August 13, 2025
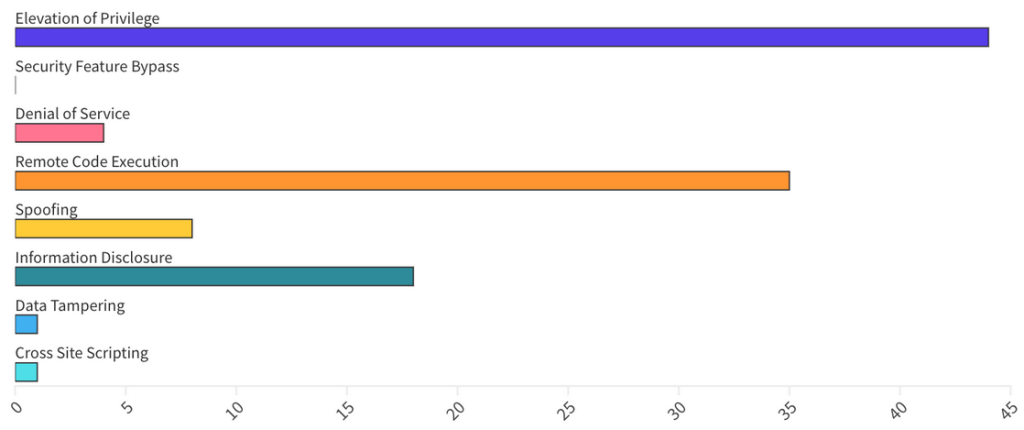
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 119 CVEs, including 8 republished CVEs. Overall, Microsoft announced 1 Zero-Day, 16 Critical, and 92 Important vulnerabilities.

From an Impact perspective, Escalation of Privilege vulnerabilities accounted for 40%, while Remove Code Execution for 32% and Information Disclosure for 16%.
Patches for this month cover components for the following areas:
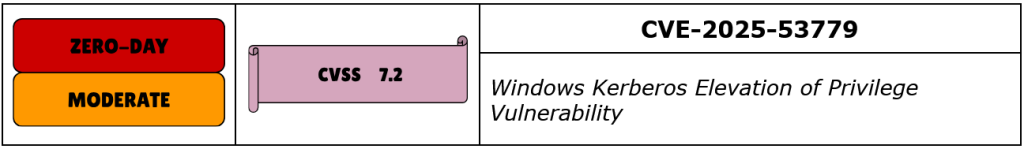
CVE-2025-53779 is an elevation of privilege (EoP) vulnerability in the Windows Kerberos authentication protocol, specifically in the handling of delegated Managed Service Accounts (dMSAs). The flaw, nicknamed “BadSuccessor” by its discoverers at Akamai, occurs when Active Directory processes the msDS-ManagedAccountPrecededByLink, msDS-DelegatedMSAState, and msDS-GroupMSAMembership attributes without sufficient privilege validation. An authenticated attacker with delegated write access to these attributes on a dMSA object can link it to a highly privileged account, such as one with Domain Administrator rights. During Kerberos authentication, the Key Distribution Center (KDC) then builds the dMSA’s Privilege Attribute Certificate (PAC) using the target account’s security identifiers, effectively granting the attacker equivalent privileges. This misconfiguration path exists even if the domain does not actively use dMSAs, as long as Windows Server 2025 domain controllers are present.
While the vulnerability requires prior authenticated access with specific Active Directory object permissions, the exploitation can occur fast and is largely invisible to standard security monitoring. Once the attacker updates the dMSA attributes, any Kerberos service ticket obtained for the manipulated account carries the privileges of the targeted high-value principal. In lab simulations, this led directly from a low-privileged domain account to full domain compromise. The researchers highlighted that delegated MSA permissions are often granted more broadly than administrators realize, making the attack surface larger than expected. Recommended detection includes monitoring for directory service Event IDs 5136 and 5137 indicating changes to dMSA objects, and Event ID 2946 signaling the issuance of a dMSA PAC.
