 | Less Likely |
| CVE-2025-11205 | High | N/A | N/A | — |
| CVE-2025-11206 | High | N/A | N/A | — |
| CVE-2025-11207 | Medium | N/A | N/A | — |
| CVE-2025-11208 | Medium | N/A | N/A | — |
| CVE-2025-11209 | Medium | N/A | N/A | — |
| CVE-2025-11210 | Medium | N/A | N/A | — |
| CVE-2025-11211 | Medium | N/A | N/A | — |
| CVE-2025-11212 | Medium | N/A | N/A | — |
| CVE-2025-11213 | Medium | N/A | N/A | — |
| CVE-2025-11215 | Medium | N/A | N/A | — |
| CVE-2025-11216 | Low | N/A | N/A | — |
| CVE-2025-11219 | Low | N/A | N/A | — |
| CVE-2025-11458 | High | N/A | N/A | — |
| CVE-2025-11460 | High | N/A | N/A | — |
| CVE-2025-2884 | Important | Info | 5.3 | Less Likely |
| CVE-2025-47827 | Important | SFB | 4.6 | KNOWN EXPLOIT |
| CVE-2025-54132 | Important | Info | 4.4 | Less Likely |
| CVE-2025-54957 | Important | RCE | 7 | Less Likely |
| CVE-2025-59489 | Important | EoP | 8.4 | — |
CHROME – As of October 14, 2025, Google released a Chrome security update addressing multiple vulnerabilities, including a critical heap buffer overflow in the Sync component and a use-after-free flaw in the Storage component. These vulnerabilities could allow attackers to execute arbitrary code in the browser process.
CVE-2025-1195777 is a heap buffer overflow vulnerability in Chrome’s Sync component, identified as CWE-122. The flaw occurs when Sync parsers allocate memory on the heap and subsequently write more data than the allocated buffer can hold, leading to memory corruption and potential control-flow hijacking. This vulnerability affects multiple Chrome components—including Sync—when processing specially crafted data. Common triggers include incorrect length or size fields in embedded content, integer arithmetic errors that result in under-allocated buffers, and incomplete bounds checks during decompression or copy operations. When exploited, the overflow can corrupt adjacent heap metadata or overwrite function pointers and vtable entries. If the attacker controls the overwritten data, they may redirect execution to attacker-controlled memory, resulting in arbitrary code execution within the context of the Chrome process.
CVE-2025-10585 is a type confusion vulnerability in Chrome’s V8 JavaScript engine, identified as CWE-843. The flaw occurs when V8 incorrectly interprets the type of an object, leading to unexpected behavior and potential memory corruption. Successful exploitation of this vulnerability allows an attacker to potentially exploit heap corruption via a crafted HTML page. Google addressed CVE-2025-10585 in the September 2025 Patch Tuesday update, which includes improved type handling and validation in the V8 engine. Mitigation guidance includes applying the September 2025 Chrome security updates immediately and exercising caution when interacting with untrusted web content.
CVE-2025-8292 is a use-after-free vulnerability in Chrome’s Media Stream component, identified as CWE-416. The flaw occurs when Media Stream objects are used after they have been freed, leading to potential memory corruption and arbitrary code execution. Successful exploitation of this vulnerability allows a remote attacker to potentially exploit heap corruption via a crafted HTML page.
CVE-2025-9864 is a use-after-free vulnerability in Chrome’s V8 JavaScript engine, identified as CWE-416. The flaw occurs when V8 objects are used after they have been freed, leading to potential memory corruption and arbitrary code execution. Successful exploitation of this vulnerability allows a remote attacker to potentially exploit heap corruption via a crafted HTML page.
CVE-2025-10502 is a heap buffer overflow vulnerability in Chrome’s ANGLE graphics library, identified as CWE-122. The flaw occurs when ANGLE processes certain graphics data without sufficient bounds checking, leading to potential memory corruption and arbitrary code execution. Successful exploitation of this vulnerability allows a remote attacker to potentially exploit heap corruption via malicious network traffic.
CISCO – As of October 14, 2025, Cisco has released several security advisories addressing critical vulnerabilities across its product line, including DoS issues in IOS and IOS XE software, and XSS vulnerabilities in Cyber Vision Center and Unified Communications Manager.
