June 10, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 69 CVEs, including 3 republished CVEs. Overall, Microsoft announced 2 Zero-Day, 10 Critical, and 57 Important vulnerabilities.

From an Impact perspective, Remote Code Execution vulnerabilities accounted for 39%, followed by Information Disclosure at 25% and Escalation of Privilege at 20%.
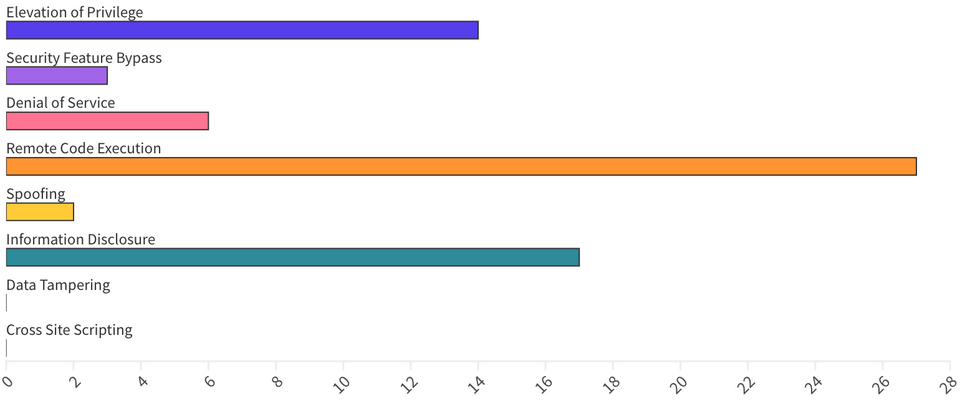
Patches for this month cover components for the following areas:
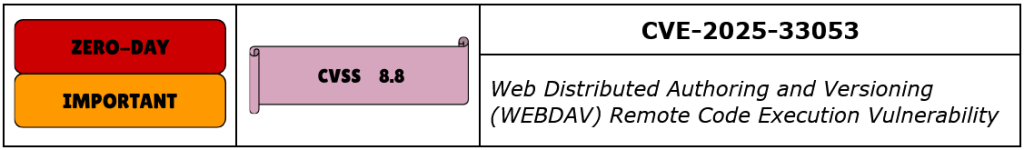
CVE-2025-33053 is a critical remote code execution vulnerability in the Microsoft Windows WebDAV client, stemming from improper handling of Internet Shortcut (.url) files that reference malicious WebDAV shares. The flaw happens when a .url file is crafted to specify a remote UNC path as its working directory. When a user opens such a shortcut, the WebDAV client attempts to resolve and interact with the remote resource. During this process, trusted executables such as iediagcmd.exe — a legitimate diagnostic tool — may be invoked with their search paths manipulated to prioritize the attacker-controlled directory. This behavior results in the unintended loading and execution of binaries from the remote share, allowing arbitrary code execution within the context of the user who opened the file.
Although this vulnerability does not inherently allow privilege escalation, it provides a reliable initial foothold for threat actors conducting targeted attacks. Microsoft reported that the vulnerability has been exploited in the wild by the Stealth Falcon advanced persistent threat group (aka FruityArmor). Attackers distributed weaponized .url files via spear-phishing emails to targets in regions such as the Middle East. Once opened, the shortcut initiated the loading of a multistage malware implant — referred to as Horus — through a series of binaries and loaders hosted on the attacker’s infrastructure. The implant includes components for keylogging, credential dumping, and establishing persistent remote access. The exploit chain leverages legitimate Windows utilities to avoid detection and is further obfuscated using runtime packers and encryption.
Microsoft assigned CVE-2025-33053 a CVSS score of 8.8, reflecting the fact that the attack can be initiated remotely, requires minimal user interaction, and results in full compromise of confidentiality, integrity, and availability. CISA has added CVE-2025-33053 to its KEV Catalog and recommends that organizations apply the patch no later than June 17, 2025.