Microsoft assigned CVE-2025-53779 a CVSS v3.1 score of 7.2 (Moderate) and patched it as the only zero-day patched this month. Exploitation is “Less Likely”, but security researchers caution that the low complexity and high impact make prompt remediation critical, especially in domains with complex service account delegations or cross-forest trusts. As of this writing, the vulnerability is not listed in CISA’s Known Exploited Vulnerabilities catalog. Organizations should deploy the August 2025 security update immediately, audit existing dMSA permissions, and restrict attribute-level writes to only the most trusted administrative accounts.
CVE-2025-53766 is a critical remote code execution (RCE) vulnerability in the Windows Graphics Device Interface (GDI+) with a CVSS score of 9.8. This flaw is a heap-based buffer overflow that allows an unauthenticated attacker to execute arbitrary code with the privileges of the logged-on user. The vulnerability is triggered during the parsing of a specially crafted metafile, a format used for storing vector graphics.
The attack vector is low-complexity and can be exploited with little to no user interaction. An attacker can deliver a malicious metafile embedded within a document (like a Word or Excel file) or a specially crafted image. The vulnerability can also be triggered automatically on systems or web services that automatically parse or render documents containing these metafiles, such as document preview panes in email clients or server-side document processing services. This makes the vulnerability particularly dangerous as it can be exploited in a “worm-like” manner to achieve lateral movement within a network or compromise web services without user involvement.
Upon successful exploitation, the buffer overflow can be leveraged to corrupt the heap, hijack the control flow of the program, and execute malicious code in the context of the user or system process running the vulnerable GDI+ component. The vulnerability was reported by a security researcher at Check Point, and Microsoft has released patches for Windows 10, Windows 11, and Windows Server to fix the issue.
CVE-2025-53740 is a critical remote code execution (RCE) vulnerability in Microsoft Office with a CVSS score of 8.4. This is a classic use-after-free (UAF) flaw, which is a type of memory corruption bug (CWE-416). The vulnerability occurs when the application attempts to use a block of memory that has been deallocated. An attacker can exploit this by crafting a malicious document that triggers the use-after-free condition. When the freed memory is reused for attacker-controlled data, it can corrupt the program’s state, leading to control flow hijacking and arbitrary code execution.
The most concerning attack vector for this vulnerability is the Preview Pane in Microsoft Office and Outlook. The flaw can be triggered simply by a user viewing the malicious document in the preview pane, without having to open the file completely. This significantly lowers the bar for a successful attack, as it requires minimal user interaction. Microsoft has rated the attack complexity as “low” and the privileges required as “none.” While exploitation is assessed as “less likely”, the potential for a no-click RCE makes this a serious threat. Microsoft has released security updates for all supported versions of Office, including Microsoft 365 Apps for Enterprise and various Office LTSC editions, to address this flaw.
CVE-2025-50171 is a Remote Desktop Protocol (RDP) spoofing vulnerability with a CVSS score of 9.1. The vulnerability is tied to the RDP server’s certificate validation process, and should be handled with priority considering the wide-spread usage of RDP.
An attacker can exploit this by setting up a malicious RDP server and presenting a forged or self-signed certificate that mimics a legitimate, trusted server. The flaw lies in how the RDP client, by default, may not adequately validate the authenticity of the server’s certificate, especially in scenarios where it’s not a public trusted certificate authority.
This vulnerability is a man-in-the-middle type of attack. The attacker must be on the same network as the victim to intercept the RDP connection. By spoofing the server, the attacker can trick the user into connecting to their malicious server instead of the intended destination. Once the connection is established, the attacker can perform various malicious actions, most notably stealing the user’s credentials.
While it doesn’t allow for direct code execution, the stolen credentials could then be used for more sophisticated attacks, including privilege escalation and lateral movement within the network. This highlights the importance of enforcing strict certificate validation policies and using network-level authentication (NLA) to prevent unauthenticated connections.
