July 8, 2025
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 140 CVEs, including 10 republished CVEs. Overall, Microsoft announced 1 Zero-Day, 10 Critical, and 120 Important vulnerabilities.

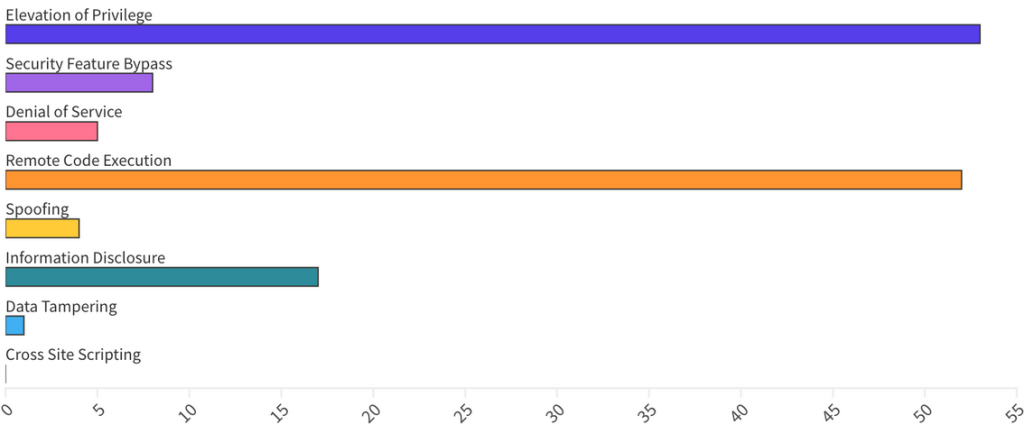
From an Impact perspective, Remote Code Execution vulnerabilities accounted for 37%, while Information Disclosure for 12% and Escalation of Privilege for 38%.
Patches for this month cover components for the following areas:
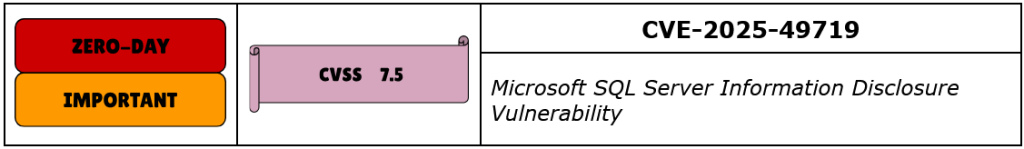
CVE-2025-49719 is a high-severity information disclosure vulnerability affecting Microsoft SQL Server, caused by improper memory initialization during the handling of certain SQL queries. The flaw resides in the database engine’s processing of crafted input sequences that interact with variable-length parameters or internal memory buffers. Under specific conditions, a remote, unauthenticated attacker can exploit this behavior by sending malformed SQL requests to an exposed SQL Server instance, triggering access to memory regions that have not been securely cleared prior to use, resulting in the leakage of uninitialized memory contents into responses.
The exposed memory may contain fragments of sensitive data, including authentication credentials, access tokens, connection strings, or fragments of prior query data, depending on the memory reuse state at the time of exploitation. Because SQL Server processes requests without validating the complete state of memory prior to allocation or exposure, it becomes possible for a remote adversary to infer or extract confidential information through repeated crafted queries, even in environments with otherwise strong access controls. This vulnerability can be triggered over the network without authentication, making it suitable for exploitation in low-complexity reconnaissance attacks or in chained post-compromise data harvesting.
Microsoft acknowledged that CVE-2025-49719 was publicly disclosed prior to the release of a patch, making it a zero-day vulnerability at the time of the July 2025 Patch Tuesday. However, no active exploitation in the wild has been confirmed as of this writing. Microsoft assigned a CVSS v3.1 base score of 7.5, reflecting the vulnerability’s remote exploitability and the high confidentiality impact, but noting the lack of direct privilege escalation or system integrity compromise. The vulnerability was discovered and reported by Vladimir Aleksic of the Microsoft Security Response Center. Although exploitation is assessed as less likely, the public disclosure increases the overall risk for exposed database servers, particularly unpatched versions.
