
November 13, 2023
Every security team recognizes that endpoint security tools/controls, such as Endpoint Detection and Response (EDR), e.g., CrowdStrike, SentinelOne, and Trend Micro, are critical for security and compliance.
But, not all endpoints are protected by an EDR tool. The gaps in coverage occur for many reasons, such as unmanaged devices, misconfigured endpoints, etc. Additionally, some end users may uninstall the EDR tool.
So, how do IT/security teams identify which endpoints do not have agents running on them? Usually, this requires a lot of data collection, correlation, and reporting. Relying on a Configuration Management Database (CMDB) alone doesn’t work because most CMDBs have partial visibility into endpoints in an IT environment.
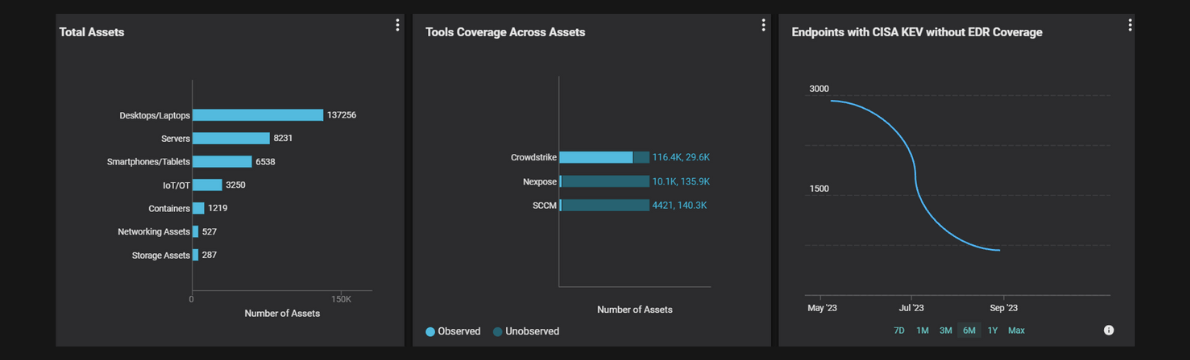
Balbix provides security teams comprehensive visibility into all their assets, including endpoints, mobile devices, and cloud, network, and IoT across their entire environment.
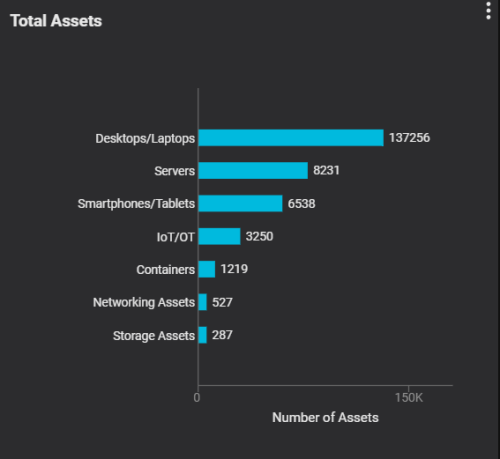
In addition, Balbix can detect endpoint security control coverage. For example, in this case, security teams can assess the coverage of Nexpose and CrowdStrike on all of their endpoints. They can further analyze endpoints with coverage and those without. This insight enables security teams to initiate programs to ensure they deploy security agents on all endpoints and address any gaps in security coverage. All of this data is available in real time on their dashboards.
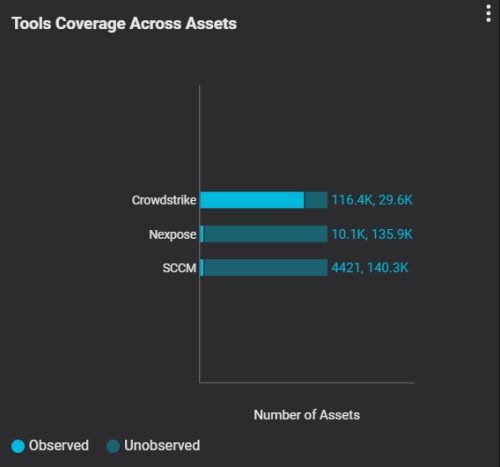
In large organizations with millions of endpoints, it can be challenging to determine which endpoints to prioritize. Security teams can create a widget that lists mission-critical endpoints with known open vulnerabilities, such as those identified in CISA KEV. This insight enables security teams to focus their security programs and resources on endpoints that pose the most significant risk to the organization and ensure an agent is deployed.
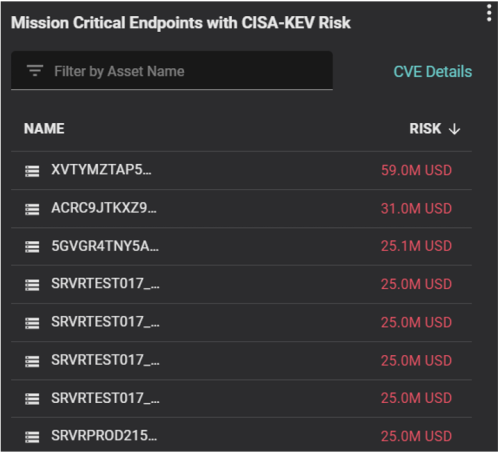
Additionally, for executive risk management and reporting, operators can show trends/changes in the number of mission-critical endpoints without an agent over time.
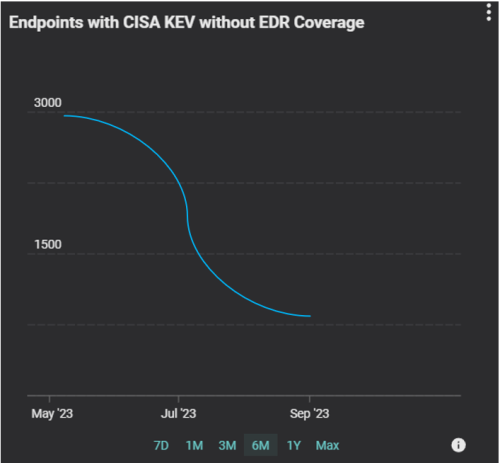
With these widgets and dashboards, security teams can significantly reduce the time and effort required for data collection and assessment of security control coverage. Over time, it helps improve compliance coverage and utilization, reducing cyber risk.