April 9, 2025
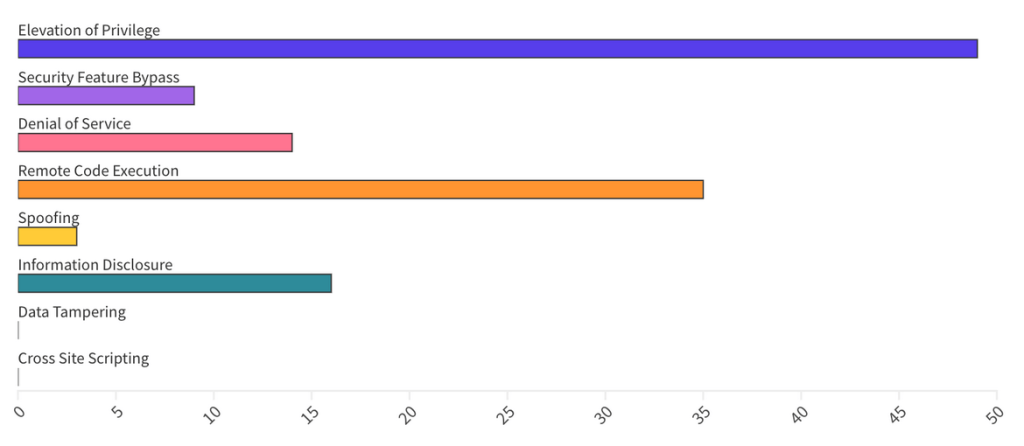
In total, including third-party CVEs, in this Patch Tuesday edition, Microsoft published 134 CVEs, including 9 republished CVEs. Overall, Microsoft announced one Zero-Day, 11 Critical, and 113 Important vulnerabilities.

From an Impact perspective, Escalation of Privilege (EoP) vulnerabilities accounted for 39%, followed by Remote Code Execution (RCE) at 28% and Information Disclosure (ID) at 13%.
Patches for this month cover components for the following areas:
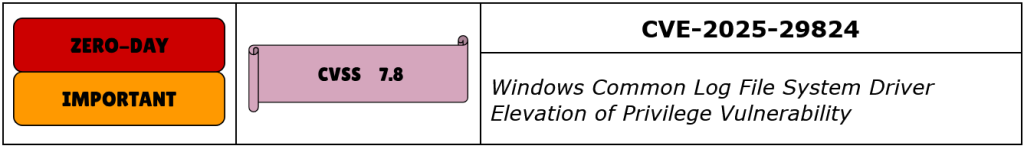
CVE-2025-29824 is a high-severity use-after-free vulnerability in the Windows Common Log File System (CLFS) driver, which has been actively exploited in the wild, notably by the RansomEXX ransomware group. This flaw allows authenticated local attackers to elevate their privileges to SYSTEM level on affected Windows systems.
The vulnerability stems from improper handling of objects in memory by the CLFS driver, leading to a use-after-free condition. An attacker who successfully exploits this flaw can execute arbitrary code with SYSTEM privileges, effectively gaining control over the compromised system.
Microsoft addressed CVE-2025-29824 in the April 2025 Patch Tuesday. However, updates for Windows 10 x64-based and 32-bit systems were not immediately available; Microsoft has indicated that these updates will be released as soon as possible. In the interim, organizations using these versions should implement additional security measures to mitigate exploitation.
CISA has added CVE-2025-29824 to its KEV Catalog, underscoring the importance of prompt remediation. Organizations are strongly advised to apply the available patches immediately and monitor for the release of updates for any remaining affected systems to mitigate the risk.
CVE-2025-26663 and CVE-2025-26670 are critical remote code execution (RCE) vulnerabilities affecting the Windows Lightweight Directory Access Protocol (LDAP) and its client components.
CVE-2025-26663 is Use-After-Free, Remote Code Execution (RCE) vulnerability in the Windows LDAP service. An unauthenticated attacker can exploit this flaw by sending a specially crafted LDAP request to a vulnerable server, leading to a use-after-free condition. Successful exploitation could allow the attacker to execute arbitrary code within the context of the LDAP service. Microsoft has assessed that exploitation of this vulnerability is “more likely,” despite the high attack complexity due to the required race condition.
CVE-2025-26670 is another Use-After-Free, Remote Code Execution (RCE) vulnerability in the Windows LDAP client. An attacker can exploit this vulnerability by sending sequential specially crafted LDAP requests to a vulnerable LDAP server. Winning the race condition could allow an attacker to execute malicious code. Similar to CVE-2025-26663, Microsoft has assessed that exploitation of this vulnerability is “more likely,” acknowledging the high attack complexity involved. Microsoft noted that an attacker would need to control or impersonate an LDAP server and exploitation would require precise timing of events.
