

November 2, 2021
Your organization is likely moving to the cloud. By now you know that moving to the cloud is not like flipping a light switch: one day you’re on-premises, the next you are in the cloud. It’s a gradual process. Today every large organization has a mix of on-premises and cloud environments. There are lots of benefits from maintaining a hybrid cloud environment. A key one is being able to choose the right location for a given asset, and being able to navigate the tradeoffs between cost, governance, agility, location etc. Simplifying security is not one of them.
This blog is about the journey to mature your security posture to catch up to your hybrid cloud. Today, for most organizations, visibility is siloed. Security context is scattered across multiple IT tools, particularly as dynamic workloads rapidly migrate to and from the cloud. Likewise, proactive cybersecurity tools are typically split into on-premises and cloud silos. This makes it very difficult to get a consolidated view into both environments. As a result, prioritization, reporting on, and fixing the most pressing risks to the business across environments is challenging. The result is an increasingly dynamic and fragmented cybersecurity posture that strains infosec teams tasked with rapidly identifying and resolving cyber-risks to cloud apps and infrastructure.
Most security teams began their journey on-premises. Typically, they started by scanning for unpatched software. They subsequently added additional capabilities over time such as the ability to automatically prioritize those vulnerabilities for remediation. Many also added the ability to identify other areas of risk such as poor passwords, weak encryption, over-privileged admin and service accounts. They have then added security for their cloud environments.
AWS, Microsoft Azure, Google Cloud Platform (GCP) and other public cloud services operate using a shared responsibility model, which has meant that the cloud provider assumed responsibility for securing the underlying cloud infrastructure. Many companies then used the native security tools of the cloud vendor to deploy and manage their security posture for this environment. Some have taken it an extra step to deploy a cloud security posture management tool to add extra capabilities and to unify posture management across clouds. Few have unified posture management between their cloud and on-premises environments.
For those that have, they typically do so using a do-it-yourself (DIY) data cloud. Often, these security leaders have a long running cybersecurity data lake project where they stream the output of all their security tools into a central place to do analytics, trying to come up with a unified picture of overall cyber risk which will help stakeholders make better cybersecurity decisions. However, as we’ve previously outlined, building your own cloud cybersecurity data lake has many shortcomings including issues with visibility, measuring risk and remediation.
Balbix offers another approach – an approach that allows you to automate your hybrid cloud security posture.
With the newly announced Balbix Connector for AWS, Balbix customers can now extend their on-premises security to the cloud, and vise-versa. The ability to unite your security posture across a hybrid cloud environment eliminates the need for you to review multiple dashboards and allows you to work more productively. Automating that security posture with Balbix provides additional unique benefits:
First, Balbix will create a single inventory of assets that unites all the assets across your environment – in the cloud, on-premises and even IoT and OT systems. Second, Balbix will automatically sort those assets into predefined groups for example: by business unit, by asset type or geographical location. Image below shows asset groups by asset type and a list of assets that includes their site and asset type. For example, there is a group combining all servers, whether on-premises or in the cloud.
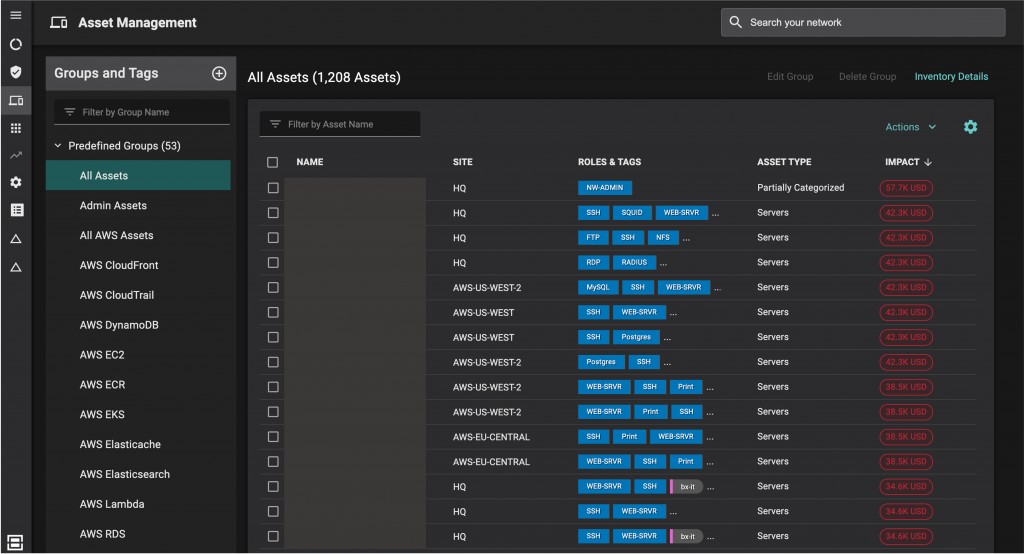
Balbix automatically detects exposure to over 100 attack vectors, notably: unpatched software vulnerabilities, weak credentials, missing or poor encryption, trust issues and cloud infrastructure misconfigurations. Having a unified security posture allows you to see them all in one place. It also allows you to see risks that you would have missed if your on-premises and cloud security remained siloed. Take shared passwords for example. With a unified view, you could see if someone was using the same password in both on-premises applications and in cloud applications. Similarly, you might not have noticed that an administrator was over provisioned with access to domains in the cloud and on-premises. Both the password and trust issue risk increase your organization’s susceptibility to lateral movement between the cloud and on-premises.
