November 28, 2022
In the United States, we are well into our fall and winter holidays. Many people started decorating for Halloween in September and Thanksgiving in October. In November we are ensconced in Christmas decorations, commercials and shopping specials. Last week we had Black Friday, a day for in-store bargain hunting. And now, here we are at Cyber Monday, a day where we are encouraged to shop online. We’re busy!
What does all of this holiday activity have to do with cybersecurity? Well, it occurs to me that a parallel can be drawn between this holiday season and cybersecurity. Namely, we can get caught up in bustle and forget to focus on our larger purpose. With regards to cybersecurity, that may mean that we lose sight of our organization’s mission and the risks to its mission. We can get caught up looking at the (Christmas) trees and miss seeing the forest.
How often are we, in the security industry, told from all kinds of government, commercial and other well-meaning sources to follow advice like:
“Patch every vulnerability with a CVSS score of 9 or greater in less than 5 days.”
“Ensure your applications are configured to be resilient against the propagation of malware and ransomware.”
“Practice defense in depth.”
“The human factor is the weakest link in the cybersecurity chain, make sure that staff are trained and aware of the best practices of cybersecurity.”
Are any of these bad or wrong statements? Absolutely not. However, just like Black Friday and Cyber Monday where the commercial focus can take away our attention from family and friends, these tactical cybersecurity issues can distract us from the big picture and our role as cybersecurity professionals. The answer I believe is to instead focus on the risks to the organization’s core mission, or what we might call the business risk. Let your organization’s mission take the driver’s seat when you approach the task of prioritizing your IT risk management efforts.
Yes, I say business risk rather than IT technical risk should be the starting point for the cybersecurity professional because, with the exception of a very small minority of organizations, it is more than likely that the organization you work for does not make money by being secure. For example:
The point here is that we should focus on the business risk that would prevent our organization from engaging in the primary functions for which it exists. Cybersecurity organizations exist to support, enhance and protect the organization from IT risks that would negatively impact these primary business functions.
So, how do we go about achieving this goal? The answer is to start with business risk and translate this into cybersecurity risk. How many times have you received a security report that stated you have hundreds of thousands of critical and high CVSS scored vulnerabilities? Or that half of the 2000 assets that run protocols over SSL have a self-signed certificate, or have one that supports old and vulnerable protocols? Or, that your security architecture is deficient because it is not multi-zoned and protected in depth?
All of these things may be true, but what they don’t tell you is which items to start addressing to reduce the risk to the business fastest. Arbitrarily working through a list of items puts the cart before the horse as the old saying goes.
Instead, we must learn to start with the business risk then move to the technical risk.
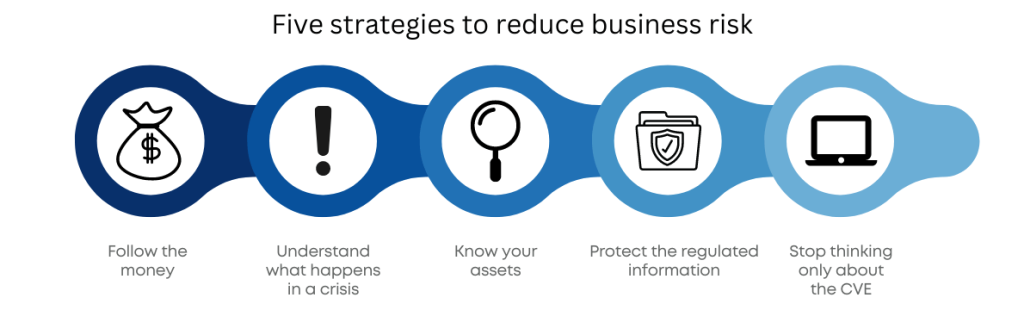
Here are five ways to focus on the most impactful areas for risk reduction:
Understand which of your organization’s business units are driving your financial goals.
By looking at these resources, you will quickly understand which parts of your organization are most critical to meeting its financial goals. Focus on these areas first.
Obtain a copy of any business impact assessment (BIA) or business continuity planning / disaster recovery (BCP/DR) plans. These documents will point you to the business functions that are most critical for the organization to meet its core objectives. Combine this knowledge with following the money and you will have a great map for prioritizing your risk reduction efforts.
Inventory your assets including traditional devices (servers, laptops), IoT/OT systems and cloud assets. Asset management lists can be obtained in many different ways and Balbix certainly has an outstanding means of interrogating your environment to help in this task.
Once you have this raw list of assets it is imperative to map them to the business units identified when following the money and understanding what happens in a crisis. Grouping your assets will allow you to determine which assets to remediate in which order (e.g. in order of which assets belong to the primary business driving units).
Throughout the years, many efforts at the legislative level have been passed with the well-meaning intention of improving data management and security. Regulations such as SOX, PCI, GLBA, CA SB-237, GDPR and the EU Cybersecurity Act, just to name a few, are some of the many pieces of legislation that have been passed.