The vulnerability affects multiple supported versions of Microsoft SQL Server, including SQL Server 2016 SP2 and SP3, SQL Server 2017 CU31, SQL Server 2019 CU32, and SQL Server 2022 CU19. Microsoft addressed the flaw by modifying how memory buffers are initialized and accessed during query processing to ensure that no residual data is exposed during normal or malformed execution paths. The fix is included in the cumulative security updates released on July 8, 2025. Microsoft further recommends updating the Microsoft OLE DB Driver for SQL Server to version 18.7 or later, as earlier versions may not be compatible with the memory handling changes introduced in the patch.
Organizations are advised to apply the relevant SQL Server and OLE DB driver updates without delay, especially in environments where database services are exposed to untrusted networks or integrated into externally accessible applications. Although the vulnerability does not grant code execution or privilege elevation on its own, the ability to extract arbitrary memory from a privileged database process introduces substantial risk to the confidentiality of enterprise data and may serve as a precursor to broader attacks involving credential theft or lateral movement.
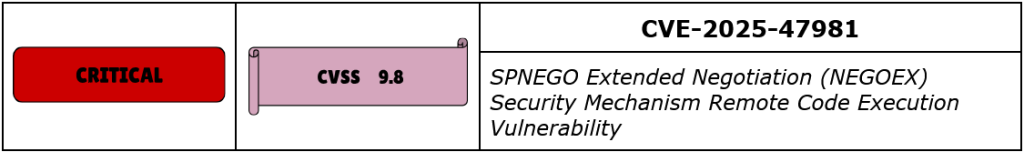
CVE-2025-47981 is a critical heap‑based buffer‑overflow vulnerability in the Windows SPNEGO Extended Negotiation (NEGOEX) protocol component, allowing unauthenticated remote code execution. The flaw exists in the handling of SPNEGO messages during extended negotiation, where malformed data can overflow heap buffers due to improper bounds validation. This allows an attacker to overwrite heap metadata or adjacent heap regions and achieve arbitrary code execution within the context of the LocalSystem account.
A remote attacker can exploit this flaw by sending a specially crafted SPNEGO handshake message to the affected service. No user interaction is required, and no valid credentials or prerequisite privileges are necessary. Due to SPNEGO’s role in negotiating authentication for many Windows services — including IIS, WinRM, and SMB — the attacker can target multiple network-exposed interfaces. Because the code executes at system level and exploitation can propagate via automated service-to-service negotiation, Microsoft classifies the defect as “wormable” and assigned a CVSS v3.1 base score of 9.8, reflecting high impact on integrity, confidentiality, and availability, combined with remote unauthenticated vector and low attack complexity.
This vulnerability affects Windows 10 version 1607 and later, as well as equivalent Windows Server versions, specifically where the Group Policy “Network security: Allow PKU2U authentication requests to this computer to use online identities” is enabled by default. The NEGOEX protocol is automatically used by services that support SPNEGO, making a broad array of server roles and client machines vulnerable by default.
Microsoft’s exploitability index rates the flaw as “Exploitation More Likely”, with anticipation of in-the-wild attacks within 30 days without patch deployment. Microsoft addressed this issue in the July 8, 2025 security updates by implementing proper allocation and bounds checking for NEGOEX buffers within the Windows authentication components. System administrators are required to install the umulative updates specific to their OS version (KB5062553/K5062552 for Windows 11/10), ensuring SPNEGO buffer handling incorporates these safeguards.
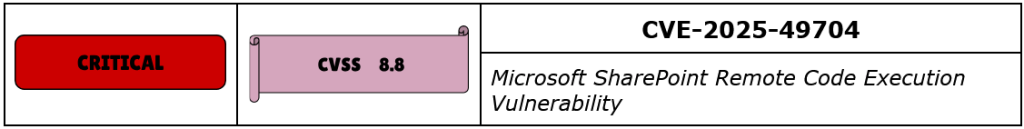
CVE-2025-49704 is a high-severity authenticated remote code execution vulnerability in Microsoft Office SharePoint, caused by improper control of code generation allowing code injection by an attacker with at least site-level privileges who can exploit this flaw by injecting a malicious payload into a SharePoint site. When processed by the server, the malicious input is not correctly sanitized or validated, enabling the injection of arbitrary code that executes in the context of the SharePoint application pool account.
