
May 14, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 83 CVEs, including 5 republished CVEs. Overall, Microsoft announced 5 Zero-Day, 11 Critical, and 66 Important vulnerabilities.

From an Impact perspective, Remote Code Execution vulnerabilities accounted for 39%, followed by Escalation of Privilege at 28% and Information Disclosure at 20%.
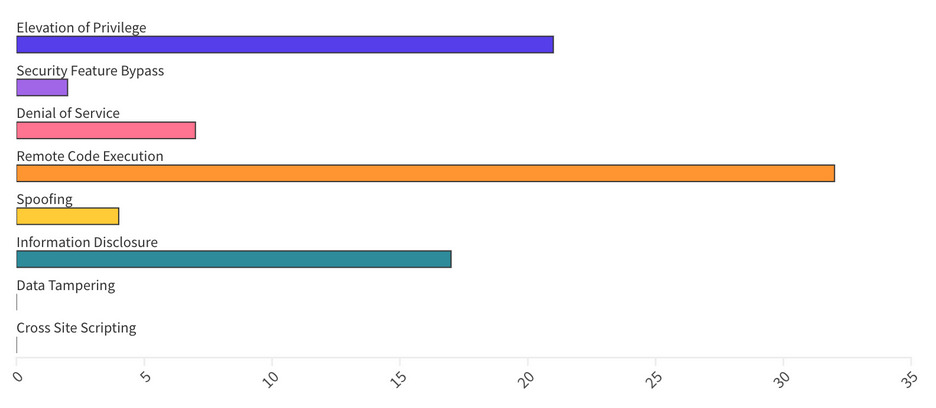
Patches for this month cover components for the following areas:
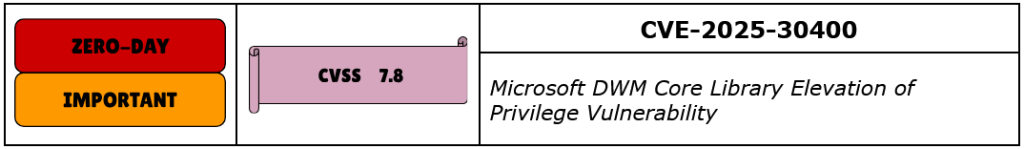
CVE-2025-30400 is a high-severity use-after-free vulnerability in the Desktop Window Manager (DWM) core library, which is responsible for composing and rendering the graphical desktop environment in Windows. The vulnerability stems from improper management of reference-counted objects within the DWM process, specifically during operations related to composition surfaces and window transitions. When a low-privilege user initiates certain graphical actions – such as creating and destroying windows in a carefully timed sequence – it is possible to trigger a race condition that causes an object to be freed prematurely while a reference to it is still active. Subsequent access to the stale pointer results in a use-after-free condition, allowing controlled corruption of the process heap.
Because DWM runs in a highly privileged user-mode context (SYSTEM), successful exploitation enables local attackers to escalate their privileges to the highest level. No user interaction is required, and the vulnerability is exploitable by any authenticated local user capable of making standard GUI system calls. The vulnerability has been actively exploited in the wild, reportedly integrated into post-exploitation toolchains for lateral movement and persistence. Microsoft assigned a CVSS v3.1 score of 7.8 and released a patch addressing the flaw by reinforcing reference tracking and synchronization mechanisms within the DWM subsystem.
Given the elevated privileges and critical role of DWM, prompt application of the security update is essential to mitigate the risk of full system compromise. CISA added the CVE-2025-30400 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before June 3, 2025.
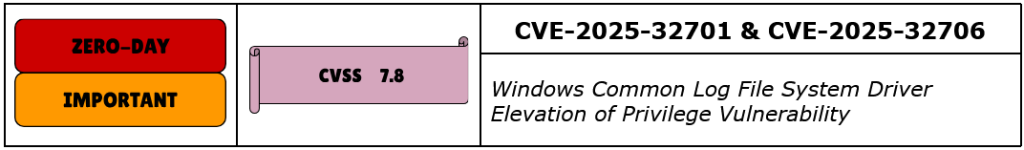
CVE-2025-32701 is a use-after-free vulnerability in the Windows Common Log File System (CLFS) driver, which is responsible for managing transactional log files in the operating system. The vulnerability arises from improper handling of memory allocation and deallocation within the CLFS driver. Specifically, under certain conditions, the driver may access memory after it has been freed, leading to memory corruption. An attacker with local access and low privileges can exploit this flaw to execute arbitrary code in kernel mode, effectively elevating their privileges to SYSTEM. This vulnerability has been actively exploited in the wild, as confirmed by Microsoft and CISA. Microsoft assigned a CVSS v3.1 base score of 7.8 to this vulnerability.