CVE-2025-20352 is a denial of service vulnerability in Cisco IOS and IOS XE Software’s SNMP implementation, identified as CWE-121. The flaw occurs when the software improperly handles SNMP requests, leading to a buffer overflow and potential device crash. An unauthenticated, remote attacker could exploit this vulnerability by sending crafted SNMP packets to an affected device, causing a denial of service condition. Cisco has released software updates to address this vulnerability. There are no workarounds available.
CVE-2025-20225 and CVE-2025-20239 are memory leak vulnerabilities in the Internet Key Exchange Version 2 (IKEv2) feature of Cisco IOS Software, IOS XE Software, Secure Firewall ASA Software, and Secure FTD Software, identified as CWE-401. The flaws occur due to improper processing of IKEv2 packets, leading to memory leaks and potential device reloads. An unauthenticated, remote attacker could exploit these vulnerabilities by sending crafted IKEv2 packets to an affected device, causing a denial of service condition. Cisco has released software updates to address these vulnerabilities. There are no workarounds available.
CVE-2025-20356 and CVE-2025-20357 are stored cross-site scripting vulnerabilities in Cisco Cyber Vision Center, identified as CWE-79. The flaws occur when the software improperly sanitizes user-supplied input, allowing an attacker to inject malicious scripts into web pages viewed by other users. An attacker could exploit these vulnerabilities by persuading a user to click on a crafted link, executing arbitrary JavaScript in the user’s browser. Cisco has released software updates to address these vulnerabilities.
CVE-2025-20361 is a stored cross-site scripting vulnerability in Cisco Unified Communications Manager, identified as CWE-79. The flaw occurs when the software improperly sanitizes user-supplied input, allowing an attacker to inject malicious scripts into web pages viewed by other users. An attacker could exploit this vulnerability by persuading a user to click on a crafted link, executing arbitrary JavaScript in the user’s browser. Cisco has released software updates to address this vulnerability.
CVE-2025-20160 is a TACACS+ authentication bypass vulnerability in Cisco IOS and IOS XE Software, identified as CWE-287. The flaw occurs due to improper handling of authentication requests, allowing an attacker to bypass authentication and gain unauthorized access to the system. An attacker could exploit this vulnerability by sending specially crafted TACACS+ packets to an affected device. Cisco has released software updates to address this vulnerability. There are no workarounds available.
FORTINET – As of October 14, 2025, Fortinet has disclosed several critical vulnerabilities across its product suite, including issues in FortiOS CLI command handling, SSL VPN RDP bookmark functionality, and GUI access controls.
CVE-2025-58325, disclosed on October 14, 2025, is a high-severity privilege escalation vulnerability in FortiOS. Authenticated users can bypass CLI command restrictions, potentially executing unauthorized system commands. This flaw affects FortiOS versions 7.0.0 through 7.0.16 and 7.2.0 through 7.2.12. Fortinet has released patches to address this issue. No workarounds are available.
CVE-2025-57740, also disclosed on October 14, 2025, is a heap-based buffer overflow vulnerability in the RDP bookmark feature of Fortinet’s SSL VPN. An authenticated user can exploit this flaw by sending specially crafted requests during RDP bookmark connection establishment, leading to potential remote code execution. Affected products include FortiOS, FortiPAM, and FortiProxy. Fortinet has issued patches to mitigate this vulnerability.
CVE-2025-54822, disclosed on October 14, 2025, is a medium-severity access control vulnerability in the FortiOS GUI. An attacker can exploit this flaw to access static files without proper authorization, potentially leading to information disclosure. Fortinet has provided guidance to address this issue.
CVE-2025-58903, also disclosed on October 14, 2025, is a low-severity denial-of-service vulnerability in the FortiOS GUI. An attacker can exploit this flaw to cause a denial of service condition, affecting the availability of the GUI. Fortinet has released a fix to mitigate this vulnerability.