CVE-2025-27480 and CVE-2025-27482 are critical remote code execution (RCE) vulnerabilities in the Windows Remote Desktop Gateway Service.
CVE-2025-27480 is a use-after-free vulnerability in the Remote Desktop Gateway Service. An unauthenticated attacker can exploit this flaw by connecting to a system with the Remote Desktop Gateway role and triggering a race condition that leads to the use-after-free scenario. Successful exploitation could allow the attacker to execute arbitrary code within the context of the service. Despite the high attack complexity due to the required race condition, Microsoft has assessed that exploitation of this vulnerability is “more likely”.
CVE-2025-27482 involves sensitive data storage in improperly locked memory within the Remote Desktop Gateway Service. An unauthenticated attacker can exploit this vulnerability by connecting to a vulnerable system and triggering a race condition, leading to a use-after-free scenario. This could result in arbitrary code execution. Similar to CVE-2025-27480, Microsoft has assessed that exploitation of this vulnerability is “more likely,” acknowledging the high attack complexity involved.
CVE-2025-27745, CVE-2025-27748 and CVE-2025-27749 are critical remote code execution (RCE) vulnerabilities in Microsoft Office components.
CVE-2025-27745 is caused by improper memory handling in Microsoft Office, specifically when certain document objects are deallocated but still accessed by the application. A crafted file can trigger a use-after-free condition, leading to remote code execution. The exploit requires the user to open a malicious Office document. The attacker does not need privileges on the system, but user interaction is necessary.
Similar in nature to CVE-2025-27745, CVE-2025-27748 stems from memory being released too early in the lifecycle of Office objects. If exploited via a crafted document, it can allow arbitrary code execution in the context of the user. The vulnerability has the same base CVSS score and impact metrics, suggesting it targets a similar internal Office component or rendering process.
While less detail is publicly available, CVE-2025-27749 vulnerability is also believed to stem from memory corruption or unsafe object handling during document processing. It can lead to remote code execution if a user opens a specially crafted Office file. Like the others, the vulnerability requires user interaction but no prior system access, and successful exploitation results in complete compromise of the user’s session.
| CVE | Severity | Type | CVSS | Exploitation |
| CVE-2025-20570 | Important | EoP | 6.8 | Less Likely |
| CVE-2025-21174 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-21191 | Important | EoP | 7 | Less Likely |
| CVE-2025-21197 | Important | Info | 6.5 | Less Likely |
| CVE-2025-21203 | Important | Info | 6.5 | Less Likely |
| CVE-2025-21204 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-21205 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-21221 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-21222 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-24058 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-24060 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-24062 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-24073 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-24074 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-25000 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-25001 | Low | Spoofing | 4.3 | Less Likely |
| CVE-2025-25002 | Important | Info | 6.8 | Less Likely |
| CVE-2025-26628 | Important | Info | 7.3 | Less Likely |
| CVE-2025-26635 | Important | SFB | 6.5 | Less Likely |
| CVE-2025-26637 | Important | SFB | 6.8 | Less Likely |
| CVE-2025-26639 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-26640 | Important | EoP | 7 | Less Likely |
| CVE-2025-26641 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-26642 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-26644 | Important | Spoofing | 6.2 | Less Likely |
| CVE-2025-26647 | Important | EoP | 8.1 | Less Likely |
| CVE-2025-26648 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-26649 | Important | EoP | 7 | Less Likely |
| CVE-2025-26651 | Important | DoS | 6.5 | Less Likely |
| CVE-2025-26652 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-26663 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-26664 | Important | Info | 6.5 | Less Likely |
| CVE-2025-26665 | Important | EoP | 7 | Less Likely |
| CVE-2025-26666 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-26667 | Important | RCE | 6.5 | Less Likely |
| CVE-2025-26668 | Important | RCE | 7.5 | Less Likely |
| CVE-2025-26669 | Important | Info | 8.8 | Less Likely |
| CVE-2025-26670 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-26671 | Important | RCE | 8.1 | Less Likely |
| CVE-2025-26672 | Important | Info | 6.5 | Less Likely |
| CVE-2025-26673 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-26674 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-26675 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-26676 | Important | Info | 6.5 | Less Likely |
| CVE-2025-26678 | Important | SFB | 8.4 | Less Likely |
| CVE-2025-26679 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-26680 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-26681 | Important | EoP | 6.7 | Less Likely |
| CVE-2025-26682 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-26686 | Critical | RCE | 7.5 | Less Likely |