CVE-2025-53778 is an Elevation of Privilege (EoP) vulnerability in the Windows NTLM (NT LAN Manager) authentication protocol, carrying a CVSS score of 8.8 (High). This flaw is an improper authentication issue (CWE-287), but the attack vector is more complex than a simple logon bypass. It specifically exploits a weakness in how NTLM handles challenge-response authentication requests. A low-privileged attacker on the network can leverage this weakness to capture and relay a user’s NTLM hash, effectively authenticating as that user to other services.
The vulnerability has low attack complexity but requires an initial foothold on the network. The attack chain typically involves an NTLM relay attack, where the attacker uses a compromised machine to intercept and forward a legitimate user’s authentication request to a target service, such as a domain controller or another server. This exploit does not require cracking the user’s password; instead, it relies on relaying the NTLM hash itself. By doing so, the attacker can impersonate the user and perform actions with their privileges. If the targeted user is a domain administrator, the attacker can gain SYSTEM-level access on the domain controller, which would result in a full compromise of the Active Directory environment. Microsoft has assessed that exploitation is “more likely”, making this a critical vulnerability that requires immediate patching across multiple versions of Windows, including Windows 10, Windows 11, and Windows Server 2022. The patch addresses the improper handling of the NTLM challenge-response mechanism, preventing the relay attack.
CVE-2025-53144 is a Remote Code Execution (RCE) vulnerability that exists within the Microsoft Message Queuing (MSMQ) component. This is a critical distinction, as it changes the vulnerability from a moderate-risk data leak to a high-risk code execution. The vulnerability is a heap-based buffer overflow (CWE-122) that could be triggered by an attacker sending a specially crafted malicious message to a vulnerable MSMQ server.
The attack can be carried out over the network without requiring any user interaction or authentication. If the MSMQ service is running, an unauthenticated attacker can send a malformed message that overflows a heap buffer, leading to memory corruption. This corruption can be leveraged to achieve code execution with the privileges of the MSMQ service, which often runs with elevated permissions. This type of vulnerability is particularly dangerous because it can be wormable, meaning it could spread autonomously across a network without any user action.
CVE-2025-53145 is a Remote Code Execution (RCE) vulnerability found in Microsoft Message Queuing (MSMQ) with a CVSS score of 8.8 (High). This flaw is a heap-based buffer overflow, similar in nature to CVE-2025-53144. It allows an unauthenticated attacker to execute arbitrary code on a system running the vulnerable MSMQ service by sending a specially crafted malicious message.
This is a wormable vulnerability that can be exploited remotely without authentication or user interaction. An attacker can send a malformed MSMQ packet to a vulnerable server, which triggers the heap buffer overflow and allows for memory corruption. The attacker can then use this to achieve code execution with the privileges of the MSMQ service. Because the vulnerability is wormable and has a low attack complexity, it poses a severe risk to unpatched systems.