Because SharePoint processes user-supplied content through server-side code-generation paths without enforcing strict boundaries, the attacker’s payload can traverse controlled execution paths, leading to full execution on the server. Successful exploitation grants the ability to modify or exfiltrate site data, deploy web shells, or pivot laterally to back-end systems.
Microsoft assigned this vulnerability a CVSS 3.1 base score of 8.8, reflecting its network attack vector, low complexity, privilege requirement, and full impact on confidentiality, integrity, and availability. Although authenticated access is required at minimum site membership, the flaw has low exploitation complexity and Microsoft indicates the likelihood of active exploitation is “more likely”.
This vulnerability affects all supported versions of SharePoint Server where code-generation functionality is exposed over the network, including SharePoint Server versions 2016, 2019, and Subscription Edition. To mitigate, administrators should apply the latest SharePoint cumulative updates immediately. In environments where authenticated SharePoint access isn’t required by all users, consider tightening membership permissions and applying URL filtering or web application firewall rules to monitor uploads and requests that may include executable content.
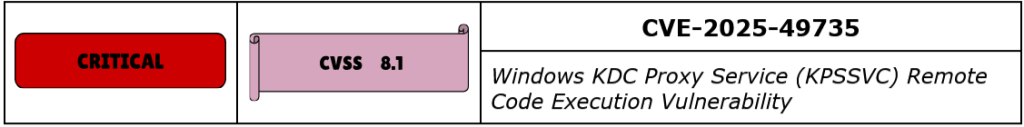
CVE-2025-49735 is a high-severity use-after-free vulnerability in the Windows Kerberos Key Distribution Center (KDC) Proxy Service (KPSSVC), which permits unauthenticated remote code execution due to improper handling of memory allocation and object lifetimes during Kerberos authentication over HTTP. The vulnerability is triggered when a remote attacker sends a series of carefully crafted Kerberos messages to a Windows server that is configured to accept Kerberos proxy requests via KPSSVC. Under specific timing conditions, the service fails to maintain a consistent reference to heap-allocated memory, leading to the use of a freed pointer.
This use-after-free condition allows the attacker to manipulate memory in a way that results in execution of attacker-controlled code within the KPSSVC process. Since the service runs under the context of the LocalSystem account, successful exploitation grants the attacker full control over the underlying server operating system. The vulnerability does not require prior authentication, nor does it require any interaction from the target user, making it suitable for automated exploitation attempts against exposed systems.
Microsoft assigned this vulnerability a CVSS v3.1 base score of 8.1, with a vector string indicating network-based attackability, zero privileges required, and no user interaction. Although the attack complexity is rated as high due to the inherent difficulty of reliably exploiting a race condition, Microsoft considers exploitation to be “more likely”, given the exposure of KPSSVC to unauthenticated input and the historical success of attackers in weaponizing similar memory safety vulnerabilities. The vulnerability does not affect domain controllers directly, but it does affect any supported Windows Server system configured as a Kerberos Proxy Protocol endpoint, including Windows Server 2012 through Windows Server 2022 (including version 23H2).
The vulnerability was discovered internally. Microsoft addressed the flaw by modifying the KPSSVC service to ensure proper synchronization and reference tracking of heap-allocated memory, thereby eliminating the possibility of dangling pointer dereferencing. Security updates that remediate this vulnerability were published under cumulative update rollups for each supported Windows Server version, including KB5062600 for Windows Server 2022 and KB5062599 for Windows Server 2019.
