

January 11, 2023
It’s a new year and the battle in cybersecurity goes on. The latest war front is this month’s Microsoft Patch Tuesday releases. For January, Microsoft announced patches for 98 vulnerabilities, including 11 that Microsoft has rated critical, 1 zero-day (CVE-2023-21674) and 1 advisory (ADV220005).
The headline issues this month are:
CVE-2023-21674, Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability
CVE-2023-21745, Microsoft Exchange Server Spoofing Vulnerability
Microsoft Exchange 2019 is particularly exposed to this month’s vulnerabilities. It has three vulnerabilities with CVSS score of 7.5+ (including CVE-2023-21745), that have an access vector which allows for exploitation as follows:
CVE-2023-21762 is a vulnerability that you’ll want to pay close attention to. It is a known exploited vulnerability which affects the advanced local procedure call (ALPC) system within Windows Server 2012 R2. ALPC is an inter-process communication facility for high-speed message passing. It is not directly available through the Windows API; it is an internal mechanism available only to Windows operating system components. This known exploitable vulnerability has the ability to change the scope of the user interaction. It also has the ability to be accessed from the local network, with low privileges, and no user interaction, allowing a user to change the scope of their privileges to more privileged position.
CVE-2023-21745, CVE-2023-21761, and CVE-2023-21764 are also vulnerabilities relating to Microsoft Exchange server 2019. All have a CVSS base score between 7.5 and 8 and allow for the impact of Spoofing, Information Disclosure, Elevation of Privileges respectively. Given the pervasiveness of the Exchange Server these CVE’s deserve particular attention.
Microsoft also released updates to the 3 existing CVEs below:
Breaking down the 48 vulnerabilities further, we can see that elevation of privileges and remote code executions lead the way this month in terms of impact type.
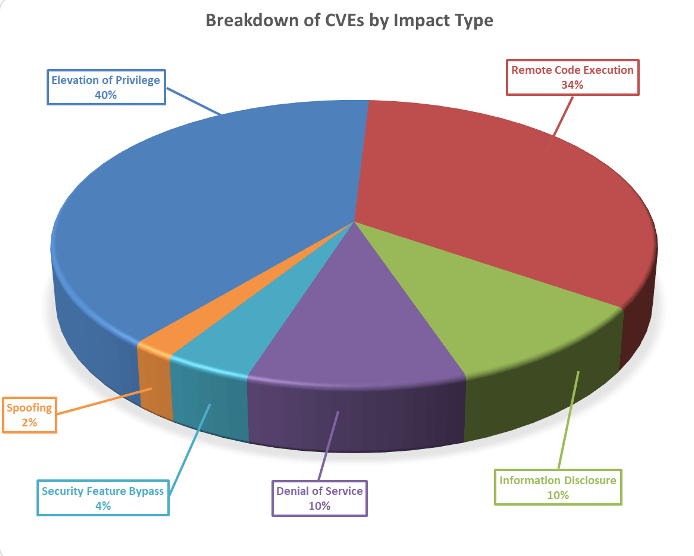
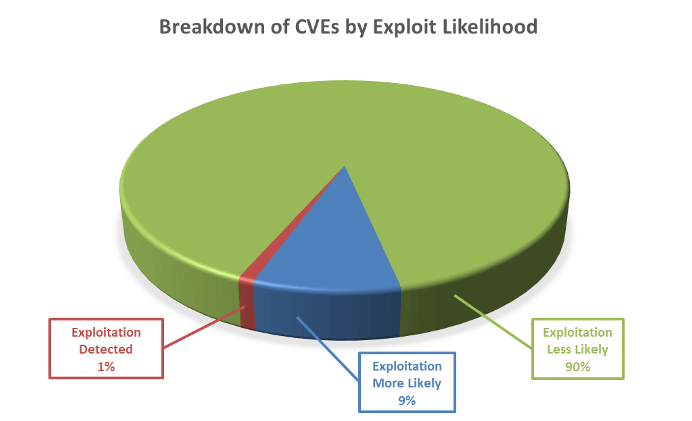
Furthermore, as can be seen below, these vulnerabilities vary in terms of how likely they are to be exploited, with 10% of the vulnerabilities this month either already exploited or highly likely to be exploited.
As always, Balbix can identify all affected assets within 1 hour of release. There are no scans to run. Balbix customers simply search for the CVE name in their Balbix dashboard to view the list of affected assets. Users can also use the filtered search functionality to search for the CVE by site, subnet, location, or other distinguishing factors