

September 24, 2025
After nearly a decade of working with Fortune 500 CISOs, I’ve learned two universal truths:
The vulnerability backlog is like laundry. No matter how many loads you run, it just piles up again. And yet, boards keep asking the same question: “Are we safer today than yesterday?”
The mistake most teams make? Treating cyber risk like a linear project (Figure 1). First get full visibility into the enterprise environment. After this start working on the backlog. Then build continuous response.
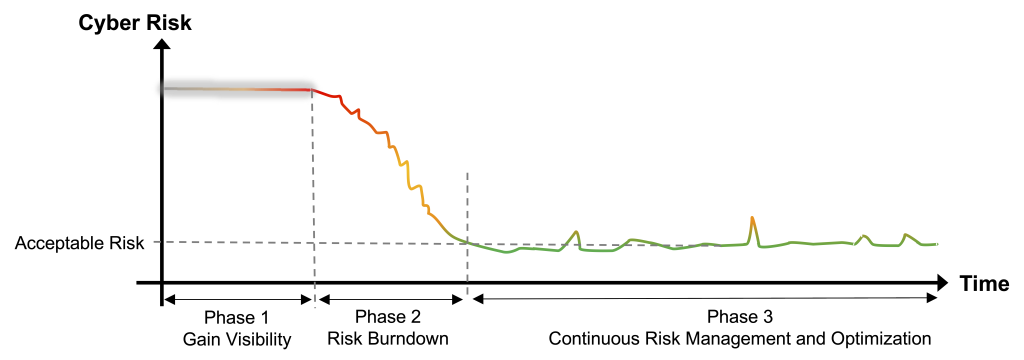
That’s like saying, “I’ll start exercising once I’ve perfected my diet and meditation routine.” You’ll be waiting forever.
In practice, cyber risk reduction doesn’t work in sequence. It’s a parallel processing problem. The most effective CISOs run three tracks at the same time (Figure 2).
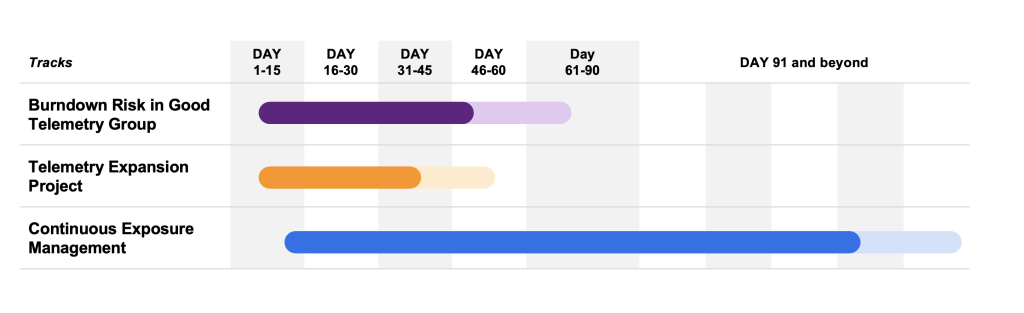
Every enterprise has some assets with decent visibility — ownership mapped, vulnerability data available, and key controls in place.
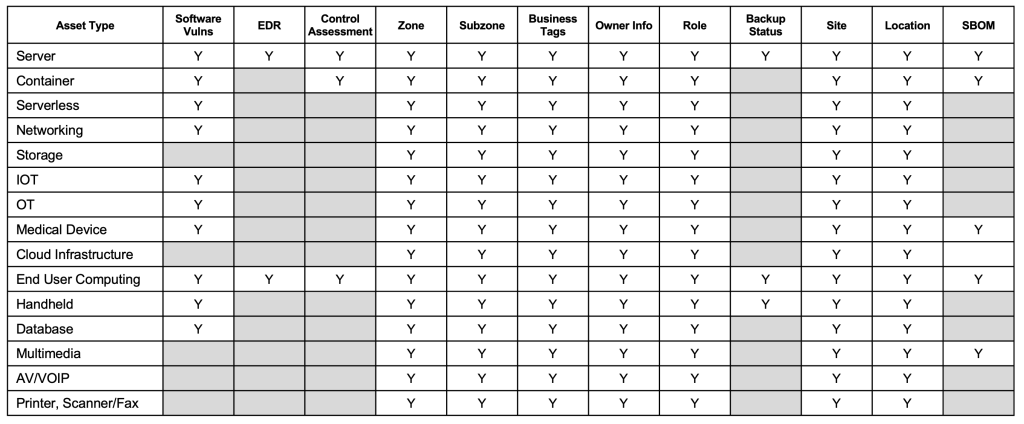
But here’s the rub: most organizations don’t actually know which assets those are. Understanding and measuring telemetry is hard. In fact, we’ve seen enterprises spend months arguing over what “good visibility” even means. This is confounded by the fact that “expected signals” for a given asset type (assuming that itself is known) varies quite a bit, as shown in Figure 3.