| CVE-2025-26687 | Important | EoP | 7.5 | Less Likely |
| CVE-2025-26688 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27467 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27469 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-27470 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-27471 | Important | DoS | 5.9 | Less Likely |
| CVE-2025-27472 | Important | SFB | 5.4 | More Likely |
| CVE-2025-27473 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-27474 | Important | Info | 6.5 | Less Likely |
| CVE-2025-27475 | Important | EoP | 7 | Less Likely |
| CVE-2025-27476 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27477 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-27478 | Important | EoP | 7 | Less Likely |
| CVE-2025-27479 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-27480 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-27481 | Important | RCE | 8.8 | Less Likely |
| CVE-2025-27482 | Critical | RCE | 8.1 | More Likely |
| CVE-2025-27483 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27484 | Important | EoP | 7.5 | Less Likely |
| CVE-2025-27485 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-27486 | Important | DoS | 7.5 | Less Likely |
| CVE-2025-27487 | Important | RCE | 8 | Less Likely |
| CVE-2025-27489 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27490 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27491 | Critical | RCE | 7.1 | Less Likely |
| CVE-2025-27492 | Important | EoP | 7 | Less Likely |
| CVE-2025-27727 | Important | EoP | 7.8 | More Likely |
| CVE-2025-27728 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27729 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-27730 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27731 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27732 | Important | EoP | 7 | Less Likely |
| CVE-2025-27733 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27735 | Important | SFB | 6 | Less Likely |
| CVE-2025-27736 | Important | Info | 5.5 | Less Likely |
| CVE-2025-27737 | Important | SFB | 8.6 | Less Likely |
| CVE-2025-27738 | Important | Info | 6.5 | Less Likely |
| CVE-2025-27739 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27740 | Important | EoP | 8.8 | Less Likely |
| CVE-2025-27741 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27742 | Important | Info | 5.5 | Less Likely |
| CVE-2025-27743 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27744 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-27745 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-27746 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-27747 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-27748 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-27749 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-27750 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-27751 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-27752 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-29791 | Critical | RCE | 7.8 | Less Likely |
| CVE-2025-29792 | Important | EoP | 7.3 | More Likely |
| CVE-2025-29793 | Important | RCE | 7.2 | More Likely |
| CVE-2025-29794 | Important | RCE | 8.8 | More Likely |
| CVE-2025-29796 | Low | Spoofing | 4.7 | Less Likely |
| CVE-2025-29800 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-29801 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-29802 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-29803 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-29804 | Important | EoP | 7.3 | Less Likely |
| CVE-2025-29805 | Important | Info | 7.5 | Less Likely |
| CVE-2025-29808 | Important | Info | 5.5 | Less Likely |
| CVE-2025-29809 | Important | SFB | 7.1 | More Likely |
| CVE-2025-29810 | Important | EoP | 7.5 | Less Likely |
| CVE-2025-29811 | Important | EoP | 7.8 | Less Likely |
| CVE-2025-29812 | Important | EoP | 7.8 | More Likely |
| CVE-2025-29815 | Important | RCE | 7.6 | Less Likely |
| CVE-2025-29816 | Important | SFB | 7.5 | Less Likely |
| CVE-2025-29817 | Important | RCE | 5.7 | Less Likely |
| CVE-2025-29819 | Important | Info | 6.2 | Less Likely |
| CVE-2025-29820 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-29821 | Important | Info | 5.5 | Less Likely |
| CVE-2025-29822 | Important | SFB | 7.8 | Less Likely |
| CVE-2025-29823 | Important | RCE | 7.8 | Less Likely |
| CVE-2025-29824 | Important | EoP | 7.8 | KNOWN EXPLOIT |
| CVE-2025-3066 | High | — | — | — |
| CVE-2025-3067 | Medium | — | — | — |
| CVE-2025-3068 | Medium | — | — | — |
| CVE-2025-3069 | Medium | — | — | — |
| CVE-2025-3070 | Medium | — | — | — |
| CVE-2025-3071 | Low | — | — | — |
| CVE-2025-3072 | Low | — | — | — |
| CVE-2025-3073 | Low | — | — | — |
| CVE-2025-3074 | Low | — | — | — |
APPLE – Apple has released security updates for older versions of its operating systems, incorporating patches for vulnerabilities that were previously exploited as zero-day in the wild.
CVE-2025-24200 is an authorization vulnerability in Apple’s iOS and iPadOS operating systems that was addressed with improved state management in iOS 18.3.1 and iPadOS 18.3.1. This flaw allowed a physical attacker to disable USB Restricted Mode on a locked device, potentially facilitating unauthorized data access. Apple acknowledged reports indicating that this vulnerability may have been exploited in sophisticated attacks targeting specific individuals.
