
October 12, 2023
Whether you celebrate Halloween, Día de los Muertos, Guy Fawkes Day (although we’re a little early there), or celebrate something else or nothing at all, there is no denying the security landscape continues to be spooky. Hopefully, this note will help dispel some fear and shed much-needed light on the areas for remediation.
Microsoft announced fixes for 104 new CVEs this month, including 12 Microsoft-rated critical vulnerabilities. This month, 3 new zero-day vulnerabilities were disclosed (as well as an update to 1 previously disclosed zero-day from September 2023). Also, there were updates to 15 previously reported CVEs and 2 previously released advisories. (see the full list on the Microsoft Security Response Center (MSRC)
Of the 104 new vulnerabilities, the fix sources break down as follows:
This month’s headline continues to be the release of zero-day vulnerabilities, where there were three new zero-days this month (CVE-2023-44487, CVE-2023-36563, CVE-2023-41763).
The first of these vulnerabilities, CVE-2023-44487, is a significant Distributed Denial of Service Attack (DDoS) most prominently launched against Google who defeated a peak of 398 million Requests Per Second (rps). See the following article by Google for more information on the technical specifics of this attack. Thus, this vulnerability bears very close attention.
The second zero-day vulnerability (CVE-2023-36563) impacts Microsoft WordPad, which is installed on nearly every Microsoft OS installation, as it is a default package unless explicitly removed. However, the risk, while significant (could allow the disclosure of NTLM hashes (although superseded by Kerberos Auth now), but it does require the user to take explicit action. Specifically, an attacker must send the user a malicious file and convince them to open it.
Finally, the third zero-day vulnerability (CVE-2023-41763) affects Skype for Business. In this vulnerability, an attacker would need to make a specially crafted network call to the target Skype for Business server. This could cause the parsing of an HTTP request made to an arbitrary address disclosing IP addresses, port numbers, or both to the attacker.
So what’s the moral of looking at these three vulnerabilities? I’ve said this before, but it bears repeating.. after all.. repetition drives retention: Vigilance is paramount. Attacks are constantly coming from varied vectors and have very little pattern as to when or how they appear. So solid cyber-hygiene is a critical habit to build.
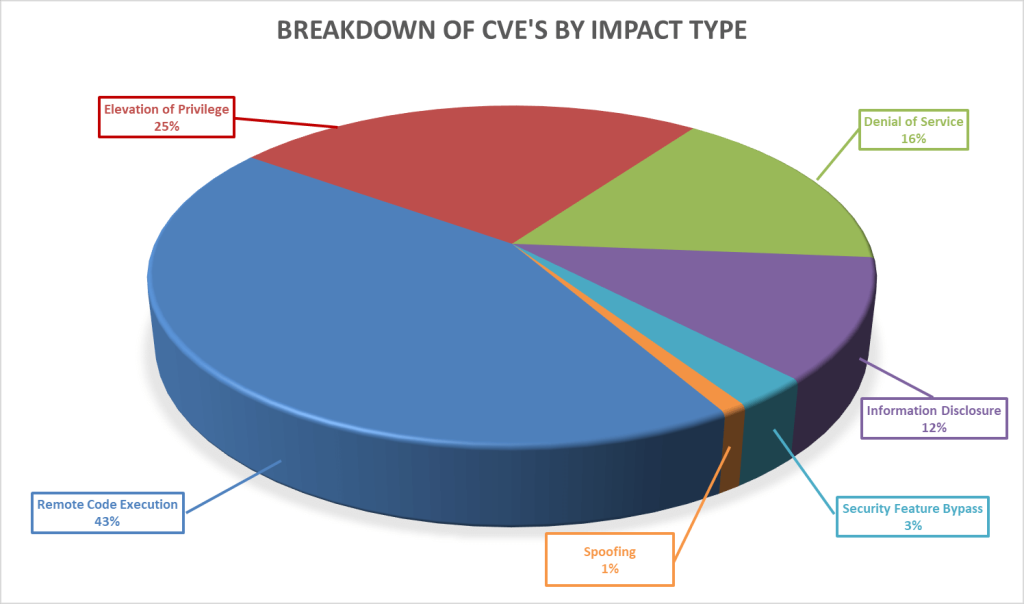
Breaking down the complete set of 104 vulnerabilities further by impact type, we can see that remote code execution again leads the way this month, with an elevation of privilege again following behind it.
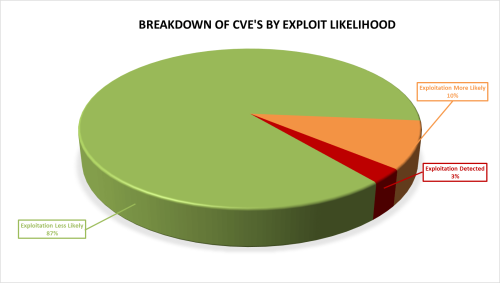
Furthermore, as seen below, these vulnerabilities vary in how likely they are to be exploited, with 13% of the vulnerabilities this month either already exploited or highly likely to be exploited, as ranked by the Microsoft Exploitability Index.
As always, Balbix can identify all affected assets within hours of release. There are no scans to run. Balbix customers simply search for the CVE name in their Balbix dashboard to view the list of affected assets. Filtered search functionality can also be used to search for the CVE by site, subnet, location, or other distinguishing factors.
If you have additional questions, please contact support@balbix.com.