February 12, 2021
Picture this.
You walk into the kitchen. On the counter, is a beautiful charcoal gray plate. And right in the center of the plate is a perfectly round cookie. You are tempted, of course. You reach for the cookie, take a bite, and close your eyes in anticipation of a sweet, sinful burst of flavor, but instead, you get a mouthful of …red peppers and artichokes. Whaaaat?!!
This is what most organizations’ cybersecurity posture looks like. A warm, delectable cookie from the outside, but you, the security leader, know that there is something amiss.
This is why you spend sleepless nights, worrying about unseen risks and vulnerabilities. You worry about not having an accurate asset inventory. You worry that your team is not working on issues that matter the most. And you worry about how you can involve everyone in the company, especially the risk owners, to do their part.
Now, you can spend the rest of 2021 doing pretty much what you did last year with, get lots of vendor briefings, buy some tools, get new dashboards, and hire more analysts. You can continue to have a discussion each quarter with your board about why the company’s cybersecurity posture may seem like a warm, delectable cookie, but in fact, it isn’t, and you are trying to make things better with your 65+ tools and still falling short.
Or, you can try something radical.
While you cannot miraculously transform a red pepper and artichoke cookie into a white-chocolate macadamia nut delicacy, you CAN really focus on automating your cybersecurity posture.
Here’s what you need to do:
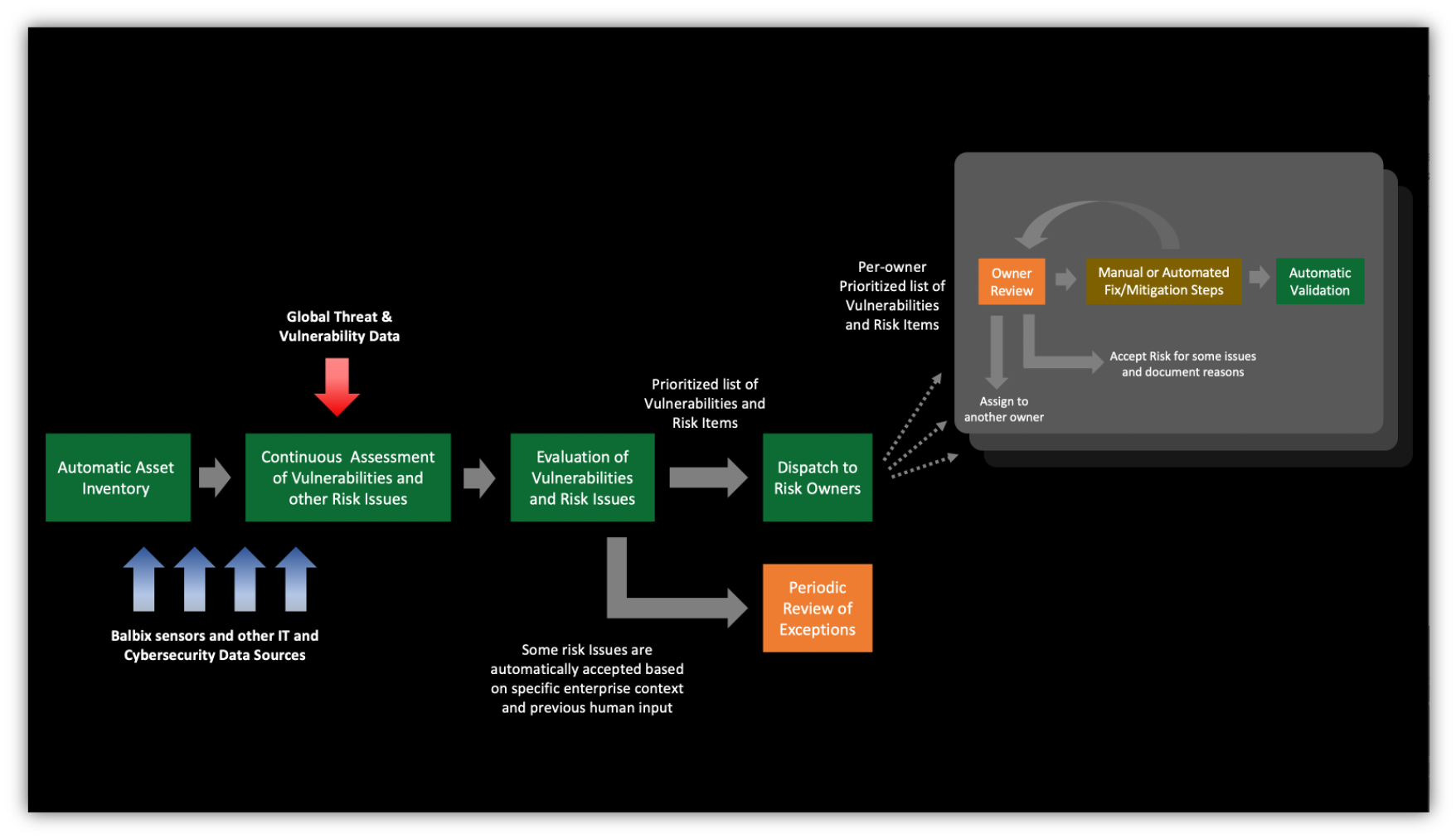
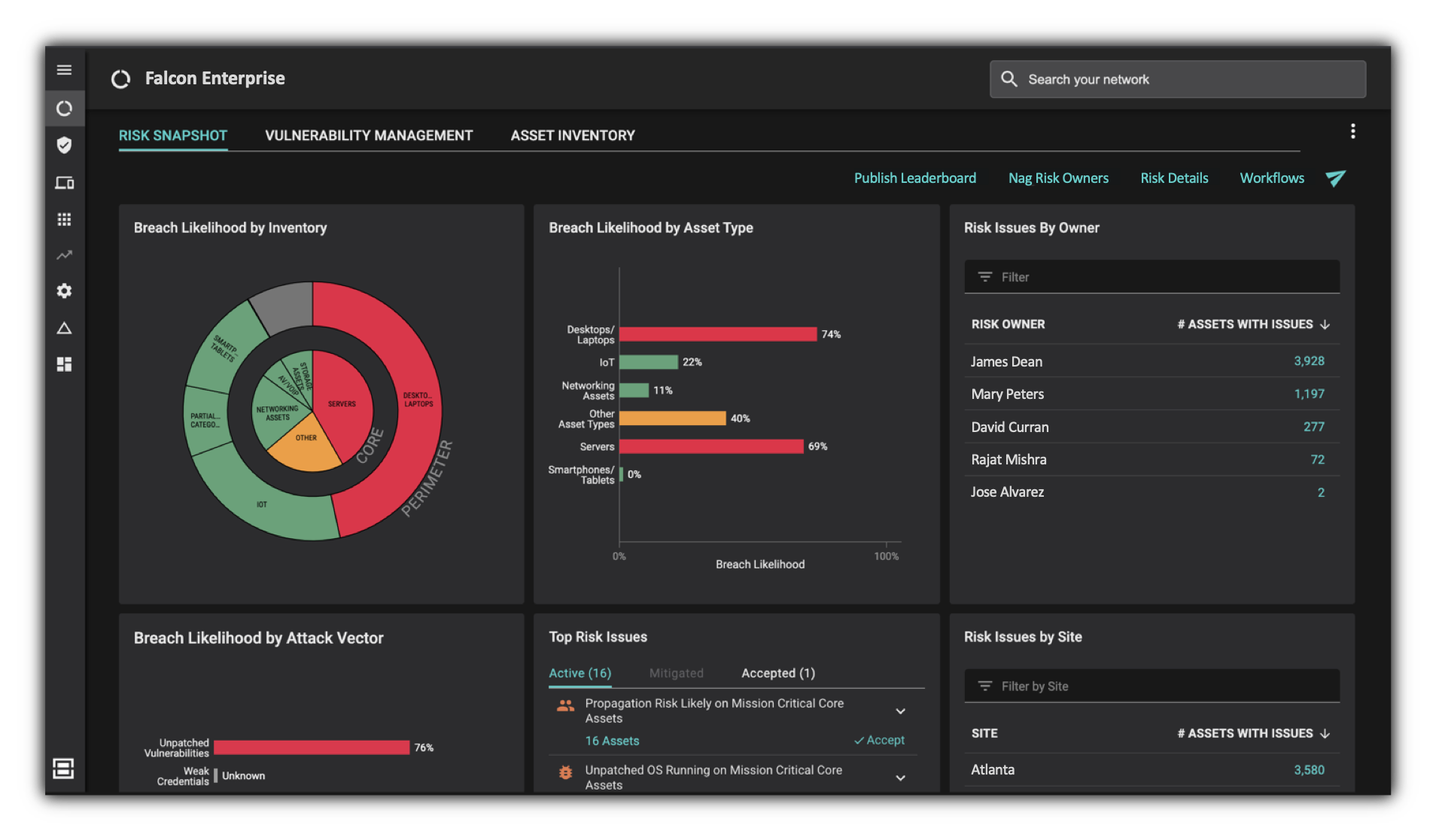
You can’t improve what you cannot measure, so this project is also about gaining 100x cybersecurity posture visibility. Ditching that stethoscope for a CT scanner to find those needles is key to staying ahead of attackers.
Yes – all this can be done! We have helped organizations ranging from startups to a Fortune 10 organization to get this working (and no, it does not take 18 months). Get started here.