CVE-2025-32706 is a heap-based buffer overflow vulnerability in the Windows Common Log File System (CLFS) driver. The flaw is due to improper input validation, allowing an attacker to write beyond the bounds of allocated memory. By carefully crafting input data, a local attacker with low privileges can exploit this vulnerability to execute arbitrary code in kernel mode, leading to privilege escalation to SYSTEM. This vulnerability has also been actively exploited in the wild and was patched by Microsoft in the May 2025 security updates. It has a CVSS v3.1 score of 7.8.
Both vulnerabilities highlight the critical importance of robust memory management and input validation in kernel-mode drivers. Given their active exploitation and potential for full system compromise, these vulnerabilities should be prioritized and patching applied as soon as possible.

CVE-2025-32709 is a use-after-free vulnerability in the Windows Ancillary Function Driver for WinSock (AFD.sys), a kernel-mode component responsible for managing socket operations and network I/O. The flaw stems from improper handling of memory deallocation in the AFD driver, leading to a use-after-free condition. An attacker with local access and low privileges can exploit this vulnerability to execute arbitrary code in kernel mode, effectively elevating their privileges to administrator.
This vulnerability has been assigned a CVSS v3.1 base score of 7.8 and has been actively exploited in the wild, as confirmed by Microsoft and CISA, who added it to its Known Exploited Vulnerabilities Catalog, mandating federal agencies to apply mitigations by June 3, 2025. Given the elevated privileges and critical role of the AFD driver, prompt application of the security update is essential to mitigate the risk of system compromise.

CVE-2025-30397 is a type confusion vulnerability in the Microsoft Scripting Engine, which can lead to remote code execution (RCE). The flaw arises when the engine accesses a resource using an incompatible type, allowing an attacker to execute arbitrary code over a network. Microsoft assigned a CVSS v3.1 base score of 7.5 to this vulnerability.
Exploitation of CVE-2025-30397 requires a user to interact with malicious content, such as clicking on a crafted URL, especially when running Microsoft Edge in Internet Explorer mode.

CVE-2025-26685 is a spoofing vulnerability in Microsoft Defender for Identity (MDI), stemming from improper authentication mechanisms within the product. This flaw allows an unauthorized attacker on an adjacent network to impersonate legitimate services or users, potentially leading to unauthorized access or information disclosure. The vulnerability has been assigned a CVSS v3.1 base score of 6.5, indicating a medium severity level.
The vulnerability can be exploited when MDI improperly handles authentication requests, particularly in scenarios where legacy protocols like NTLM are used. An attacker could exploit this by initiating a fallback from Kerberos to NTLM, thereby capturing NTLM hashes of privileged accounts, such as the Directory Service Account used by MDI. This could facilitate lateral movement within the network, undermining the security posture of the organization.
Administrators are advised to apply the latest security updates promptly and to review authentication configurations, ensuring that legacy protocols like NTLM are disabled where possible. Additionally, organizations should monitor for unusual authentication patterns that may indicate exploitation attempts.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2025-21264 | Important | SFB | 6.7 | Less Likely |
| CVE-2025-24063 | Important | EoP | 7.8 | More Likely |
| CVE-2025-26646 | Important | Spoofing | 8 | Unlikely |
| CVE-2025-26677 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-26684 | Important | EoP | 6.7 | Unlikely |
| CVE-2025-26685 | Important | Spoofing | 6.5 | Unlikely |
| CVE-2025-27468 | Important | EoP | 7 | Less Likely |
| CVE-2025-27488 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-29813 | Critical | EoP | 10 | N/A |
| CVE-2025-29825 | Low | Spoofing | 6.5 | Less Likely |
| CVE-2025-29826 | Important | EoP | 7.3 | Unlikely |
| CVE-2025-29827 | Critical | EoP | 9.9 | N/A |
| CVE-2025-29829 | Important | Info | 5.5 | Less Likely |
| CVE-2025-29830 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29831 | Important | RCE | 7.5 | Unlikely |
| CVE-2025-29832 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29833 | Critical | RCE | 7.1 | Less Likely |
| CVE-2025-29835 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29836 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29837 | Important | Info | 5.5 | Unlikely |
| CVE-2025-29838 | Important | EoP | 7.4 | Unlikely |
| CVE-2025-29839 | Important | Info | 4 | Unlikely |