CVE-2025-33073 is a high-severity elevation of privilege vulnerability affecting the Microsoft Windows Server Message Block (SMB) client. The vulnerability is a result of improper handling of security contexts during the establishment of authenticated SMB sessions, where the SMB client fails to correctly isolate session credentials when interacting with certain types of network shares, particularly in scenarios involving symbolic links or server-side redirection. This flaw enables an attacker-controlled SMB server to manipulate session metadata in such a way that the client inadvertently grants elevated privileges to untrusted code or operations initiated by the attacker.
To exploit this vulnerability, an attacker must lure an authenticated local user into initiating a connection to a malicious SMB share — typically through a crafted UNC path delivered via phishing, malicious scripts, or cross-protocol interaction. Once the connection is established, the malicious SMB server can take advantage of the incorrect session token propagation to execute code in the context of SYSTEM on the victim’s machine. Because the SMB client operates within core networking components of the Windows operating system, successful exploitation effectively allows a low-privilege user to elevate their access to the highest local privilege level, bypassing standard access control mechanisms and leading to full system compromise.
Microsoft assigned CVE-2025-33073 a CVSS score of 8.8, indicating a high severity due to the low complexity of exploitation and the critical impact on confidentiality, integrity, and availability. The vulnerability was addressed for all supported versions of Windows 10, Windows 11, and corresponding server editions. As a partial mitigation, administrators are advised to enable SMB signing through Group Policy and to restrict outbound SMB traffic wherever possible, particularly to untrusted or external hosts. While Microsoft has not confirmed active exploitation in the wild as of the patch release, the vulnerability has been publicly disclosed, increasing the risk of exploitation by opportunistic threat actors. Prompt deployment of security updates is strongly recommended to mitigate the risk of privilege escalation through SMB session manipulation.
CVE‑2025‑29828 is a high-severity remote code execution vulnerability in the Windows Cryptographic Services (CryptSvc) component. The root cause lies in a missing release of memory after its effective lifetime when handling cryptographic operations — specifically within the secure channel (Schannel) engine responsible for TLS connections. This memory mismanagement permits an attacker to create a use-after-free scenario, enabling controlled memory corruption. If successfully exploited, the corrupted memory can be leveraged to execute arbitrary code within the CryptSvc process, which runs with SYSTEM privileges.
The vulnerability can be triggered remotely with no user interaction, and it requires no prior authentication. The network-facing attack vector targets any service that relies on Cryptographic Services to process TLS or other cryptographic messages. Given that CryptSvc operates in a core system service with access to critical cryptographic functions, successful exploitation may allow an unauthenticated remote attacker to gain full control over the host, compromising confidentiality, integrity, and availability across the system — all with SYSTEM‑level privileges.
Microsoft assigned CVE‑2025‑29828 a CVSS score of 8.1, noting that exploitation requires high attack complexity but could result in total system compromise. The vulnerability is tracked under CWE‑401, “Missing Release of Memory after Effective Lifetime”. Microsoft addressed this issue by enhancing memory handling routines in Cryptographic Services to ensure that allocated buffers are correctly freed after use.
Given the remote and unauthenticated nature of the attack, this vulnerability presents a high risk to any Internet‑exposed Windows systems or servers that perform TLS termination. Administrators are strongly advised to apply the June 2025 Windows updates immediately. In addition, deploying network-level mitigations such as intrusion detection systems capable of identifying anomalous TLS handshakes, and isolating systems that do not require remote TLS services, can help reduce the risk of exploitation while patches are being applied.
CVE-2025-32710 is a critical remote code execution vulnerability in Windows Remote Desktop Services, specifically within the Remote Desktop Protocol (RDP) stack. The flaw arises from a use-after-free condition in the handling of RDP connections, allowing an unauthenticated attacker to execute arbitrary code remotely. This vulnerability is triggered when the RDP service improperly manages memory during the processing of RDP requests, leading to potential code execution in the context of the RDP service process.
Exploitation of this vulnerability requires network access to the affected RDP service and does not necessitate user interaction or authentication. Successful exploitation can result in the attacker executing arbitrary code with SYSTEM privileges, leading to complete system compromise. Given the widespread use of RDP in enterprise environments, this vulnerability presents a significant risk, particularly for systems exposed to the internet.