Organizations that use KPSSVC for Kerberos proxy functionality — particularly in hybrid identity or remote authentication scenarios — should apply the security update without delay. While exploitation requires precise control over memory layout and timing, successful attacks result in complete system compromise and may allow adversaries to use KPSSVC as a stepping stone for lateral movement into Active Directory environments. Disabling the KPSSVC feature entirely on systems where it is not required may serve as a temporary mitigation measure in environments unable to patch immediately.
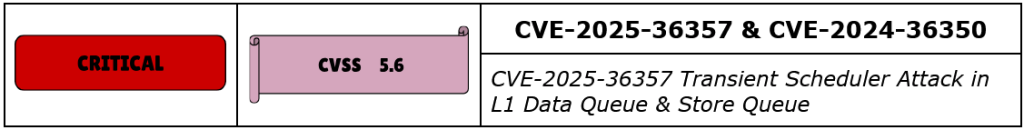
CVE-2025-36357 is a medium-severity speculative-execution side-channel vulnerability affecting AMD processors, caused by insufficient isolation of speculative data in the L1 data cache. When an attacker executes specially crafted speculative-memory instructions, it becomes possible to bypass existing microarchitectural boundaries and extract data from recently accessed memory locations. This data may include sensitive information from higher-privileged contexts, such as encryption keys or credential fragments.
This vulnerability can be exploited by a local attacker using high-resolution timing methods to monitor speculative access patterns in the L1 cache. No special privileges are necessary beyond code execution on the same host. The attack complexity is rated high due to requirement for precise timing and microarchitectural conditions.
CVE-2024-36350 is a medium-severity speculative-execution side-channel vulnerability in AMD processors, allowing local attackers to infer data via timing manipulation in the Store Queue. By orchestrating overlapping memory store and subsequent memory operations, attackers can glean timing variations that indirectly expose data from previous memory stores executed by other threads or processes.
This vulnerability is exploitable by local unprivileged code with access to high-resolution timers, requiring no user interaction. The attack complexity is high and may require careful calibration of memory workloads. AMD has assigned a CVSS v3.1 base score of 5.6 (Medium) with the same metrics as CVE‑2025‑36357.
Both CVE‑2025‑36357 and CVE‑2024‑36350 are speculative-execution side-channel vulnerabilities targeting AMD CPU microarchitecture. Although they pose no direct code execution threat, they can compromise confidentiality by leaking sensitive data. They have moderate overall severity (CVSS 5.6) and require local code execution with high attack complexity, making real-world exploitation less likely but still plausible in multi-tenant cases. Firmware updates (PI) and OS patches should be applied promptly where applicable.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2025-21195 | Important | EoP | 6 | Less Likely |
| CVE-2025-26636 | Important | Info | 5.5 | Less Likely |
| CVE-2025-33054 | Important | Spoofing | 8.1 | Less Likely |
| CVE-2025-47159 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47178 | Important | RCE | 8 | Unlikely |
| CVE-2025-47971 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47972 | Important | EoP | 8 | Unlikely |
| CVE-2025-47973 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-47975 | Important | EoP | 7 | Less Likely |
| CVE-2025-47976 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47978 | Important | DoS | 6.5 | More Likely |
| CVE-2025-47980 | Critical | Info | 6.2 | Less Likely |
| CVE-2025-47981 | Critical | RCE | 9.8 | More Likely |
| CVE-2025-47982 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47984 | Important | Info | 7.5 | Less Likely |
| CVE-2025-47985 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47986 | Important | EoP | 8.8 | Unlikely |
| CVE-2025-47987 | Important | EoP | 7.8 | More Likely |
| CVE-2025-47988 | Important | RCE | 7.5 | Less Likely |
| CVE-2025-47991 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-47993 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47994 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-47996 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-47998 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-47999 | Important | DoS | 6.8 | Less Likely |
| CVE-2025-48000 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-48001 | Important | SFB | 6.8 | More Likely |
| CVE-2025-48002 | Important | Info | 5.7 | Less Likely |
| CVE-2025-48003 | Important | SFB | 6.8 | Less Likely |
| CVE-2025-48799 | Important | EoP | 7.8 | More Likely |
| CVE-2025-48800 | Important | SFB | 6.8 | More Likely |
| CVE-2025-48802 | Important | Spoofing | 6.5 | Less Likely |
| CVE-2025-48803 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-48804 | Important | SFB | 6.8 | More Likely |
