Achieve Greater Visibility into Your Attack Surface
Build a robust vulnerability prioritization and deliver accurate risk and compliance reports
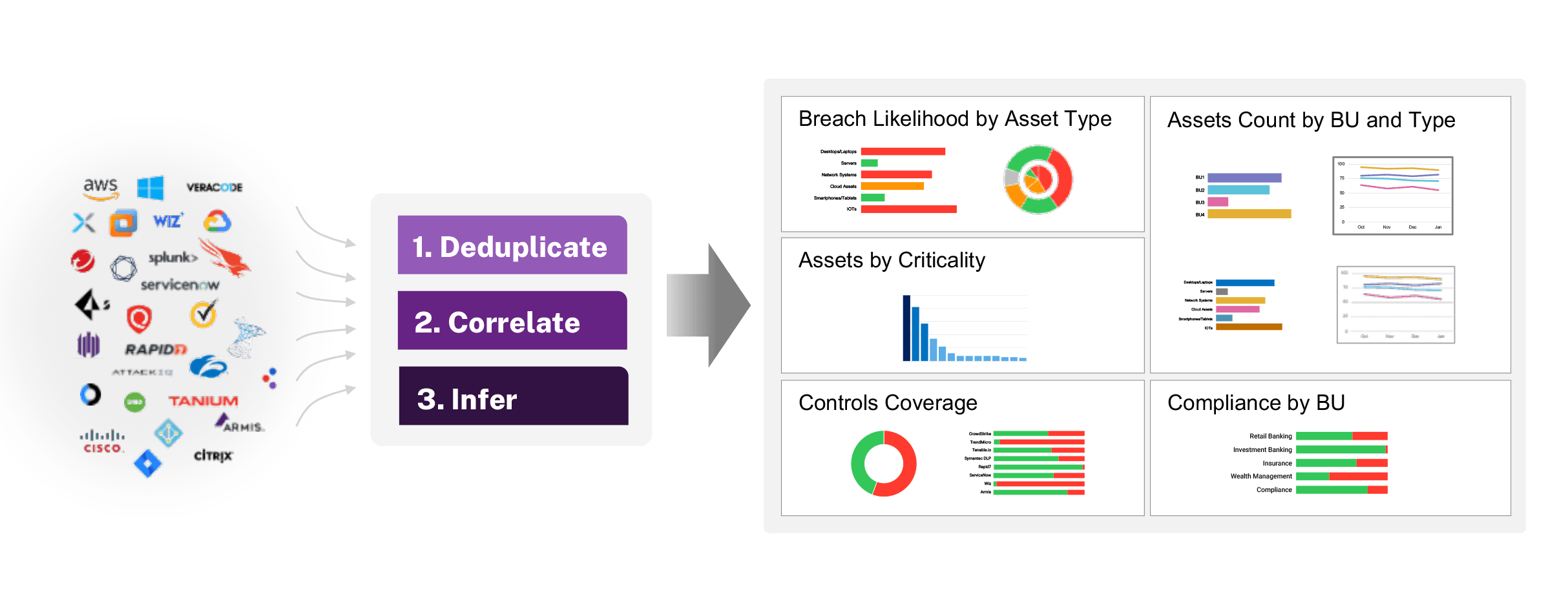
Uses AI and ML to consolidate, normalize, and deduplicate data gathered from hundreds of IT, security, business, and home-grown tools via APIs for comprehensive visibility
Automatically tag assets with business context to assess criticality, enabling materiality determination, vulnerability prioritization, and risk quantification