Microsoft has assigned CVE-2025-32710 a CVSS score of 8.1, indicating a high severity level. Administrators are strongly advised to apply the security updates promptly to mitigate the risk.
CVE-2025-47162 is a high-severity heap-based buffer overflow vulnerability affecting the Microsoft Office suite, specifically in the component responsible for parsing and rendering embedded objects within Office document files. The vulnerability originates from improper bounds checking when processing malformed data structures embedded in document objects such as OLE (Object Linking and Embedding) streams or ActiveX controls. This flaw allows an attacker to overwrite heap memory buffers, leading to memory corruption that can be exploited to achieve arbitrary code execution.
Exploitation requires the victim to open or preview a specially crafted Microsoft Office document, typically delivered via email or other social engineering vectors. Upon processing the malicious document, the vulnerable Office component mishandles object data, causing a buffer overflow that corrupts the heap. The attacker can then manipulate this corruption to hijack control flow and execute attacker-controlled code with the privileges of the current user. Given that Office applications usually run with user-level privileges, exploitation may enable lateral movement or installation of persistent malware within the user’s session.
Microsoft assigned CVE-2025-47162 a CVSS score of 7.8, reflecting the high impact of arbitrary code execution with user-level privileges and the requirement for user interaction to trigger the exploit. The vulnerability was patched in the June 2025 Microsoft security updates, which included enhancements to input validation and memory handling routines in the Office file parsing engine to prevent out-of-bounds writes. Due to the widespread use of Microsoft Office and frequent targeting by threat actors, immediate application of the patch is strongly recommended. In addition, users should exercise caution when opening documents from untrusted sources and consider employing email filtering solutions to block suspicious attachments.
CVE-2025-47172 describes a critical remote code execution vulnerability impacting Microsoft SharePoint Server. This flaw originates from an improper neutralization of special elements used in SQL commands, commonly known as SQL Injection (CWE-89). This means that user-controlled input is not correctly sanitized before being incorporated into SQL queries. The consequence is that an attacker can inject malicious SQL statements. Unlike typical SQL injection vulnerabilities, which might be confined to database manipulation, this particular flaw likely facilitates the execution of operating system commands. This escalation can occur through SQL Server features such as xp_cmdshell or CLR integration, thereby significantly elevating the potential impact from mere data manipulation to a full system compromise.
An authenticated attacker possessing low-level privileges can exploit this vulnerability over a network to execute arbitrary code. The primary impact of this vulnerability is the ability for an authorized attacker with low-privilege access to achieve remote code execution on the affected SharePoint server. Once remote code execution is accomplished, attackers can compromise the confidentiality of sensitive system data, modify or delete critical information, and disrupt service availability. They can also extract stored credentials, access application secrets, and steal authentication tokens. This initial access can be chained with local exploits to escalate privileges, potentially reaching the level of domain administrator, which further facilitates lateral movement within the network from the compromised SharePoint server. Furthermore, successful exploitation could enable widespread data theft from SharePoint and connected systems, and even lead to the deployment of ransomware across the victim’s network. Organizations that utilize SharePoint for core business operations, expose their SharePoint instances to the internet, grant broad “Site Member” access, or rely on custom applications interacting with vulnerable components face a particularly high risk.
Currently, no public proof-of-concept exploits or active in-the-wild exploitation for CVE-2025-47172 have been observed. Nevertheless, given its nature as an SQL injection leading to remote code execution and Microsoft’s “More Likely” exploitability rating for similar critical vulnerabilities, it is highly probable that exploitation will emerge in the future.
Microsoft has assigned CVE-2025-47172 a CVSS score of 8.8, indicating a critical severity. The attack vector is network-based, meaning it can be exploited remotely. The attack complexity is low, requiring minimal technical sophistication. Only low privileges are required on the part of the authenticated attacker, and no user interaction is necessary for successful exploitation. The scope of the vulnerability remains unchanged, but the impact on confidentiality, integrity, and availability is rated as high.