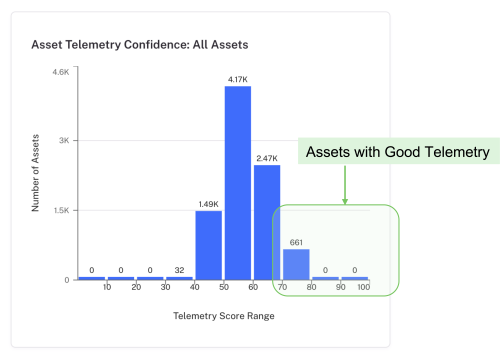
With Balbix, this problem goes away quickly. After just 2–3 days in a proof of concept, it becomes clear which assets have “good enough telemetry” to start burndown.
Once the group is defined, Balbix prioritization ensures you’re not just chasing CVSS scores — you’re fixing what’s exploitable, business-critical, and high risk.
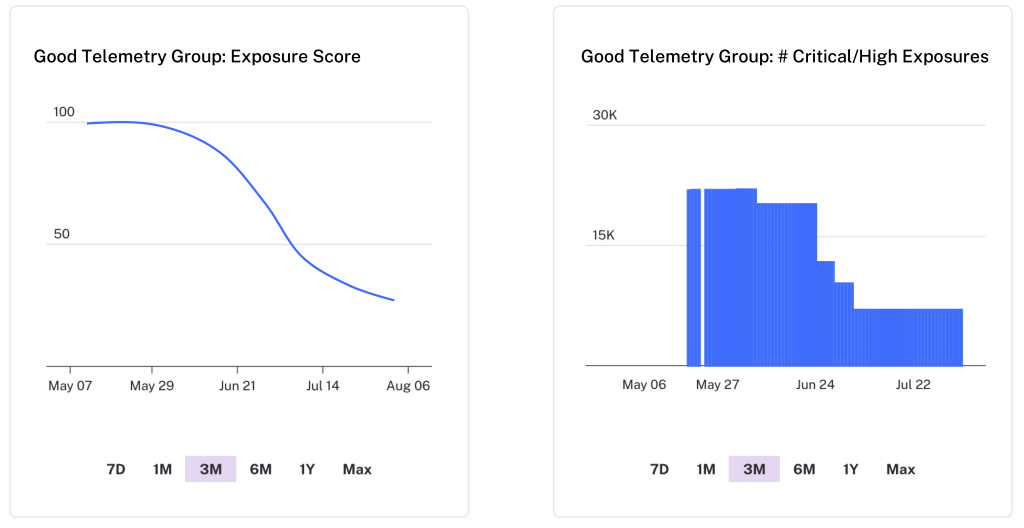
In the first 30–90 days, leading teams show:
It’s the kind of early progress that boards actually notice.
While the burndown is running, top programs launch enrichment sprints to improve visibility across the rest of the environment.
As we saw in Figure 3, different asset types need different signals to accurately calculate exposure and cyber risk:
Similarly, applications also have their own set of telemetry dimensions that influence visibility and prioritization. These include:
The backlog of telemetry gaps can feel overwhelming — where do you even start? Balbix helps by showing exactly which signals matter most for risk reduction, and which can wait. This way, enrichment projects are focused, time-bound, and achievable.