| CVE | Severity | Type | CVSS | Exploitation |
|---|---|---|---|---|
| CVE-2025-24999 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-25005 | Important | Tampering | 6.5 | Less Likely |
| CVE-2025-25006 | Important | Spoofing | 5.3 | Less Likely |
| CVE-2025-25007 | Important | Spoofing | 5.3 | Less Likely |
| CVE-2025-33051 | Important | Info | 7.5 | Less Likely |
| CVE-2025-47954 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-48807 | Critical | RCE | 7.5 | Less Likely |
| CVE-2025-49707 | Critical | Spoofing | 7.9 | Less Likely |
| CVE-2025-49712 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-49736 | Moderate | Spoofing | 4.3 | Unlikely |
| CVE-2025-49743 | Important | EoP | 6.7 | More Likely |
| CVE-2025-49745 | Important | XSS | 5.4 | Less Likely |
| CVE-2025-49751 | Important | DoS | 6.8 | Less Likely |
| CVE-2025-49755 | Low | Spoofing | 4.3 | Unlikely |
| CVE-2025-49757 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-49758 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-49759 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-49761 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-49762 | Important | EoP | 7 | Less Likely |
| CVE-2025-50153 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-50154 | Important | Spoofing | 7.5 | Unlikely |
| CVE-2025-50155 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-50156 | Important | Info | 5.7 | Less Likely |
| CVE-2025-50157 | Important | Info | 5.7 | Unlikely |
| CVE-2025-50158 | Important | Info | 7 | Less Likely |
| CVE-2025-50159 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-50160 | Important | RCE | 8 | Less Likely |
| CVE-2025-50161 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-50162 | Important | RCE | 8 | Unlikely |
| CVE-2025-50163 | Important | RCE | 8.8 | Unlikely |
| CVE-2025-50164 | Important | RCE | 8 | Unlikely |
| CVE-2025-50165 | Important | RCE | 9.8 | Less Likely |
| CVE-2025-50166 | Important | Info | 6.5 | Less Likely |
| CVE-2025-50167 | Important | EoP | 7 | More Likely |
| CVE-2025-50168 | Important | EoP | 7.8 | More Likely |
| CVE-2025-50169 | Important | RCE | 7.5 | Unlikely |
| CVE-2025-50170 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-50171 | Important | Spoofing | 9.1 | Less Likely |
| CVE-2025-50172 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-50173 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-50176 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-50177 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-53131 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-53132 | Important | EoP | 8 | More Likely |
| CVE-2025-53133 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53134 | Important | EoP | 7 | Less Likely |
| CVE-2025-53135 | Important | EoP | 7 | Less Likely |
| CVE-2025-53136 | Important | Info | 5.5 | Less Likely |
| CVE-2025-53137 | Important | EoP | 7 | Less Likely |
| CVE-2025-53138 | Important | Info | 5.7 | Unlikely |
| CVE-2025-53140 | Important | EoP | 7 | Less Likely |
| CVE-2025-53141 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53142 | Important | EoP | 7 | Less Likely |
| CVE-2025-53143 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-53144 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-53145 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-53147 | Important | EoP | 7 | More Likely |
| CVE-2025-53148 | Important | Info | 5.7 | Less Likely |
| CVE-2025-53149 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53151 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53152 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53153 | Important | Info | 5.7 | Less Likely |
| CVE-2025-53154 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53155 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53156 | Important | Info | 5.5 | More Likely |
| CVE-2025-53716 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-53718 | Important | EoP | 7 | Less Likely |
| CVE-2025-53719 | Important | Info | 5.7 | Less Likely |
| CVE-2025-53720 | Important | RCE | 8 | Unlikely |
| CVE-2025-53721 | Important | EoP | 7 | Less Likely |
| CVE-2025-53722 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-53723 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53724 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-53725 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-53726 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-53727 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-53728 | Important | Info | 6.5 | Less Likely |
| CVE-2025-53729 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-53730 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-53731 | Critical | RCE | 8.4 | Unlikely |