I would argue that what they have been most successful at is raising the awareness of the need to keep IT environments secure rather than actually creating more secure environments. However, one area where these regulations have really shined, is in forcing organizations to identify what data is critical and where it resides. These regulations cover information such as financial records and personally identifiable information (PII), to name two of the biggest categories.
By identifying the data of your organization covered by these regulations you will be pointed to some of the most critical information systems (and the underlying assets) that your organization maintains. You can then tag these assets and group them as critical systems to be used as prioritization for remediation efforts.
In the early days of cybersecurity we focused on specific instances of vulnerabilities that had the potential to be particularly impactful if exploited. However, that led us to long reports of CVEs that were near impossible to prioritize for remediation efforts. Furthermore, it was near impossible to understand if you were truly making an impact on organizational risk. In other words, we were left asking, ‘what am I doing to make our system more reliable and secure for my company to succeed?’.
Rather than focus on the CVE, focus first on the collective cyber risk of the assets in the most business critical organizations. Then, when creating remediation strategies, focus on the asset as a whole rather than addressing CVE instances. In this way, the systems that are driving your critical business mission will be secure, and your business risk will be reduced.
Focusing in the reverse, on the CVE, may result in all high and critical severity vulnerabilities being remediated and leave behind seemingly innocuous medium and low severity vulnerabilities. However, based on the configuration of your environment it may leave critical assets open to being exploited by the remaining vulnerabilities even though those vulnerabilities had low severity ratings.
If you can address these five areas you will be well on your way to managing your IT environment in a business risk aligned manner that not only provides the highest impact for the least amount of effort but also drives a more secure environment for your business to thrive.
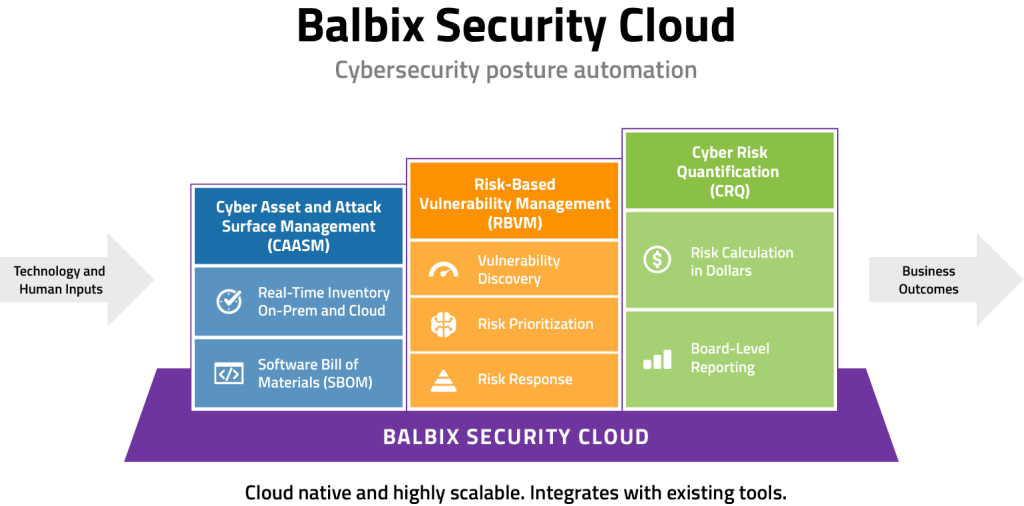
I would be remiss of course if I did not mention the many capabilities that Balbix has to enable you to take a business-focused approach to IT security risk management. Our SaaS platform, the Balbix Security Cloud, uses AI and automation to consolidate all your security data and turn it into the intelligence and actions you need to reduce risk, improve security team productivity and gain the confidence of your board and senior leaders.
While Bablix hosts a vast array of capabilities, here are three features that are specifically relevant to the context of this article.
With Balbix, you can accurately inventory your on-prem, hybrid and cloud assets either through ingestion of third party CMDB data sources, or via the native Balbix sensors, or a combination of both. In all cases, you get a very clear picture of the cyber resources in your environment. And, as we know, “knowing is half the battle”.
Balbix has the capability to identify many types of systems automatically, from domain controllers, to exchange servers and many many more. This automatic identification cuts the time to find important assets dramatically. Add to this the powerful set of filters that can be applied as a group definition and you have the ability to group your assets in a nearly limitless array of possibilities. For example, every asset ingested that has a tag of “SOX” will be automatically put into a “compliance” group, thus automating the grouping of assets based on business prioritization.
The ability to identify in monetary terms where your biggest risk lies is indeed one of the most powerful features of Balbix. Balbix starts calculating risk by automatically identifying and correlating risk-based vulnerability information (CVE’s, misconfigurations, credential vulnerabilities, etc.) for every asset in your environment from all data sources available. Balbix then uses its AI/ML driven engine to calculate risk impact and likelihood. Balbix, in combination with inputs from your business risk analysis, then translates these inputs into monetary values to help drive concrete real world prioritization discussions and efforts.
In closing, while we rush headlong into busy days of celebration and rejoicing, I bid you to focus on your organization’s mission as you go about reducing risk.