| CVE-2025-48805 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-48806 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-48808 | Important | Info | 5.5 | Unlikely |
| CVE-2025-48809 | Important | Info | 5.5 | Less Likely |
| CVE-2025-48810 | Important | Info | 5.5 | Less Likely |
| CVE-2025-48811 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-48812 | Important | Info | 5.5 | Unlikely |
| CVE-2025-48814 | Important | SFB | 7.5 | Less Likely |
| CVE-2025-48815 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-48816 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-48817 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-48818 | Important | SFB | 6.8 | More Likely |
| CVE-2025-48819 | Important | EoP | 7.1 | Less Likely |
| CVE-2025-48820 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-48821 | Important | EoP | 7.1 | Less Likely |
| CVE-2025-48822 | Critical | RCE | 8.6 | Less Likely |
| CVE-2025-48823 | Important | Info | 5.9 | Less Likely |
| CVE-2025-48824 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49657 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49658 | Important | Info | 5.5 | Less Likely |
| CVE-2025-49659 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49660 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49661 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49663 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49664 | Important | Info | 5.5 | Less Likely |
| CVE-2025-49665 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49666 | Important | RCE | 7.2 | Unlikely |
| CVE-2025-49667 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49668 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49669 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49670 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49671 | Important | Info | 6.5 | Unlikely |
| CVE-2025-49672 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49673 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49674 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49675 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49676 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49677 | Important | EoP | 7 | Less Likely |
| CVE-2025-49678 | Important | EoP | 7 | Unlikely |
| CVE-2025-49679 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49680 | Important | DoS | 7.3 | Less Likely |
| CVE-2025-49681 | Important | Info | 6.5 | Unlikely |
| CVE-2025-49682 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-49683 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-49684 | Important | Info | 5.5 | Less Likely |
| CVE-2025-49685 | Important | EoP | 7 | Less Likely |
| CVE-2025-49686 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49687 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-49688 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49689 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49690 | Important | EoP | 7.4 | Less Likely |
| CVE-2025-49691 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-49693 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49694 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49695 | Critical | RCE | 8.4 | More Likely |
| CVE-2025-49696 | Critical | RCE | 8.4 | More Likely |
| CVE-2025-49697 | Critical | RCE | 8.4 | Less Likely |
| CVE-2025-49698 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-49699 | Important | RCE | 7 | Less Likely |
| CVE-2025-49700 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-49701 | Important | RCE | 8.8 | More Likely |
| CVE-2025-49702 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-49703 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-49704 | Critical | RCE | 8.8 | More Likely |
| CVE-2025-49705 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-49706 | Important | Spoofing | 6.3 | Less Likely |
| CVE-2025-49711 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-49713 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49714 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-49716 | Important | DoS | 5.9 | Unlikely |
| CVE-2025-49717 | Critical | RCE | 8.5 | Unlikely |
| CVE-2025-49718 | Important | Info | 7.5 | More Likely |
| CVE-2025-49719 | Important | Info | 7.5 | KNOWN EXPLOIT |
| CVE-2025-49721 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49722 | Important | DoS | 5.7 | Less Likely |
| CVE-2025-49723 | Important | Tampering | 8.8 | Less Likely |
| CVE-2025-49724 | Important | RCE | 8.8 | More Likely |
| CVE-2025-49725 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49726 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49727 | Important | EoP | 7 | More Likely |
| CVE-2025-49729 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49730 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49731 | Important | EoP | 3.1 | Less Likely |