| CVE-2025-53732 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53733 | Critical | RCE | 8.4 | Less Likely |
| CVE-2025-53734 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53735 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53736 | Important | Info | 6.8 | Less Likely |
| CVE-2025-53737 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53738 | Important | RCE | 7.8 | Unlikely |
| CVE-2025-53739 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53740 | Critical | RCE | 8.4 | Less Likely |
| CVE-2025-53741 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53759 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53760 | Important | EoP | 7.1 | Less Likely |
| CVE-2025-53761 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53765 | Important | Info | 4.4 | Unlikely |
| CVE-2025-53766 | Critical | RCE | 9.8 | Less Likely |
| CVE-2025-53767 | Critical | EoP | 10 | – |
| CVE-2025-53769 | Important | Spoofing | 5.5 | Less Likely |
| CVE-2025-53772 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-53773 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-53774 | Critical | Info | 6.5 | Less Likely |
| CVE-2025-53778 | Critical | EoP | 8.8 | More Likely |
| CVE-2025-53779 | Moderate | EoP | 7.2 | KNOWN EXPLOIT |
| CVE-2025-53781 | Critical | Info | 7.7 | Less Likely |
| CVE-2025-53783 | Important | RCE | 7.5 | Less Likely |
| CVE-2025-53784 | Critical | RCE | 8.4 | Unlikely |
| CVE-2025-53786 | Important | EoP | 8 | More Likely |
| CVE-2025-53787 | Critical | Info | 8.2 | – |
| CVE-2025-53788 | Important | EoP | 7 | Unlikely |
| CVE-2025-53789 | Important | EoP | 7.8 | Unlikely |
| CVE-2025-53792 | Critical | EoP | 9.1 | – |
| CVE-2025-53793 | Critical | Info | 7.5 | Unlikely |
| CVE-2025-8576 | High | – | 8.8 | – |
| CVE-2025-8577 | Moderate | – | 4.3 | – |
| CVE-2025-8578 | High | – | 8.8 | – |
| CVE-2025-8579 | Low | – | 4.3 | – |
| CVE-2025-8580 | Low | – | 4.3 | – |
| CVE-2025-8581 | Low | – | 4.3 | – |
| CVE-2025-8582 | Low | – | 4.3 | – |
| CVE-2025-8583 | Low | – | 4.3 | – |
QUALCOMM – The August 2025 Android Security Bulletin highlighted two critical Qualcomm vulnerabilities (CVE-2025-27038 and CVE-2025-21479) that are being actively exploited in limited, targeted attacks. While the specifics of the exploit are not fully detailed, the active exploitation of these flaws makes them a priority for Android device manufacturers and users. These are both tied to the Graphics component. CVE-2025-27038 is a use-after-free vulnerability in the Adreno GPU drivers. It could lead to memory corruption when rendering graphics in a browser like Chrome. The CVSS 3.1 score is 7.5. CVE-2025-21479 is an incorrect authorization vulnerability within the GPU micronode. This flaw allows for unauthorized command execution in the GPU’s microcode, which can lead to memory corruption. This has a CVSS 3.1 score of 8.6.
ADOBE – Adobe released an emergency patch for two zero-day vulnerabilities in Adobe Experience Manager (AEM) Forms on JEE that had public proof-of-concept exploits. CVE-2025-54253 is a critical Remote Code Execution (RCE) vulnerability with a CVSS score of 10.0. The flaw is an authentication bypass in the admin UI, which, when combined with a Java deserialization flaw, allows an attacker to execute code on the server without authentication. CVE-2025-54254 is an Improper Restriction of XML External Entity Reference (XXE) vulnerability with a CVSS score of 8.6, allowing an unauthenticated attacker to read sensitive local files.
7-ZIP – The vulnerability in 7-Zip, CVE-2025-55188, is an Improper Link Resolution Before File Access, or a path traversal vulnerability. The issue arises from how 7-Zip handles symbolic links during archive extraction. A specially crafted archive can trick the software into following a symbolic link to an unintended location, allowing an attacker to write files to arbitrary directories and potentially achieve code execution. The official CVSS score is 3.6, but the researcher who discovered it argues this is underreported given the potential for arbitrary file writes.
WINRAR – A critical path traversal vulnerability, CVE-2025-8088, was found and actively exploited in WinRAR. The flaw affects the Windows version of the software. An attacker can craft a malicious archive file that uses alternate data streams to hide malicious files. When the archive is extracted, the hidden files are deployed to unintended directories, such as the Windows Startup folder, allowing for persistence and remote code execution. This vulnerability has a CVSS score of 8.4.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by automation and AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix risk scores.