Consolidate vulnerabilities [CVEs and misconfigurations] and security controls [EDR, VM tools] with assets to understand security and tool gaps

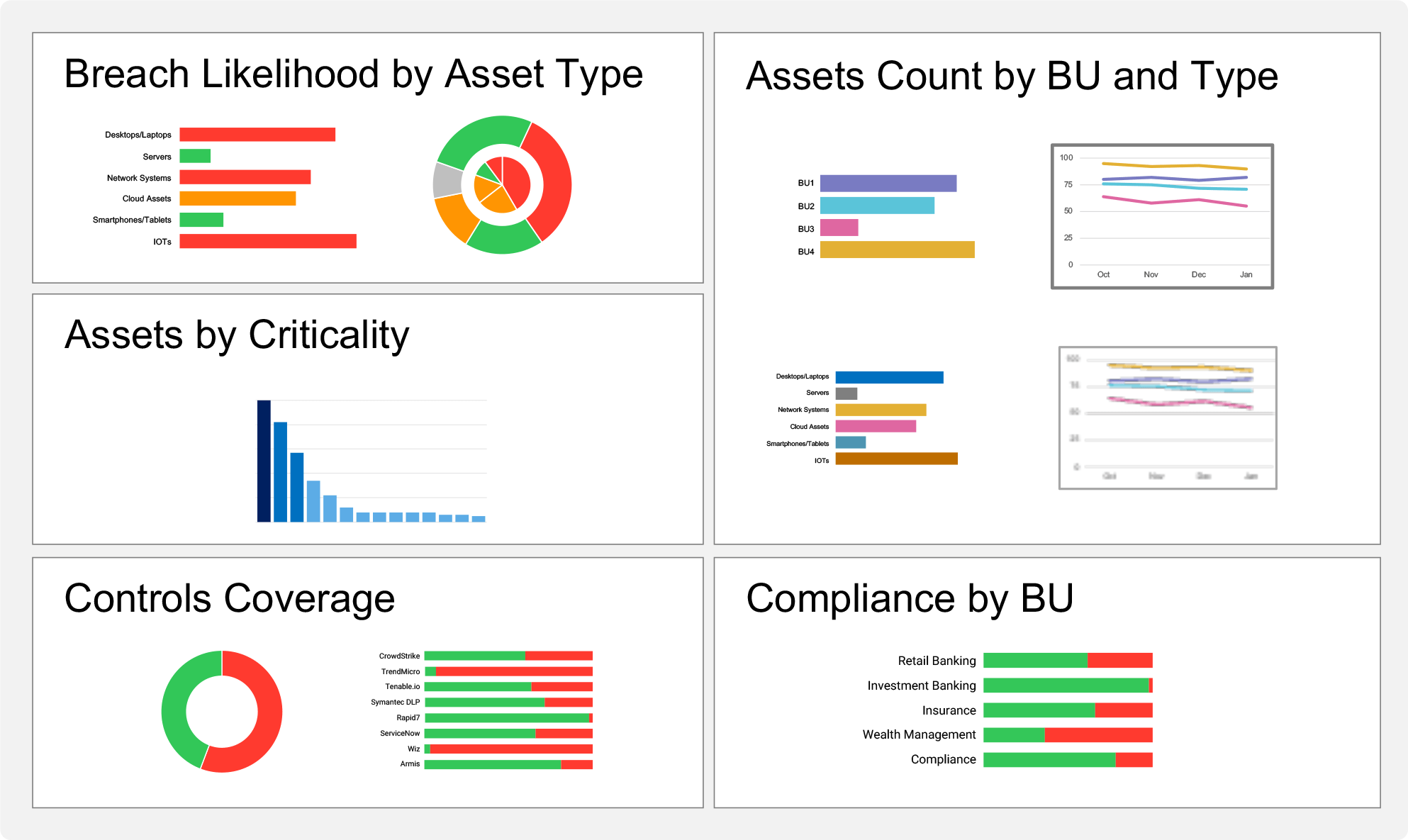
Slice and dice by business units, sites, owners, and more to operationalize IT and compliance reports on infrastructure and software assets, vulnerabilities, and security controls
Gain comprehensive visibility into assets, applications, vulnerabilities, controls, and threats to understand & appropriately prioritize risk reduction.