The affected systems include Microsoft SharePoint Server 2016, Microsoft SharePoint Server 2019, and Microsoft SharePoint Server Subscription Edition. This confirms that multiple versions of SharePoint Server are vulnerable to this flaw.
Regarding mitigation, Microsoft released a security update advising organizations to apply this patch as soon as possible and implement least privilege access controls by restricting user permissions in SharePoint to the absolute minimum required. For developers of custom applications interacting with SharePoint, it is essential to ensure that all user input in SQL queries is properly parameterized to prevent SQL injection. Regularly monitoring SharePoint server logs for suspicious activities that might indicate attempted exploitation is a recommended security practice. Furthermore, limiting network access to SharePoint servers to only necessary services and trusted IP ranges can significantly enhance security. Finally, implementing robust input validation and sanitization mechanisms for all user-supplied data within SharePoint applications is a fundamental defense.
CVE-2025-47966 identifies a critical privilege escalation vulnerability affecting Microsoft Power Automate for Desktop. This vulnerability arises from the exposure of sensitive information to an unauthorized actor, which then allows an unauthenticated attacker to elevate their privileges over a network.
The technical nature of this vulnerability is categorized under CWE-200, “Exposure of Sensitive Information to an Unauthorized Actor”. This means the affected Power Automate for Desktop software inadvertently reveals sensitive data to an entity that is not explicitly authorized to access it. This exposure creates a pathway for an attacker to escalate their privileges within the system. The critical aspect is that this can be achieved over a network by an unauthenticated attacker, without requiring any user interaction.
The impact of CVE-2025-47966 is extremely severe, as it grants an unauthorized attacker the ability to elevate privileges over a network, potentially leading to a complete system compromise. This includes the potential for full unauthorized access to sensitive system information, the capacity to modify or delete critical data, and the ability to achieve full network privilege escalation. Consequently, the confidentiality, integrity, and availability of affected Power Automate for Desktop systems could be completely compromised. Such a vulnerability is particularly significant for organizations that heavily rely on Power Automate for their business processes, as a successful exploit could have wide-ranging repercussions across their networks.
As of the current information, there is no public proof-of-concept exploit available and no evidence of in-the-wild exploitation for CVE-2025-47966. However, given its critical severity and the nature of the vulnerability, it is a high-risk concern that organizations should address promptly.
Microsoft has assigned CVE-2025-47966 a CVSS v3.1 score of 9.8, classifying it as Critical. The attack vector is network-based, meaning it can be exploited remotely, while the attack complexity is low. The primary mitigation and recommendation is to immediately apply this security patch to Microsoft Power Automate for Desktop. Organizations should utilize Microsoft’s automatic update service or refer to the Microsoft Security Update Guide to search for and apply the appropriate patch for their systems. Additionally, it is strongly recommended to conduct a thorough security audit of network access and privileges within the environment. Continuous monitoring for any potential unauthorized access or suspicious network activities related to Power Automate for Desktop instances should also be implemented. While Microsoft has stated that this issue has been fully mitigated at the cloud service level, client-side installations of Power Automate for Desktop still require the patch.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2025-24065 | Important | Info | 5.5 | Less Likely |
| CVE-2025-24068 | Important | Info | 5.5 | Less Likely |
| CVE-2025-24069 | Important | Info | 5.5 | Less Likely |
| CVE-2025-29828 | Critical | RCE | 8.1 | Less Likely |
| CVE-2025-30399 | Important | RCE | 7.5 | Less Likely |
| CVE-2025-32710 | Critical | RCE | 8.1 | Less Likely |
| CVE-2025-32712 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-32713 | Important | EoP | 7.8 | More Likely |
| CVE-2025-32714 | Important | EoP | 7.8 | More Likely |
| CVE-2025-32715 | Important | Info | 6.5 | Less Likely |
| CVE-2025-32716 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-32718 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-32719 | Important | Info | 5.5 | Unlikely |
| CVE-2025-32720 | Important | Info | 5.5 | Unlikely |
| CVE-2025-32721 | Important | EoP | 7.3 | Unlikely |