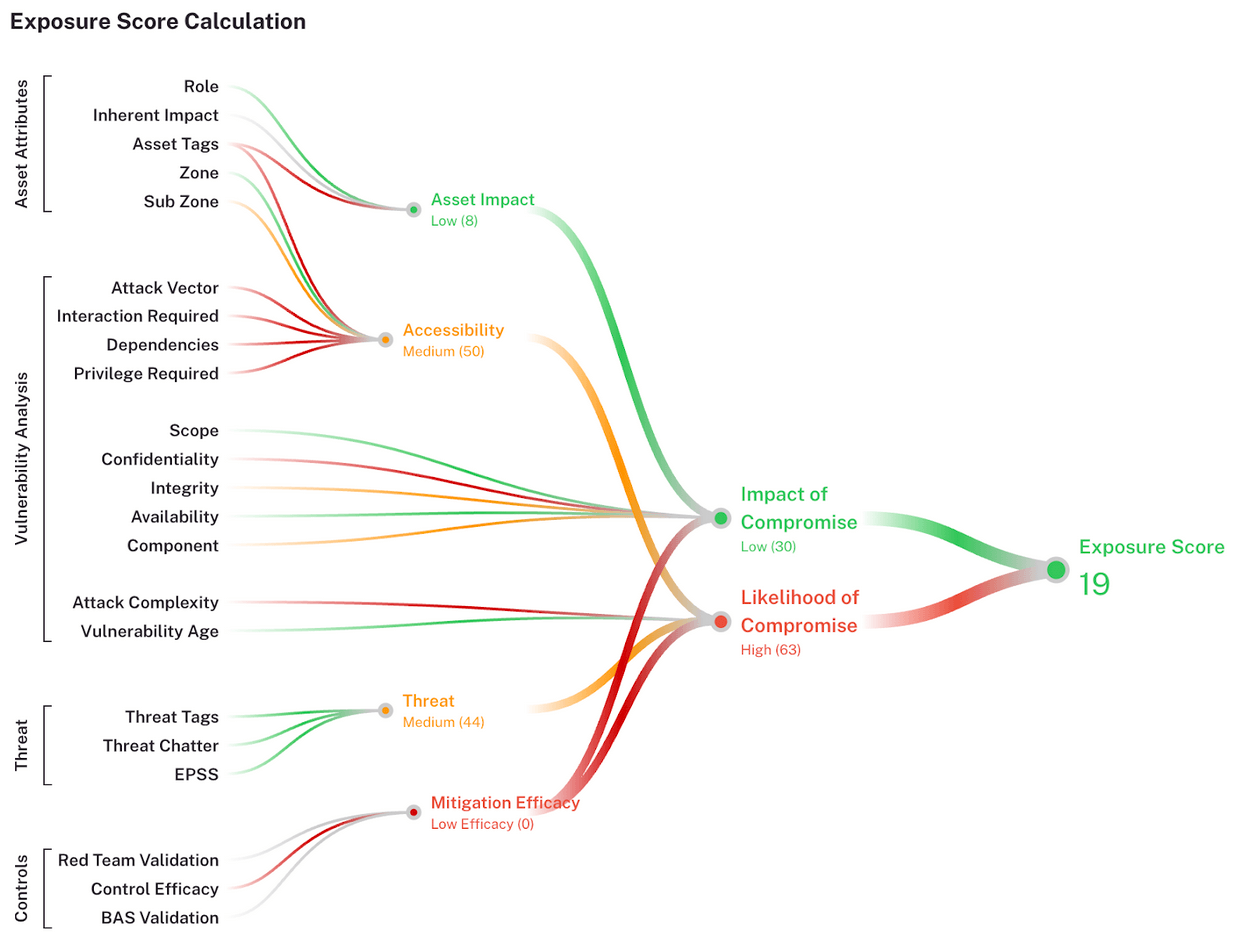
This way, Risk-Based Prioritization is proactively done, saving precious time & reducing the risk. This allows Balbix customers to simply start a Remediation Project workflow to automate, drive and manage the entire patching process – automatically calculating what patches that need to be installed on assets, cutting tickets, measuring patching progress and remediation KPIs.
