March 12, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 57 CVEs, and republished 10 additional CVEs, including 6 Zero-Day, 6 Critical, and 50 Important—with 6 Zero-Days actively exploited in the wild.

From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 46%, followed by Remote Code Execution (RCE) at 41% and Information Disclosure (ID) at 13%.
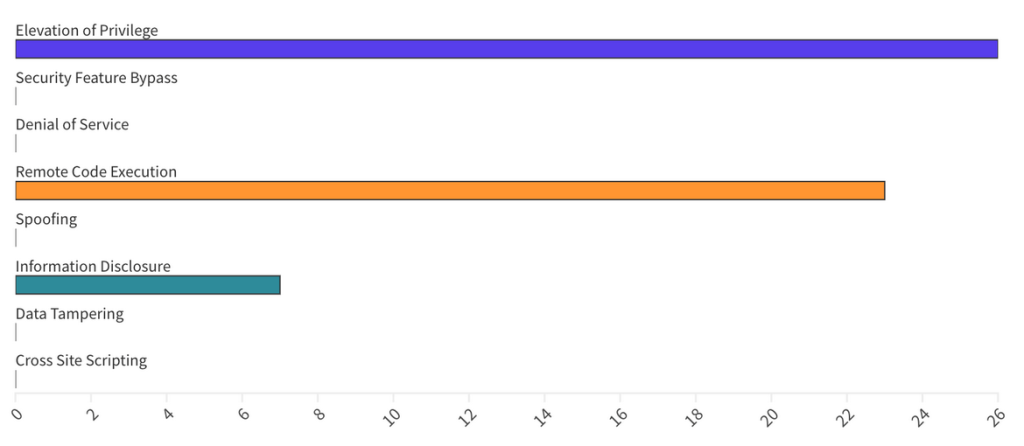
Patches for this month cover components for the following areas:
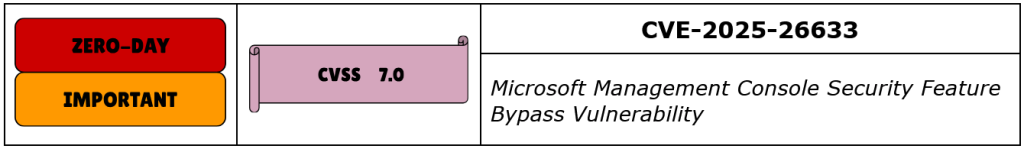
CVE-2025-26633 is a Security Feature Bypass vulnerability in the Microsoft Management Console (MMC), caused by improper handling of user-supplied input when parsing MSC files. The flaw arises due to insufficient validation of input within the MMC, allowing an attacker to craft a malicious MSC file that, when opened by a user, can bypass security mechanisms such as User Account Control (UAC) or other privilege restrictions.
This vulnerability allows an attacker with local access to potentially escalate privileges or perform actions with elevated rights, which could lead to further compromise of the system. The flaw exploits a failure in the handling of input validation, enabling the attacker to circumvent intended security features.
With a CVSS v3.1 base score of 7.0, this vulnerability is considered high severity, especially for environments where attackers may have physical access or are able to convince users to open malicious files. While no active exploitation has been confirmed, the potential for this flaw to be weaponized is significant, making prompt remediation critical.
CVE-2025-24983 is a Critical vulnerability identified as a use-after-free flaw in the Windows Win32 Kernel Subsystem. This vulnerability allows authenticated local attackers to escalate their privileges to the SYSTEM level, potentially gaining complete control over the affected system.
CVE-2025-24983 has been actively exploited in the wild, making it a zero-day threat at the time of discovery. Consequently, CISA has included this vulnerability in its Known Exploited Vulnerabilities Catalog, underscoring the urgency for remediation.
CVE-2025-24984 is an Information Disclosure vulnerability in Windows NTFS, classified under CWE-532 as the insertion of sensitive information into log files. The flaw allows local attackers with physical access to extract confidential data due to improper logging practices within NTFS.
CVE-2025-24984 has been actively exploited in the wild and is listed in CISA’s Known Exploited Vulnerabilities catalog. With a CVSS score of 4.6, it is rated as a medium-severity issue. However, it requires no privileges making it on the list of vulnerabilities that need patching fast.
CVE-2025-24035 and CVE-2025-24045 are remote code execution vulnerabilities in Windows Remote Desktop Services (RDS) caused by improper synchronization and locking of memory regions containing sensitive data. These flaws allow attackers to exploit a race condition within RDS to achieve arbitrary code execution over the network without requiring authentication.
The vulnerabilities arise from improper handling of concurrent access to session data, leading to memory corruption when certain operations are performed under specific timing conditions. Successful exploitation requires an attacker to win a race condition, making exploitation less reliable, but Microsoft has classified both vulnerabilities as “Exploitation More Likely.”
With a CVSSv3 score of 8.1, these vulnerabilities pose a high risk of compromise, especially in enterprise environments where RDS is widely used. While no active exploitation has been confirmed at this time, the technical nature of the flaw suggests a significant likelihood of weaponization in the near future.