CVE-2025-32756, disclosed on May 13, 2025, is a critical stack-based buffer overflow vulnerability in FortiVoice, FortiMail, FortiNDR, FortiRecorder, and FortiCamera. An unauthenticated attacker can exploit this flaw to execute arbitrary code or commands via specially crafted HTTP requests, leading to potential remote code execution. Fortinet has issued patches to address this vulnerability.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by automation and AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix risk scores.
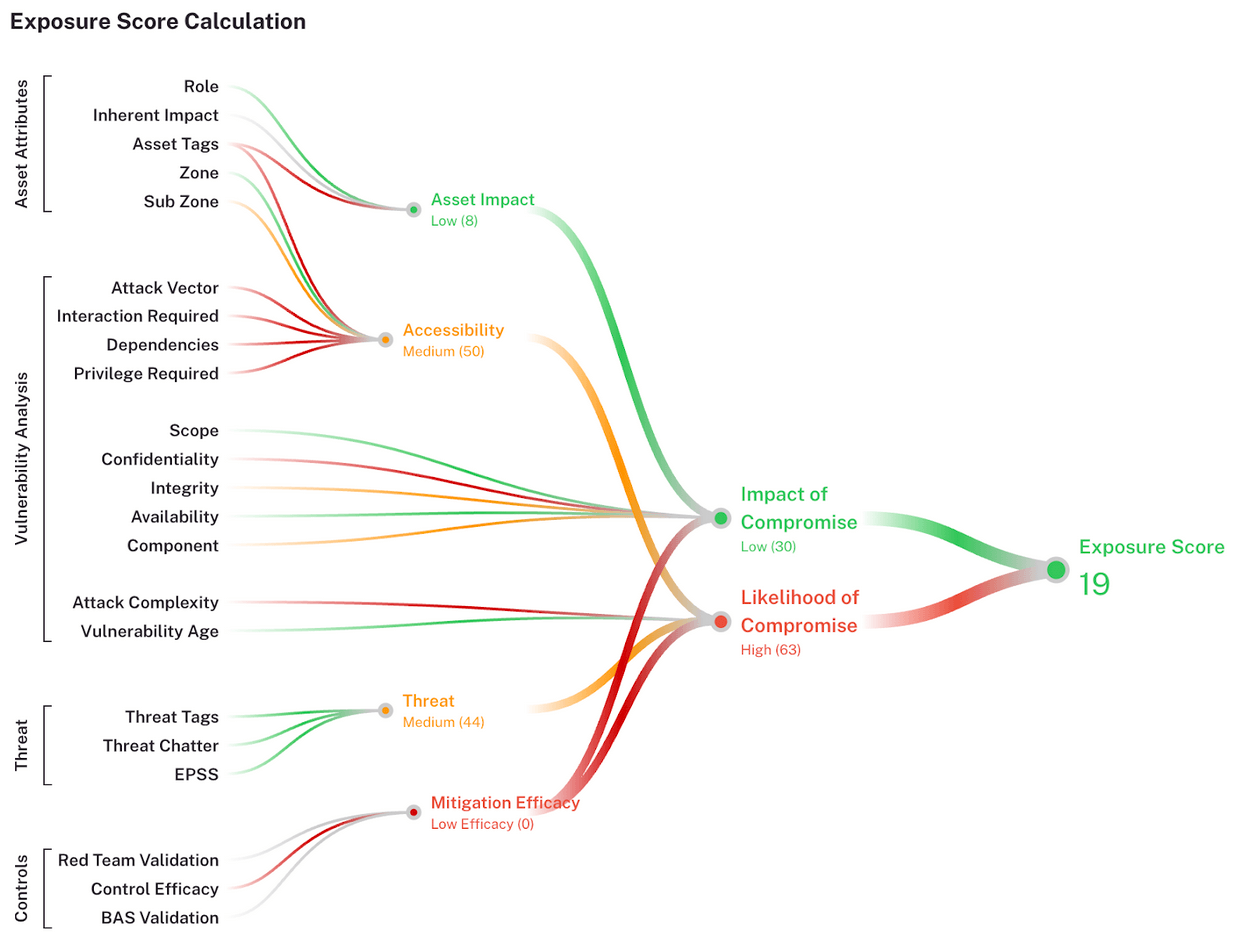
This way, Risk-Based Prioritization is proactively done, saving precious time & reducing the risk. This allows Balbix customers to simply start a Remediation Project workflow to automate, drive and manage the entire patching process – automatically calculating what patches that need to be installed on assets, cutting tickets, measuring patching progress and remediation KPIs.
