
July 12, 2023
Welcome to this month’s edition of the Patch Tuesday release analysis.
Here in the US, we’ve just finished celebrating our nation’s freedom. Wouldn’t it be nice if we could all globally celebrate freedom from security vulnerabilities? However, until that happens, we must all remain on guard and vigilant. As part of that vigilance, we must pay special attention to the ever-present Microsoft vulnerabilities.
This month, Microsoft announced fixes for 129 new CVEs (up 40% from last month), including 9 Microsoft-rated critical vulnerabilities. This month there were 6 new zero-day vulnerabilities disclosed; also, there was 1 update to a previously reported exploitable vulnerability (CVE-2023-24932) as well as 1 advisory and 9 other updates to previously released CVEs and advisories.
Of the 129 new vulnerabilities, the fix sources break down as follows:
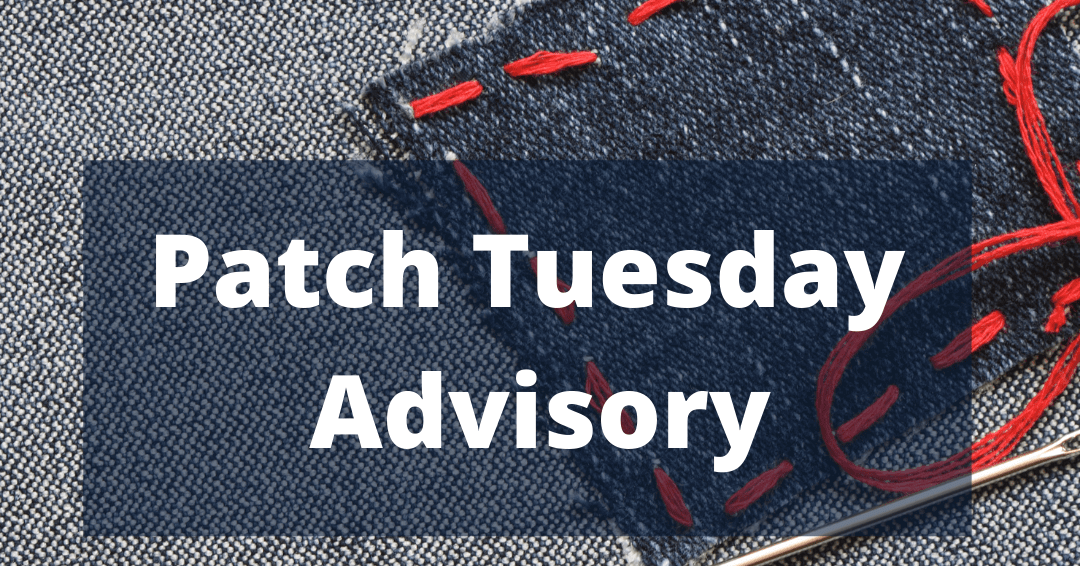
This month’s headline issues are the six (6) zero-day vulnerabilities released. The six zero-day vulnerabilities vary widely in product impact from MS Outlook to Windows SmartScreen functionality to more core services such as Windows Error Service Reporting Functionality. Their base CVE score range from 7.8 to 8.8 and provide a mix of remote code execution, elevation of privilege, and security feature bypass capability. As these zero days show, we are under constant attack with an ever more varied approach to these attacks. We must continue our in-depth defense efforts if we are to thwart these adversaries. The zero-day vulnerabilities are as follows:
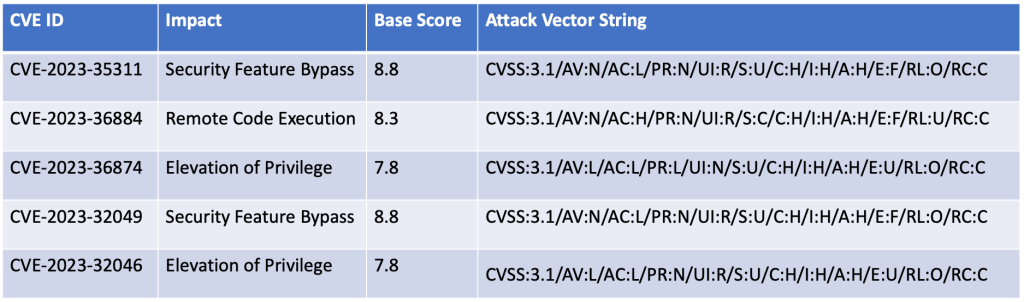
Breaking down the 129 vulnerabilities further by impact type, we can see that remote code execution leads the way again this month, with the elevation of privilege following closely behind it.
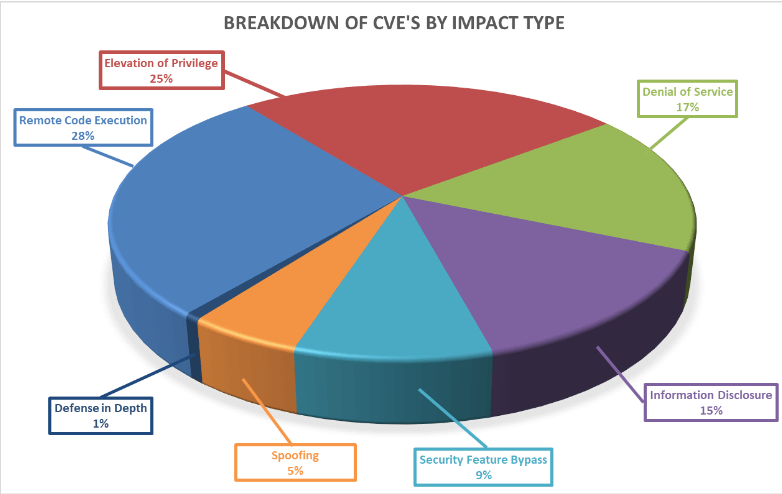
Furthermore, as seen below, these vulnerabilities vary in how likely they are to be exploited, with 10% of the vulnerabilities this month either already exploited or highly likely to be exploited, as ranked by the Microsoft Exploitability Index.
As always, Balbix can identify all affected assets within hours of release. There are no scans to run. Balbix customers simply search for the CVE name in their Balbix dashboard to view the list of affected assets. Filtered search functionality can also be used to search for the CVE by site, subnet, location, or other distinguishing factors.
If you have additional questions, please contact support@balbix.com.