Your AI-Powered Cybersecurity Brain
Transform your cybersecurity posture with a data-driven understanding of your cyber risk. Drive a decrease in risk, easier compliance and lower costs

A Unified Platform for Cyber Risk Management
Comprehensive visibility
Gain a single unified and inspectable view of all your assets, users and applications with correlated and applicable vulnerabilities, threats, controls, business impact and compliance issues
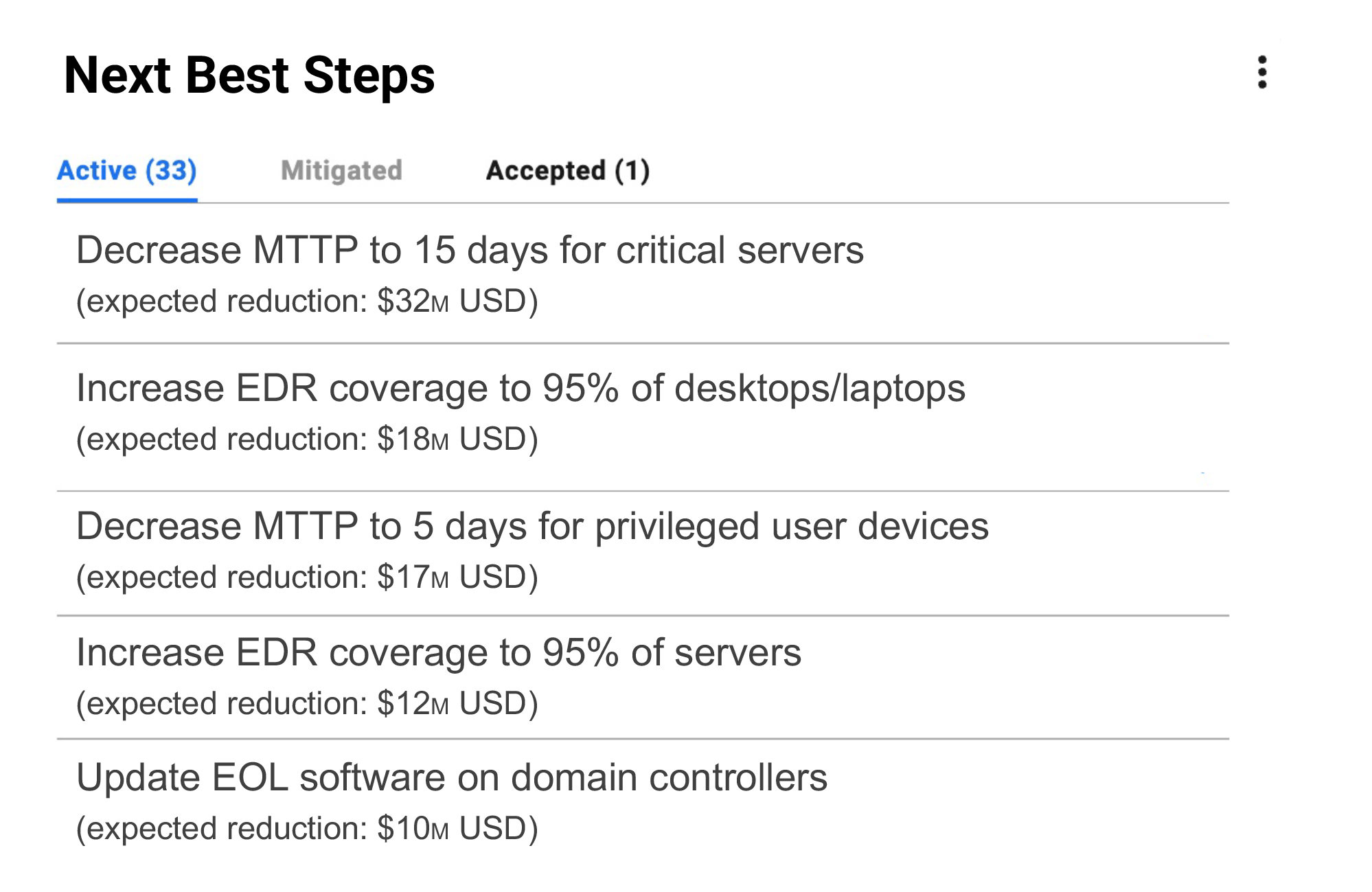
Actionability
Act on next best steps for risk reduction and compliance leveraging tactical and strategic insights to decrease your mean time to mitigate risk. Reduce residual risk to acceptable levels