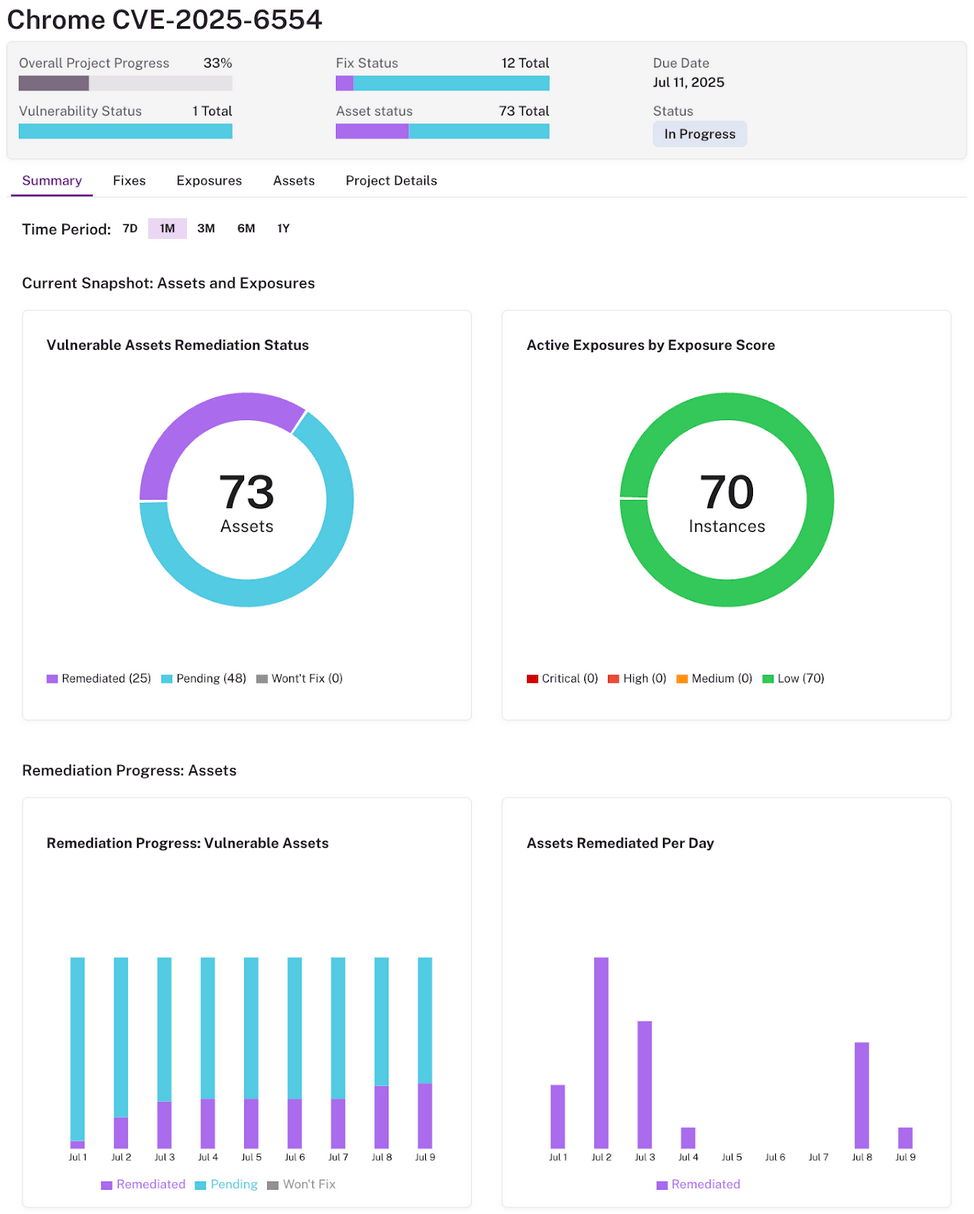
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.