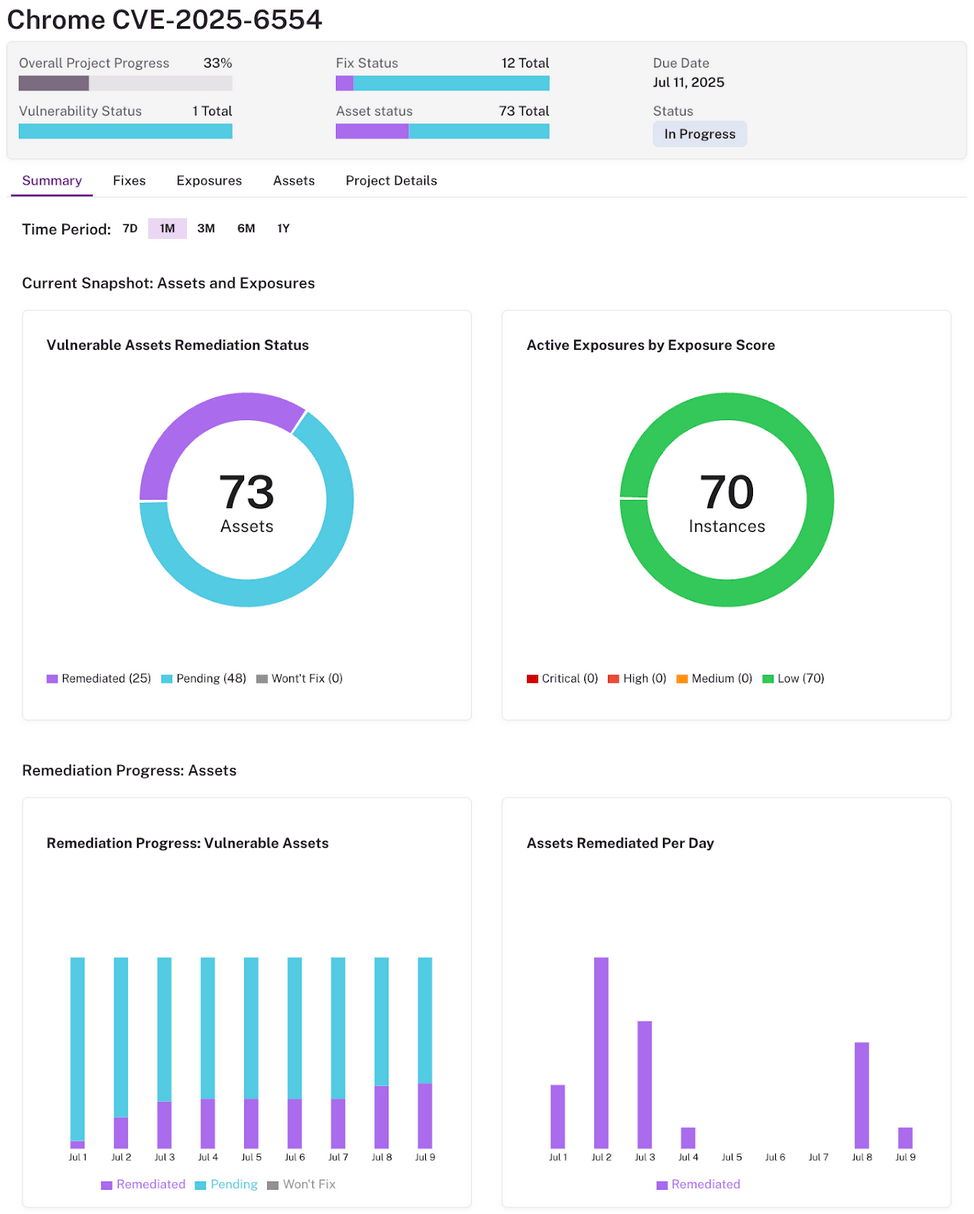
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.