Alongside the backported patches, Apple also issued security updates for the most recent stable versions of its operating systems and applications, including Safari and Xcode. Notably, the iOS 18.4 updates address a total of 77 vulnerabilities, including CVE-2025-30456, which involves an app sandbox bypass that could lead to root privilege escalation, CVE-2025-24097, which allows unauthorized access to file metadata, and CVE-2025-31182, which allows file deletion.
NEXT.JS – A critical vulnerability in the Next.js React framework, tracked as CVE-2025-29927, has been identified and carries a CVSS score of 9.1. Under specific conditions, the flaw allows attackers to bypass authorization, potentially granting unauthorized access to various resources.
The issue stems from how Next.js handles the internal x-middleware-subrequest header, which is used to prevent infinite request loops by marking internal subrequests. If this header is spoofed or manipulated in incoming HTTP requests, it can cause middleware logic to be entirely skipped. This includes skipping critical security checks such as authentication and authorization validation—particularly those tied to session or authorization cookies.
FORTINET – Has released patches for multiple products, including FortiOS, FortiProxy, FortiPAM, FortiAnalyzer, FortiManager, FortiSandbox, FortiNDR, FortiSIEM, FortiWeb, and FortiADC. Key issues include CVE-2023-48790, an XSS flaw in FortiNDR that allows remote code execution; CVE-2024-45325, a critical bug in several products enabling command execution by privileged attackers; and CVE-2023-40723, which lets unauthenticated users extract database passwords in FortiSIEM. FortiSandbox also received fixes for privilege escalation, command injection, and unauthorized access flaws. Most bugs were found internally with no sign of active exploitation.
GOOGLE – Kaspersky reported that CVE-2025-2783 zero-day in Chrome was seen exploited in targeted attacks using phishing emails linked to a fake “Primakov Readings” site. The issue is caused by a logic error between Chrome’s sandbox and Windows, enabling sandbox escape with no user interaction.
MOZILLA – Firefox 137 fixes 14 vulnerabilities, 13 of which are high severity, primarily due to memory issues like buffer overflows and use-after-free bugs that could enable code execution via malicious web pages. Notable flaws include: CVE-2025-3028 – Use-after-free in XSLTProcessor allowing code execution, CVE-2025-3032 – File descriptor leak weakening sandbox isolation and CVE-2025-3029 – Unicode-based URL spoofing for phishing attacks.
As always, you should patch everything as soon as possible… 😉
But that’s a lot easier said than done. The strategy prioritizes what matters most and reduces the vulnerabilities with the greatest business impact. For this, organizations must improve how they measure, quantify, prioritize, and communicate risk. Balbix offers the following AI-powered capabilities:
#1 – CAASM > Understand your attack surface. An accurate & up-to-date inventory of on-premises, cloud, IoT/OT assets and software bill of materials (SBOM) is fundamental. Additionally, organizations need to understand:
#2 – RVBM > Prioritize and remediate critical vulnerabilities. Use severity, threat intelligence, asset exposure, compensating controls and business context to understand which vulnerabilities are exploited and the financial impact of it (if exploited) to your organization. Use this data to prioritize ruthlessly.
#3 – CRQ > Quantify Cyber Risk. Using a language that is easily understandable by all, i.e., monetary or currencies. It’s the only way to effectively communicate and compare risk across all different environments, software, geos, business units, etc.
But the true magic of Balbix happens when you put all these together:
The Balbix Platform started doing its homework as soon as vendors announced CVEs. No human interaction is needed. It’s all driven by AI. It learned about the new CVEs and the Cyber Threat Intelligence associated with each of them, and it correlated with each asset’s technical and business context to calculate the Balbix scores.
This way, Risk-Based Prioritization is already done, and Balbix customers can simply start a Patch Prioritization workflow and automatically get the latest KB that needs to be installed on a set of assets / OS.
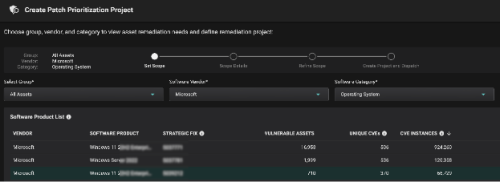
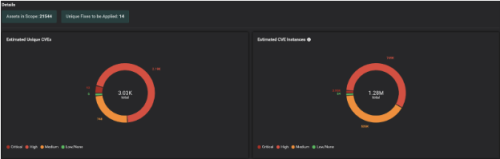
This way, Balbix customers clearly understand the assets in scope, unique CVE detections, unique patches to be applied, etc., and most importantly, the priority in which patches need to be installed to burn down risk in the most efficient way possible.
If you want to learn more, please sign up for a Balbix demo.