| CVE-2025-29840 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-29841 | Important | EoP | 7 | More Likely |
| CVE-2025-29842 | Important | SFB | 7.5 | Less Likely |
| CVE-2025-29954 | Important | DoS | 5.9 | Unlikely |
| CVE-2025-29955 | Important | DoS | 6.2 | Unlikely |
| CVE-2025-29956 | Important | Info | 5.4 | Unlikely |
| CVE-2025-29957 | Important | DoS | 6.2 | Unlikely |
| CVE-2025-29958 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29959 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29960 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29961 | Important | Info | 6.5 | Unlikely |
| CVE-2025-29962 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-29963 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-29964 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-29966 | Critical | RCE | 8.8 | Less Likely |
| CVE-2025-29967 | Critical | RCE | 8.8 | Less Likely |
| CVE-2025-29968 | Important | DoS | 6.5 | Unlikely |
| CVE-2025-29969 | Important | EoP | 7.5 | Less Likely |
| CVE-2025-29970 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-29971 | Important | DoS | 7.5 | More Likely |
| CVE-2025-29972 | Critical | Spoofing | 9.9 | N/A |
| CVE-2025-29973 | Important | EoP | 7 | Unlikely |
| CVE-2025-29974 | Important | Info | 5.7 | Unlikely |
| CVE-2025-29975 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-29976 | Important | EoP | 7.8 | More Likely |
| CVE-2025-29977 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-29978 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-29979 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-30375 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-30376 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-30377 | Critical | RCE | 8.4 | Less Likely |
| CVE-2025-30378 | Important | RCE | 7 | Less Likely |
| CVE-2025-30379 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-30381 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-30382 | Important | RCE | 7.8 | More Likely |
| CVE-2025-30383 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-30384 | Important | RCE | 7.4 | Less Likely |
| CVE-2025-30385 | Important | EoP | 7.8 | More Likely |
| CVE-2025-30386 | Critical | RCE | 8.4 | More Likely |
| CVE-2025-30387 | Important | EoP | 9.8 | Unlikely |
| CVE-2025-30388 | Important | RCE | 7.8 | More Likely |
| CVE-2025-30393 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-30394 | Important | DoS | 5.9 | Unlikely |
| CVE-2025-30397 | Important | RCE | 7.5 | KNOWN EXPLOIT |
| CVE-2025-30400 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-32701 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-32702 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-32703 | Important | Info | 5.5 | Less Likely |
| CVE-2025-32704 | Important | RCE | 8.4 | Less Likely |
| CVE-2025-32705 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-32706 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-32707 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-32709 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-33072 | Critical | Info | 8.1 | Less Likely |
| CVE-2025-47732 | Critical | RCE | 8.7 | N/A |
| CVE-2025-47733 | Critical | Info | 9.1 | N/A |
| CVE-2025-4096 | High | RCE | N/A | N/A |
| CVE-2025-4050 | Medium | Info | N/A | N/A |
| CVE-2025-4051 | Medium | RCE | N/A | N/A |
| CVE-2025-4372 | Medium | RCE | N/A | N/A |
| CVE-2025-4052 | Low | RCE | N/A | N/A |
CISCO – Cisco has acknowledged that several of its products are vulnerable to the critical CVE-2025-32433 remote code execution flaw, which stems from an issue in the Erlang/OTP framework’s message handling within the SSH protocol. This vulnerability could enable unauthorized attackers to gain control of affected systems and execute arbitrary code. The affected products include ConfD, Network Services Orchestrator (NSO), Smart PHY, Intelligent Node Manager, and Ultra Cloud Core. But while ConfD and NSO are impacted, their specific configurations prevent them from being vulnerable to remote code execution.
APPLE – Apple has released emergency updates to address two zero-day vulnerabilities, CVE-2025-31200 and CVE-2025-31201, affecting iOS, macOS, and other Apple systems. CVE-2025-31200 allows remote code execution via malicious media files in CoreAudio. CVE-2025-31201 enables attackers to bypass iOS’s Pointer Authentication (PAC) security feature. Apple also patched CVE-2025-24271, an ACL flaw that allows unauthenticated AirPlay commands, and CVE-2025-24132, a buffer overflow vulnerability in AirPlay devices that can lead to remote code execution, potentially enabling malware worms.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
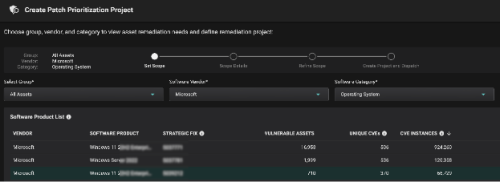
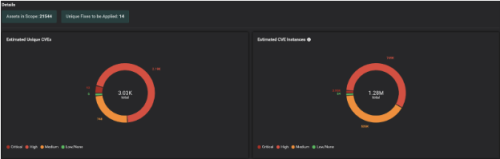
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.