| CVE-2025-49732 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49733 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49735 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-49737 | Important | EoP | 7 | Less Likely |
| CVE-2025-49738 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-49739 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-49740 | Important | SFB | 8.8 | Less Likely |
| CVE-2025-49741 | Important | Info | 7.4 | Less Likely |
| CVE-2025-49742 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-49744 | Important | EoP | 7 | More Likely |
| CVE-2025-49753 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49756 | Important | SFB | 3.3 | Less Likely |
| CVE-2025-49760 | Important | Spoofing | 3.5 | Less Likely |
| CVE-2025-27613 | Important | RCE | N/A | — |
| CVE-2025-27614 | Important | RCE | N/A | — |
| CVE-2025-36350 | Critical | RCE | 5.6 | — |
| CVE-2025-36357 | Critical | RCE | 5.6 | — |
| CVE-2025-46334 | Important | RCE | N/A | — |
| CVE-2025-46835 | Important | RCE | N/A | — |
| CVE-2025-48384 | Important | RCE | N/A | — |
| CVE-2025-48385 | Important | RCE | N/A | — |
| CVE-2025-48386 | Important | RCE | N/A | — |
| CVE-2025-6554 | High | RCE | N/A | — |
GOOGLE – has released a critical update for Chrome 138 addressing CVE-2025-6554, a type confusion vulnerability in the V8 JavaScript and WebAssembly engine that is actively exploited in the wild. This flaw allows remote attackers to perform arbitrary memory read and write operations via crafted HTML pages, potentially leading to denial-of-service or remote code execution. The vulnerability was disclosed on June 25 and patched the following day through a configuration update across all platforms. Immediate update is recommended to version 138.0.7204.96/.97 for Windows, 138.0.7204.92/.93 for macOS, and 138.0.7204.96 for Linux.
PALO ALTO – Palo Alto Networks has addressed multiple security vulnerabilities across its product suite, including a critical privilege escalation flaw in GlobalProtect for macOS and several command injection issues in PAN-OS.
CVE-2025-4232 is a high-severity authenticated code injection vulnerability in the GlobalProtect app on macOS (versions 6.0–6.3). It arises from improper handling of wildcard characters in the log collection feature, allowing non-administrative users to execute arbitrary code with root privileges.
CVE-2025-4231 is an authenticated administrator command injection vulnerability in the PAN-OS web interface. An authenticated admin with web interface access can execute actions as root.
CVE-2025-4230 is a command injection vulnerability via the PAN-OS CLI. An authenticated administrator with CLI access can execute arbitrary commands as root. The risk is reduced when CLI access is limited to a small group of admins.
CVE-2025-4228 involves a privilege escalation vulnerability in the Cortex XDR Broker virtual machine. An authenticated administrative user can execute certain files within the Broker VM and escalate privileges to root.
CVE-2025-4233 is a cache vulnerability in the Prisma Access browser that enables users to bypass certain control policies.
TELEPORT – Teleport developers have disclosed a critical authentication bypass vulnerability, tracked as CVE-2025-49825 with a CVSS score of 9.8, that permits remote attackers to circumvent SSH authentication and gain unauthorized access to managed systems. This flaw impacts Teleport Community Edition versions earlier than 17.5.1 and was resolved in subsequent releases including 17.5.2, 16.5.12, 15.5.3, 14.4.1, 13.4.27, and 12.4.35.
Teleport is a widely used platform that provides secure connectivity, authentication, and access management for servers, cloud applications, and infrastructure components, supporting protocols such as SSH, RDP, HTTPS, Kubernetes API, and various database connections. The vulnerability specifically affects deployments running Teleport SSH agents, configurations integrating OpenSSH, and Git proxy setups, exposing them to unauthorized remote access.
While Teleport’s cloud service customers have already received automatic updates addressing the issue, users with self-hosted Teleport agents are required to apply patches manually. For Kubernetes environments, administrators must use the dedicated teleport-kube-agent update utility instead of the generic teleport-update tool to ensure proper remediation.
Currently, there are no publicly available proof-of-concept exploits or confirmed incidents of exploitation in the wild. Nevertheless, it is imperative that all nodes within Teleport clusters be updated to the fixed versions to mitigate risk and maintain secure access controls.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by automation and AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix risk scores.