CVE-2025-24064 is a Critical use-after-free vulnerability identified in the memory management routines of the Windows Domain Name System (DNS) Server. This flaw occurs when the DNS Server improperly handles memory deallocation during specific processing tasks, leading to the freeing of memory that is still in use.
As a result, an attacker can exploit the flaw by sending specially crafted DNS requests that trigger this use-after-free condition, potentially allowing the execution of arbitrary code in the context of the DNS service. This vulnerability can be exploited remotely over the network, requiring no authentication or user interaction.
Given the high impact of remote code execution, this vulnerability has been assigned a CVSS v3.1 score of 8.1, indicating its critical severity. The flaw poses a significant risk to the confidentiality, integrity, and availability of affected systems. While active exploitation has not been confirmed, the nature of the vulnerability makes it a prime target for attackers.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2025-21180 | Important | Remote Code Execution | 7.8 | More Likely |
| CVE-2025-21199 | Important | Elevation of Privilege | 6.7 | Less Likely |
| CVE-2025-21247 | Important | Information Disclosure | 4.3 | More Likely |
| CVE-2025-24035 | Critical | Remote Code Execution | 8.1 | More Likely |
| CVE-2025-24043 | Important | Remote Code Execution | 7.5 | Less Likely |
| CVE-2025-24044 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2025-24045 | Critical | Remote Code Execution | 8.1 | More Likely |
| CVE-2025-24046 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-24048 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-24049 | Important | Elevation of Privilege | 8.4 | Less Likely |
| CVE-2025-24050 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-24051 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-24054 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2025-24055 | Important | Elevation of Privilege | 4.3 | Less Likely |
| CVE-2025-24056 | Important | Remote Code Execution | 8.8 | Less Likely |
| CVE-2025-24057 | Critical | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24059 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-24061 | Important | Information Disclosure | 7.8 | More Likely |
| CVE-2025-24064 | Critical | Remote Code Execution | 8.1 | Less Likely |
| CVE-2025-24066 | Important | Elevation of Privilege | 8.4 | More Likely |
| CVE-2025-24067 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2025-24070 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2025-24071 | Important | Information Disclosure | 7.5 | Less Likely |
| CVE-2025-24072 | Important | Elevation of Privilege | 7.8 | Less Likely |
| CVE-2025-24075 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24076 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-24077 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24078 | Important | Remote Code Execution | 7 | Less Likely |
| CVE-2025-24079 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24080 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24081 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24082 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24083 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-24084 | Critical | Remote Code Execution | 8.4 | Less Likely |
| CVE-2025-24983 | Important | Elevation of Privilege | 7 | KNOWN EXPLOIT |
| CVE-2025-24984 | Important | Elevation of Privilege | 4.6 | KNOWN EXPLOIT |
| CVE-2025-24985 | Important | Remote Code Execution | 7.8 | KNOWN EXPLOIT |
| CVE-2025-24986 | Important | Remote Code Execution | 6.5 | Less Likely |
| CVE-2025-24987 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2025-24988 | Important | Elevation of Privilege | 6.6 | Less Likely |
| CVE-2025-24991 | Important | Elevation of Privilege | 5.5 | KNOWN EXPLOIT |
| CVE-2025-24992 | Important | Elevation of Privilege | 5.5 | More Likely |
| CVE-2025-24993 | Important | Remote Code Execution | 7.8 | KNOWN EXPLOIT |
| CVE-2025-24994 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-24995 | Important | Elevation of Privilege | 7.8 | More Likely |
| CVE-2025-24996 | Important | Information Disclosure | 6.5 | Less Likely |
| CVE-2025-24997 | Important | #N/A | 4.4 | Less Likely |
| CVE-2025-24998 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-25003 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-25008 | Important | Elevation of Privilege | 7.1 | Less Likely |
| CVE-2025-26627 | Important | Elevation of Privilege | 7 | Less Likely |
| CVE-2025-26629 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-26630 | Important | Remote Code Execution | 7.8 | Less Likely |
| CVE-2025-26631 | Important | Elevation of Privilege | 7.3 | Less Likely |
| CVE-2025-26633 | Important | Information Disclosure | 7 | KNOWN EXPLOIT |
| CVE-2025-26643 | Low | Information Disclosure | 5.4 | Less Likely |
| CVE-2025-26645 | Critical | Remote Code Execution | 8.8 | Less Likely |
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
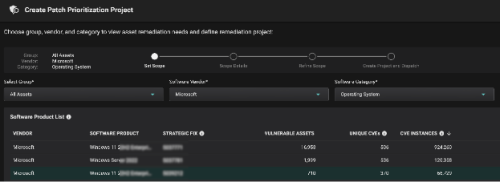
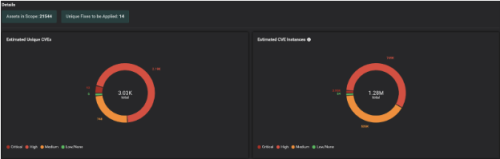
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.