
September 11, 2025
If you’ve been anywhere near cybersecurity leadership circles lately, you’ve probably heard the acronym CTEM tossed around a lot. Continuous Threat Exposure Management promises a framework for staying ahead of an endlessly shifting attack surface. But here’s the catch: a framework is only as good as the engines that drive it.
That was the heart of our recent webinar with Gaurav Banga, Founder & CEO of Balbix, and Vinay Sridhara, CTO & Head of Engineering. They peeled back the buzzwords to show how Exposure Management (EM) and Cyber Risk Quantification (CRQ) together transform CTEM from theory into a repeatable, defensible program that actually reduces risk, and proves it in business terms.
Balbix frames CTEM as a journey in three distinct phases:
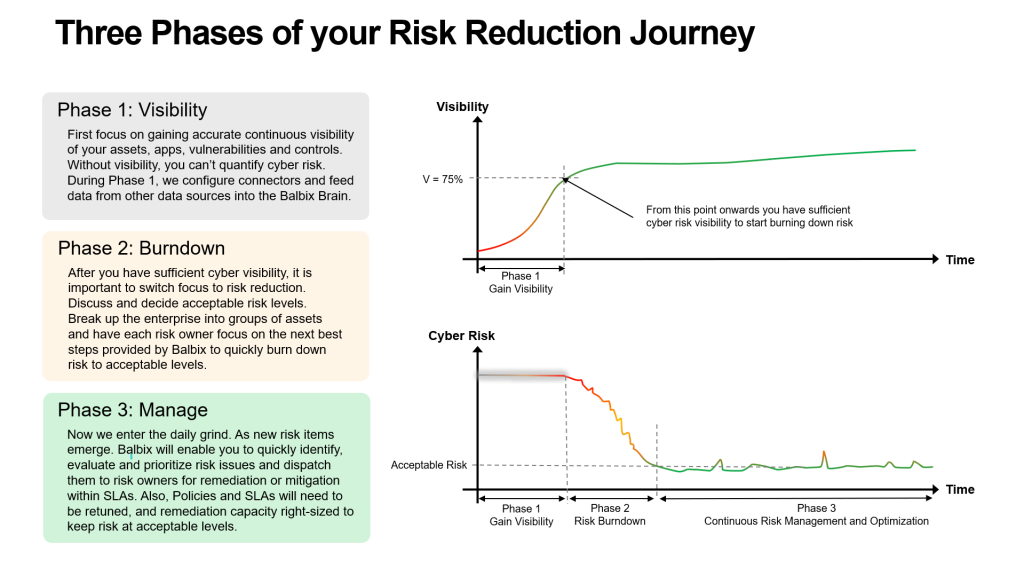
It sounds deceptively simple. But, as both Gaurav and Vinay reminded us, the devil is in the execution.
Everyone wants 100% telemetry. But as Vinay pointed out, that’s a mirage:
“Chasing 100% telemetry is like chasing the horizon. Don’t do that. What matters is knowing where your data is strong, where it’s weak, and making confident decisions from there.”
— Vinay Sridhara
Instead, teams should aim for 80–90% confident telemetry. The key is to organize findings by domain (apps, users, assets), attack the low-coverage areas first, and accept that visibility is never finished, and it’s continuous.
Visibility on its own doesn’t win board approval. What wins? Backlog evaporation.
Burndown means compressing your attack surface into a state where risk is measurable and manageable. That requires prioritization at the vulnerability instance level. A Log4j on an external-facing server isn’t the same as Log4j on a quarantined dev machine.
This shift is game-changing: in most enterprises, only 1–2% of exposures actually require urgent remediation. By focusing on that narrow band, powered by automation, security teams can set aggressive SLAs (like resolving critical exposures within two days) without chasing impossible goals.
The webinar also explored how to operationalize CTEM across uneven environments. Most organizations don’t start with uniform visibility everywhere. That’s normal.