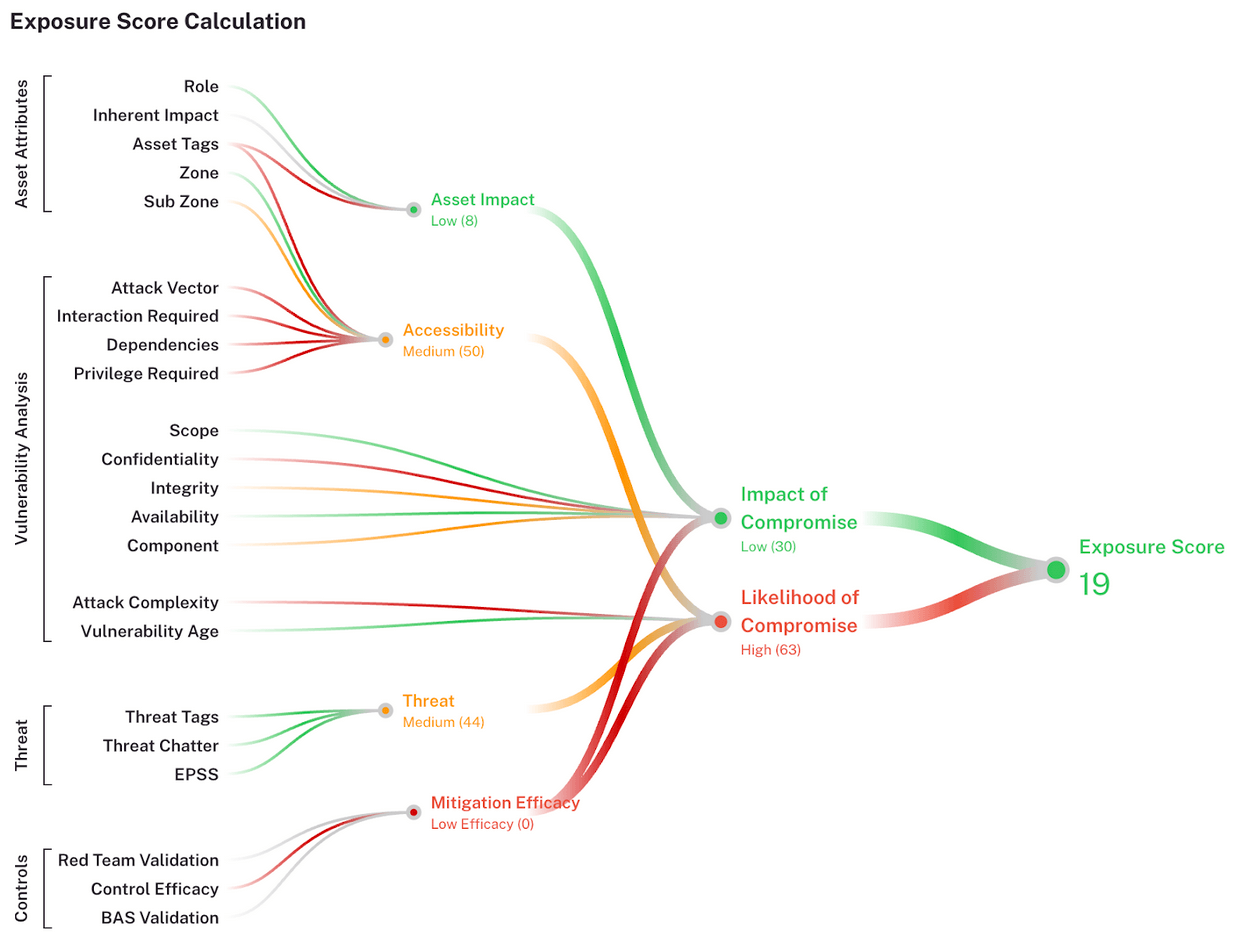
This way, Risk-Based Prioritization is proactively done, saving precious time & reducing the risk. This allows Balbix customers to simply start a Remediation Project workflow to automate, drive and manage the entire patching process – automatically calculating what patches that need to be installed on assets, cutting tickets, measuring patching progress and remediation KPIs.
