

February 17, 2023
Chocolates, flowers, jewelry…love is in the air, time to cozy up with the one you love…. Your patch management system. That’s right, it’s Patch Tuesday. For February, Microsoft announced patches for 76 vulnerabilities, including 8 that Microsoft has rated critical, and 3 zero-day (CVE-2023-23376, CVE-2023-21823, CVE-2023-21715).
The headline issues this month are the three known exploitable zero-day CVEs:
Breaking down the 76 vulnerabilities further, we can see that remote code execution and elevation of privileges lead the way this month in terms of impact type.
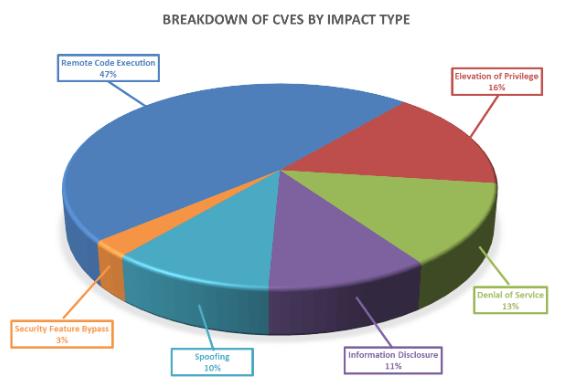
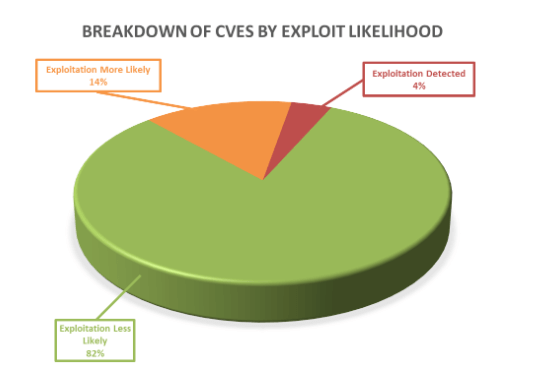
Furthermore, as can be seen below, these vulnerabilities vary in terms of how likely they are to be exploited, with 18% of the vulnerabilities this month either already exploited or highly likely to be exploited.
As always, Balbix can identify all affected assets within 1 hour of release. There are no scans to run. Balbix customers simply search for the CVE name in their Balbix dashboard to view the list of affected assets. Filtered search functionality can also be used to search for the CVE by site, subnet, location, or other distinguishing factors.