Balbix recommends running three scopes in parallel:
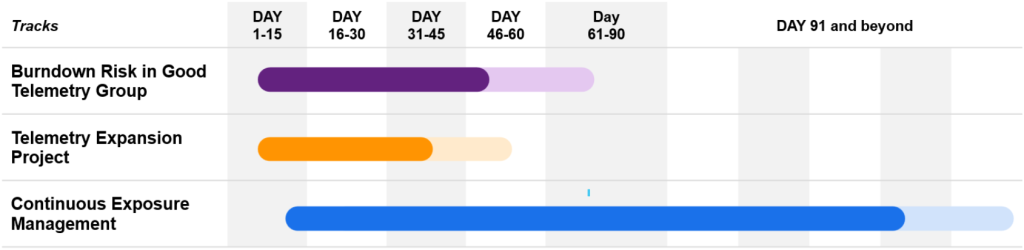
This parallel approach avoids the “boiling the ocean” trap and keeps momentum high.
At some point, the boardroom question always comes: “What does this mean in dollars?”
That’s where CRQ closes the loop. By defining risk scenarios—who might attack, how, what they’d target, and what it would cost—security leaders can connect technical exposure data directly to financial risk.
“Your CTEM journey is really your risk-reduction journey, and the goal is to keep risk at the right level. EM tells you what to fix, CRQ proves why it matters in business terms.”
— Gaurav Banga
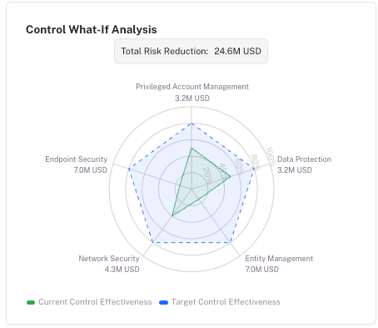
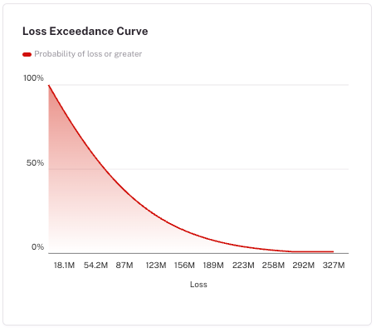
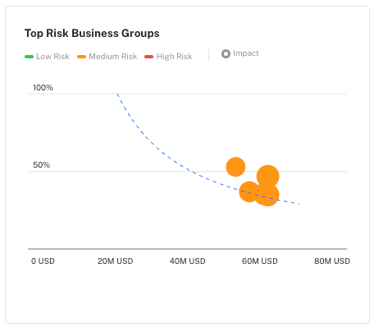
With CRQ integrated, every next-best action carries two metrics: an exposure score and a dollar value of risk reduced. That’s the kind of language executives understand.
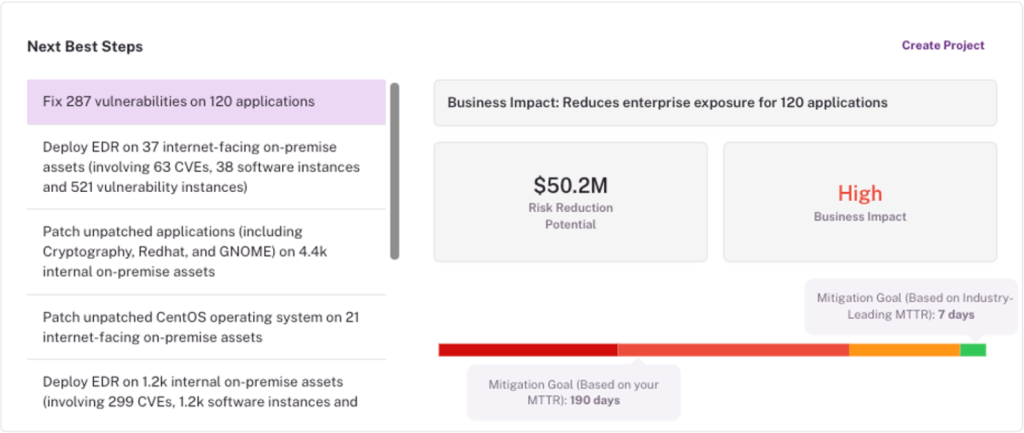
The webinar takeaway was clear: CTEM without EM is vague. CTEM without CRQ is unconvincing. Together, they make cyber risk programs actionable, defensible, and financially aligned.
It’s not about dashboards filled with vulnerabilities. It’s about:
That’s how you move from exposure to impact, and change the conversation with executives from “How many findings?” to “How much risk did we reduce?”
Want the full discussion? Listen to the webinar recording here: Watch the Recording