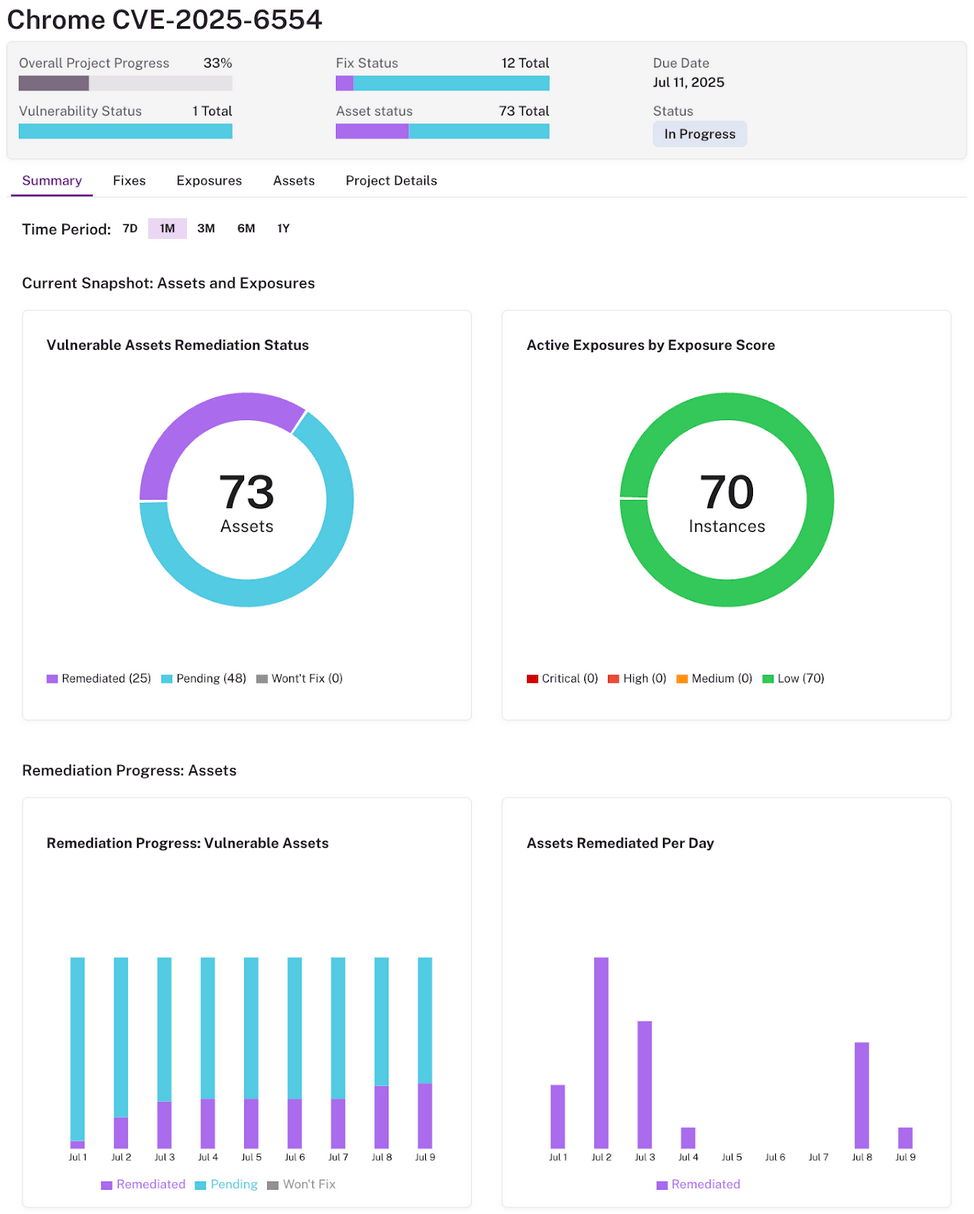
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.