Managing alerts in separate applications is a complex affair. By contrast, it is easy to manage alerts for a hybrid cloud in one place with Balbix. To start, you reduce your risk of gaps and redundancies. Balbix also uses advanced analytics to categorize and prioritize risk issues. As image below illustrates, you can see your breach likelihood by location, attack vector and asset type across your hybrid cloud environment. You can also see issues by site and by owner, which increases owner accountability and improves accountability.
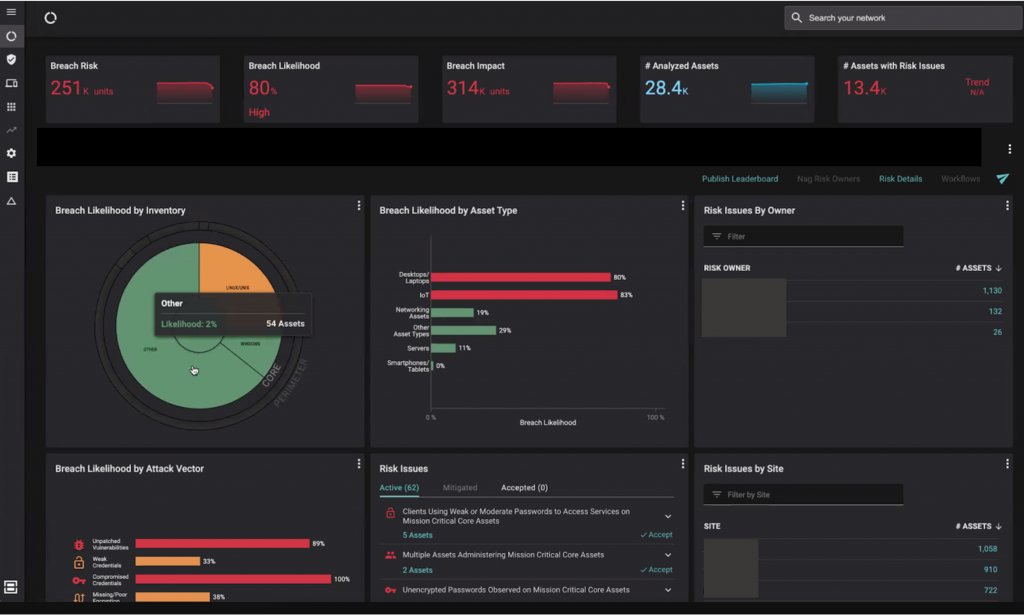
A common question from executives and the board of directors is ‘what is our cyber risk’ and ‘is it improving?’. In response, most security leaders respond with metrics around mean time to patch (MTTP) or the number of vulnerabilities that have been resolved. With Balbix, you can also report on the overall likelihood of a breach and breach risk (see Image 2). Risk is measured in dollars (or Pounds, Euros, Yen, etc.), which provides a common language that organizations can use to prioritize projects, spending and track the effectiveness of their overall cybersecurity program. Moreover, with Balbix you can break down your siloed approach and get a holistic view of your enterprise-wide cyber risk.
Of course, at the root of this integration is improved security posture for all parts of your environment including AWS. Read my recent blog about how Balbix and our new Connector for AWS improves your AWS security.