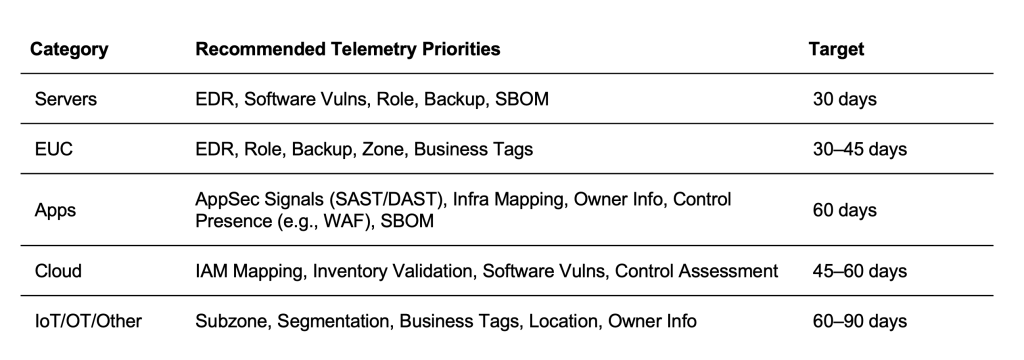
In 60–90 days, we’ve seen telemetry scores jump 30%+, with ownership mapped for the riskiest apps — dramatically expanding the universe of assets eligible for Track 1 burndown.
This is the long-term operating model. Instead of firefighting each new CVE, successful teams build a continuous loop:
Of course, keeping this loop running without burning out your team requires automation. That’s where Balbix shines. Exposures are prioritized using exploitability and business impact, tickets are automatically created and routed to the right owner, and SLAs are enforced without manual chasing.
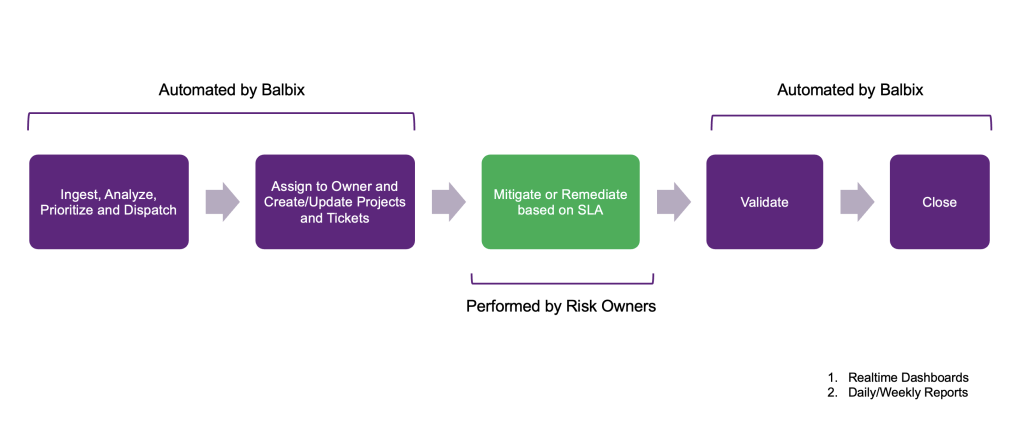
The best programs measure relentlessly:
It’s how you turn vulnerability chaos into a predictable, SLA-driven process.
If you focus on this playbook, Tracks 1 and 2 will eventually come to an end. Once you’ve burned down the initial backlog and expanded telemetry across the enterprise, Track 3 becomes the only track left.
At that point, you’ve built a world-class cybersecurity program — the kind of discipline and operational maturity that puts you in the top 2% of enterprises.
Each track plays a role:
Balbix helps you run all three at once — by surfacing the “good telemetry” group in days, guiding enrichment efforts where they matter most, and automating continuous response at scale.
Run them in sequence, and you’ll always be behind. Run them in parallel, and you actually get ahead.
Cyber risk isn’t about clearing a backlog. It’s about running three tracks in parallel — building credibility, expanding coverage, and staying resilient all at once.
If your strategy is still running in sequence, that’s exactly what you’re doing.
It’s time to break the cycle.