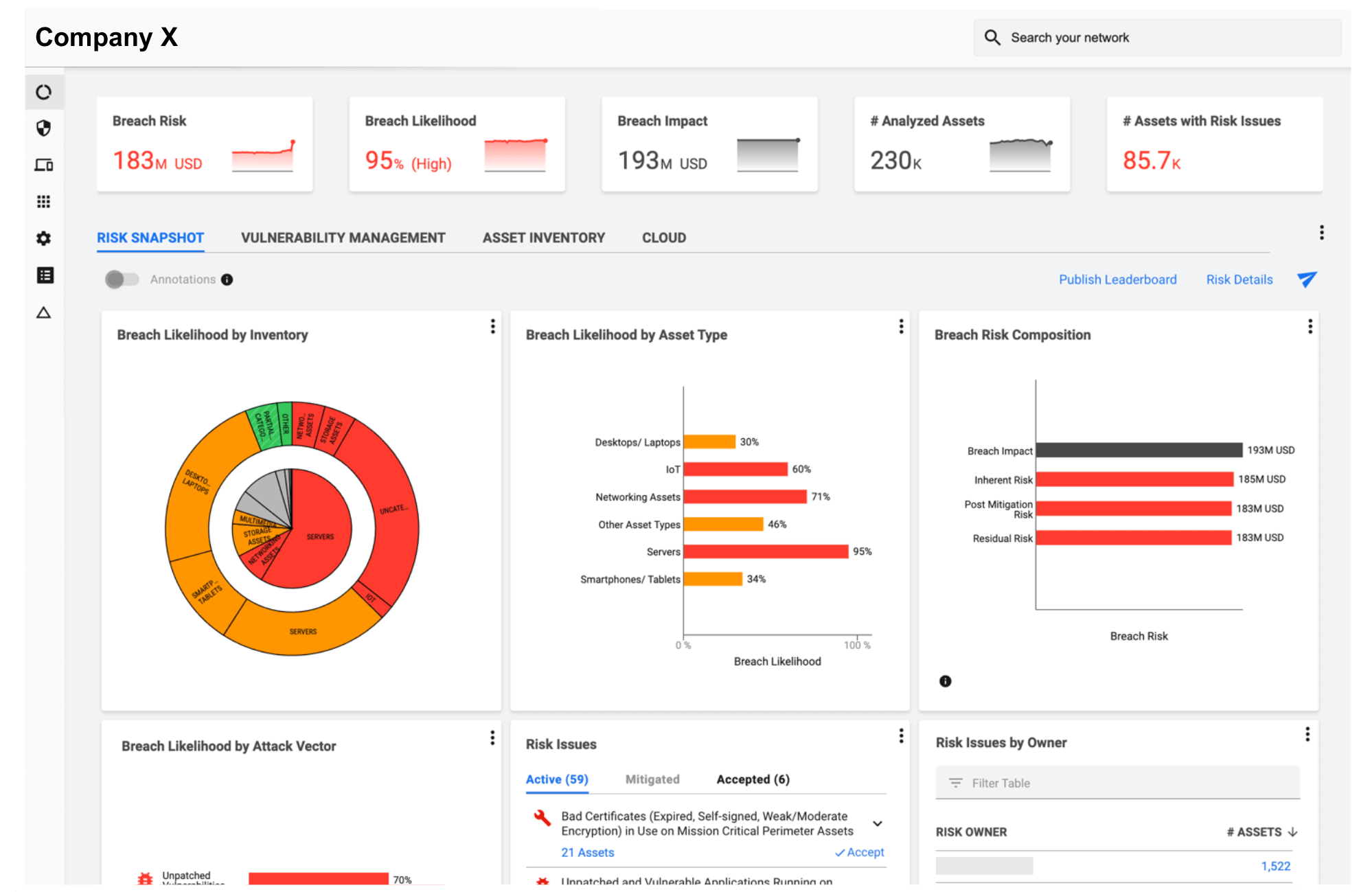
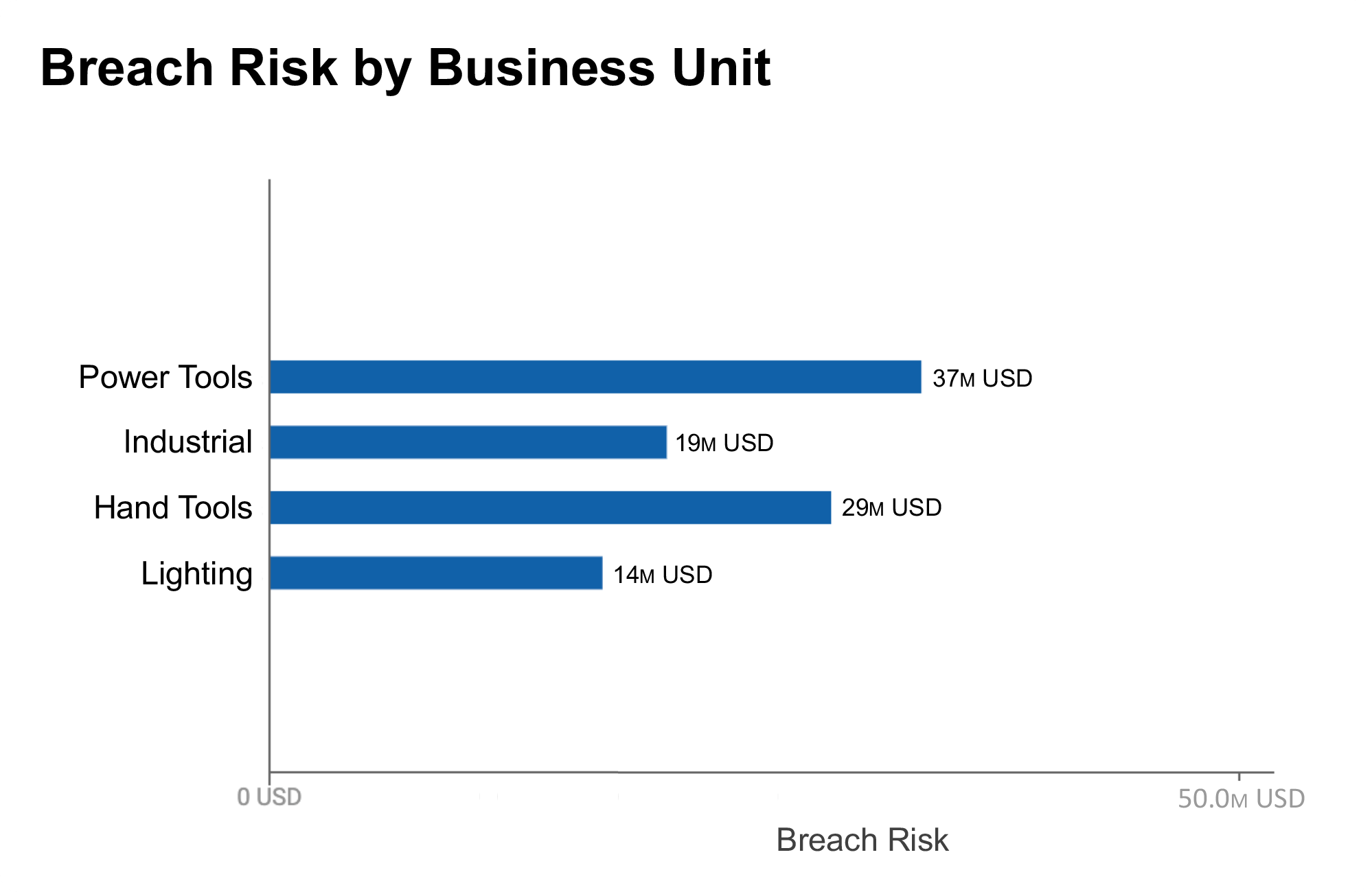
Map cyber risk to dollars
Increase understanding and engagement of cybersecurity issues in your senior leadership team, your board as well as risk owners across the organization by using the language of money
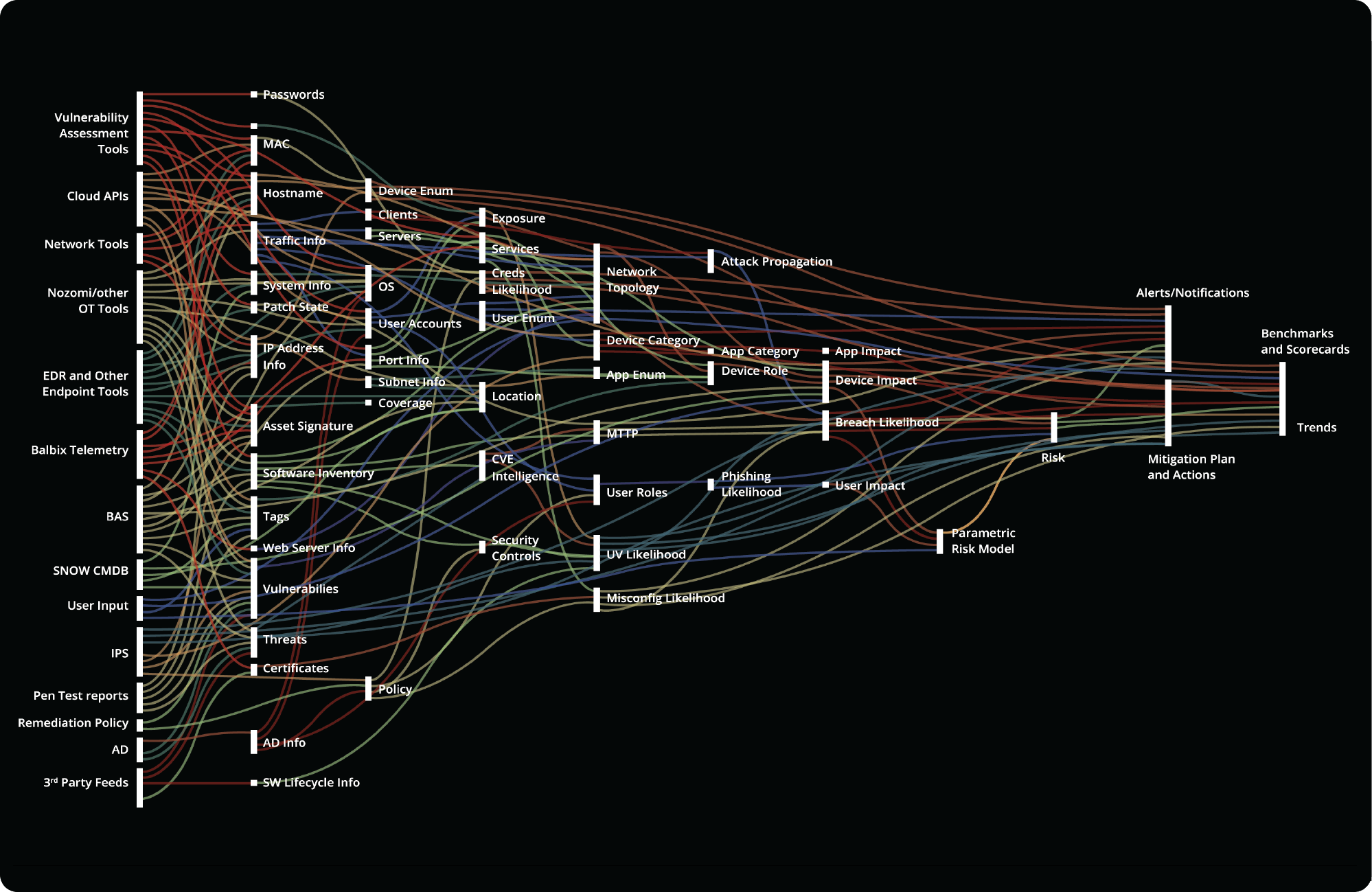
Innovative AI
First use AI to deduplicate, correlate and unify data from your siloed tools. Then convert AI-powered insights on the strengths and gaps in your cybersecurity posture into an effective strategy to manage your material cyber risks




Balbix is a Leader in Cyber Risk Management




Ready to See Balbix in Action?
Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.