| CVE-2025-32722 | Important | Info | 5.5 | Less Likely |
| CVE-2025-32724 | Important | DoS | 7.5 | Unlikely |
| CVE-2025-32725 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-33050 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-33052 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33053 | Important | RCE | 8.8 | KNOWN EXPLOIT |
| CVE-2025-33055 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33056 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-33057 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-33058 | Important | Info | 5.5 | Less Likely |
| CVE-2025-33059 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33060 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33061 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33062 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33063 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33064 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-33065 | Important | Info | 5.5 | Unlikely |
| CVE-2025-33066 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-33067 | Important | EoP | 8.4 | Less Likely |
| CVE-2025-33068 | Important | DoS | 7.5 | Unlikely |
| CVE-2025-33069 | Important | SFB | 5.1 | Less Likely |
| CVE-2025-33070 | Critical | EoP | 8.1 | More Likely |
| CVE-2025-33071 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-33073 | Important | EoP | 8.8 | KNOWN EXPLOIT |
| CVE-2025-33075 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47160 | Important | SFB | 5.4 | Less Likely |
| CVE-2025-47162 | Critical | RCE | 8.4 | More Likely |
| CVE-2025-47163 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-47164 | Critical | RCE | 8.4 | More Likely |
| CVE-2025-47165 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-47166 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-47167 | Critical | RCE | 8.4 | More Likely |
| CVE-2025-47168 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-47169 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-47170 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-47171 | Important | RCE | 6.7 | Unlikely |
| CVE-2025-47172 | Critical | RCE | 8.8 | Less Likely |
| CVE-2025-47173 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-47174 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-47175 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-47176 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-47953 | Critical | RCE | 8.4 | Less Likely |
| CVE-2025-47955 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47956 | Important | Spoofing | 5.5 | Less Likely |
| CVE-2025-47957 | Important | RCE | 8.4 | Unlikely |
| CVE-2025-47959 | Important | RCE | 7.1 | Unlikely |
| CVE-2025-47962 | Important | EoP | 7.8 | More Likely |
| CVE-2025-47966 | Critical | EoP | 9.8 | N/A |
| CVE-2025-47968 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47969 | Important | Info | 4.4 | Less Likely |
| CVE-2025-47977 | Important | Spoofing | 7.6 | Less Likely |
| CVE-2025-3052 | Important | SFB | 6.7 | N/A |
| CVE-2025-5068 | Medium | RCE | N/A | N/A |
| CVE-2025-5419 | High | RCE | N/A | N/A |
GOOGLE – has issued an urgent update for its CHROME 137 browser to fix three security flaws, one of which is a high-severity zero-day exploit identified as CVE-2025-5419. This particular vulnerability involves an out-of-bounds read/write issue within Chrome’s V8 JavaScript and WebAssembly engine, and reports indicating that spyware vendors are actively exploiting it.
While Google has confirmed that an exploit for CVE-2025-5419 exists, they have not yet disclosed the technical specifics of the flaw. According to information from NIST, this vulnerability could potentially lead to heap corruption when processing a specially designed HTML page, which might then enable an attacker to execute arbitrary code. This is the second actively exploited zero-day in Chrome in 2025, the first being CVE-2025-2783, widely used by Russia in attacks.
MOZILLA – has issued updates for its FIREFOX browser to address two critical JavaScript vulnerabilities, both of which were successfully demonstrated at the Pwn2Own Berlin 2025 hacking competition. While these flaws could lead to memory corruption and the execution of arbitrary code, it is important to note that they were unable to bypass the browser’s sandbox.
The first vulnerability, identified as CVE-2025-4918, was discovered by Eduard Boschen and Tao Yang from Palo Alto Networks. This flaw allows for out-of-bounds memory access when the browser resolves JavaScript Promise objects. Such an issue could potentially result in the execution of arbitrary code within the browser’s content process.
The second vulnerability, CVE-2025-4919, was submitted by security researcher Manfred Paul. This vulnerability involves an array index confusion that occurs during the optimization of linear sums, ultimately leading to a memory overflow.
Both of these critical vulnerabilities were successfully exploited during the Pwn2Own event. The researchers responsible for discovering and demonstrating these exploits were awarded $50,000 each and also earned five points towards the prestigious “Master of Pwn” title. Mozilla acted swiftly, releasing the necessary patches within 24 hours of the public demonstration. Although the browser’s sandboxing mechanism successfully prevented a full system compromise, users are strongly advised to update their Firefox installations immediately to ensure comprehensive protection against these exploited vulnerabilities.
IVANTI – The CVE-2025-4427 and CVE-2025-4428 vulnerabilities form a critical exploit chain within Ivanti Endpoint Manager Mobile (EPMM). This combination allows an unauthenticated attacker to achieve remote code execution (RCE) on vulnerable EPMM devices. Specifically, CVE-2025-4427 is an authentication bypass vulnerability in the EPMM API, caused by improper request handling where certain routes lack necessary Spring Security authentication checks. This flaw enables an attacker to access restricted API endpoints without valid credentials. Chained with this is CVE-2025-4428, a remote code execution vulnerability in Expression Language (EL) injection due to unsafe handling of user-supplied input in error messages, allowing arbitrary Java code execution via a crafted format parameter at the /api/v2/featureusage endpoint.
The combined impact is severe: the authentication bypass grants unauthenticated access to the RCE endpoint, leading to unauthenticated remote code execution. This provides attackers with full control over the EPMM system, enabling data exfiltration and persistent access. This exploit chain has been actively exploited in the wild by threat actors against a limited number of targets, leading CISA to add both CVEs to its Known Exploited Vulnerabilities (KEV) Catalog. Public proof-of-concept exploits are now available, heightening the risk.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
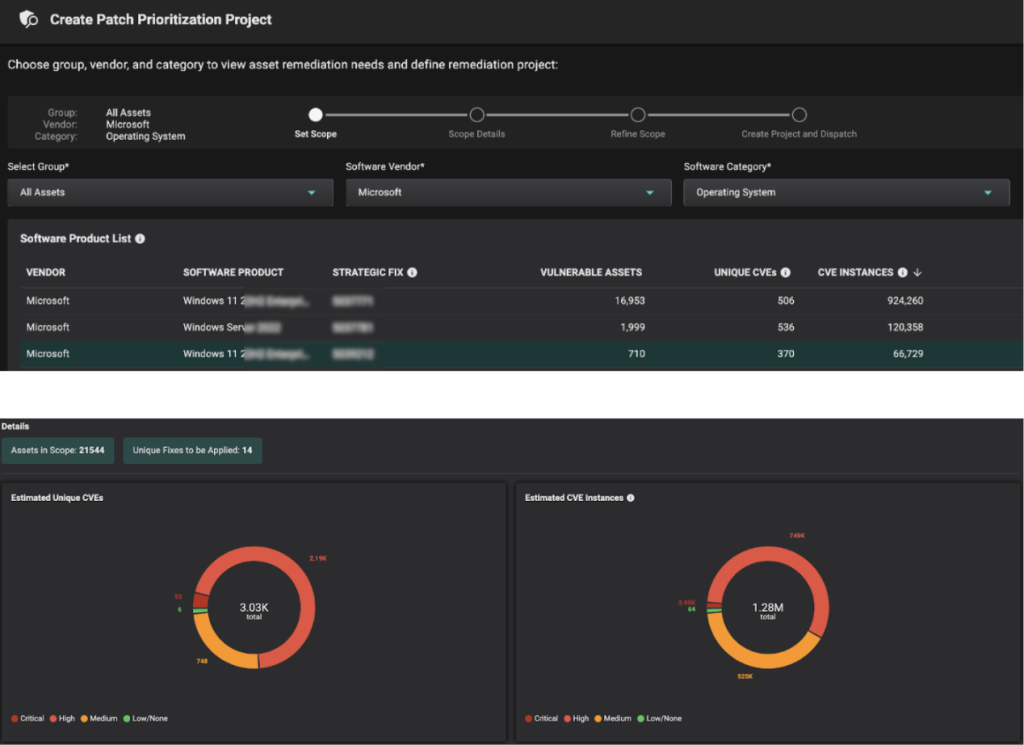
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.