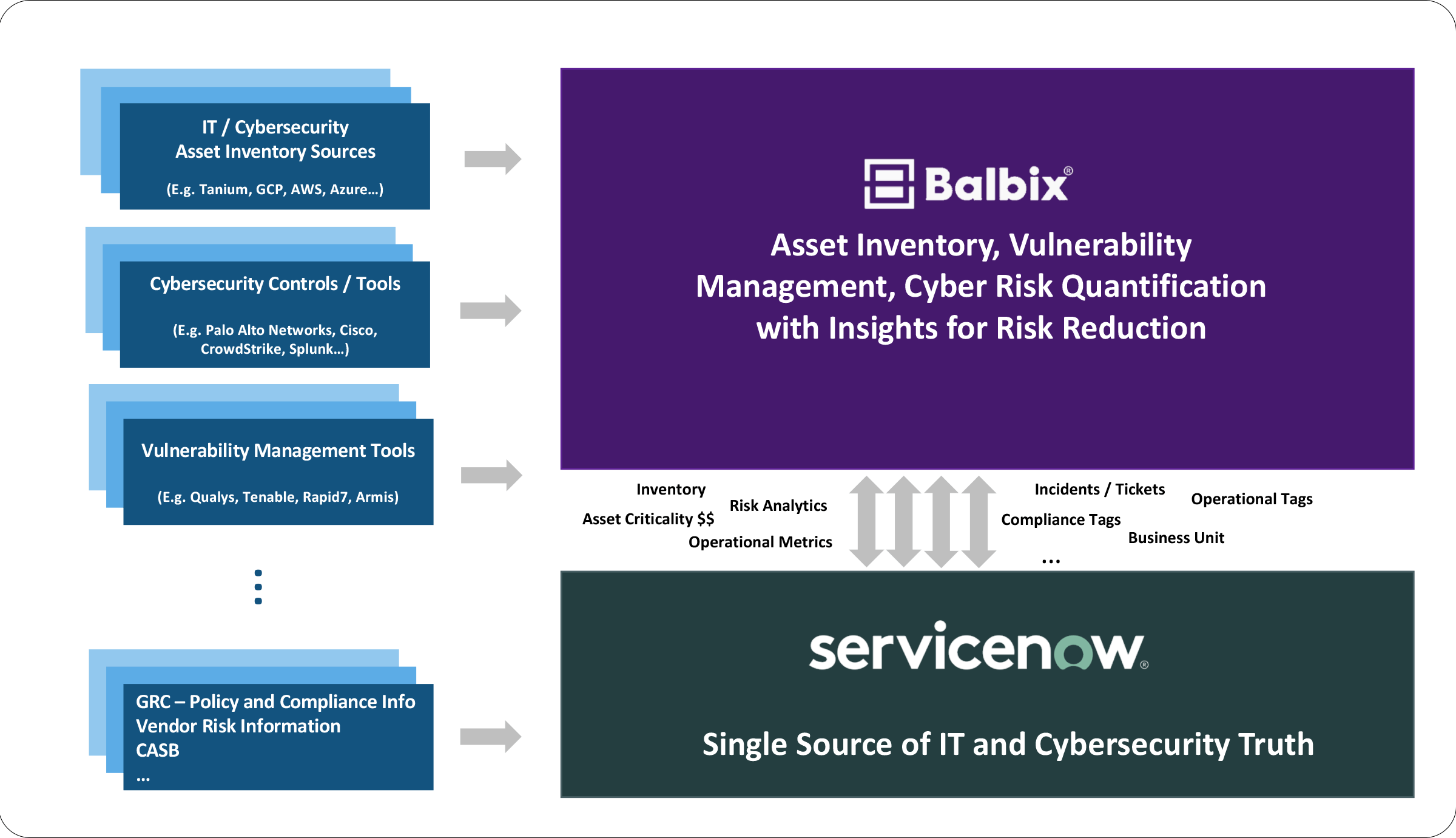
Improve the accuracy of your CMDB, such as ServiceNow, through automated updates of assets and attributes missed by your CMDB reconciliation process.
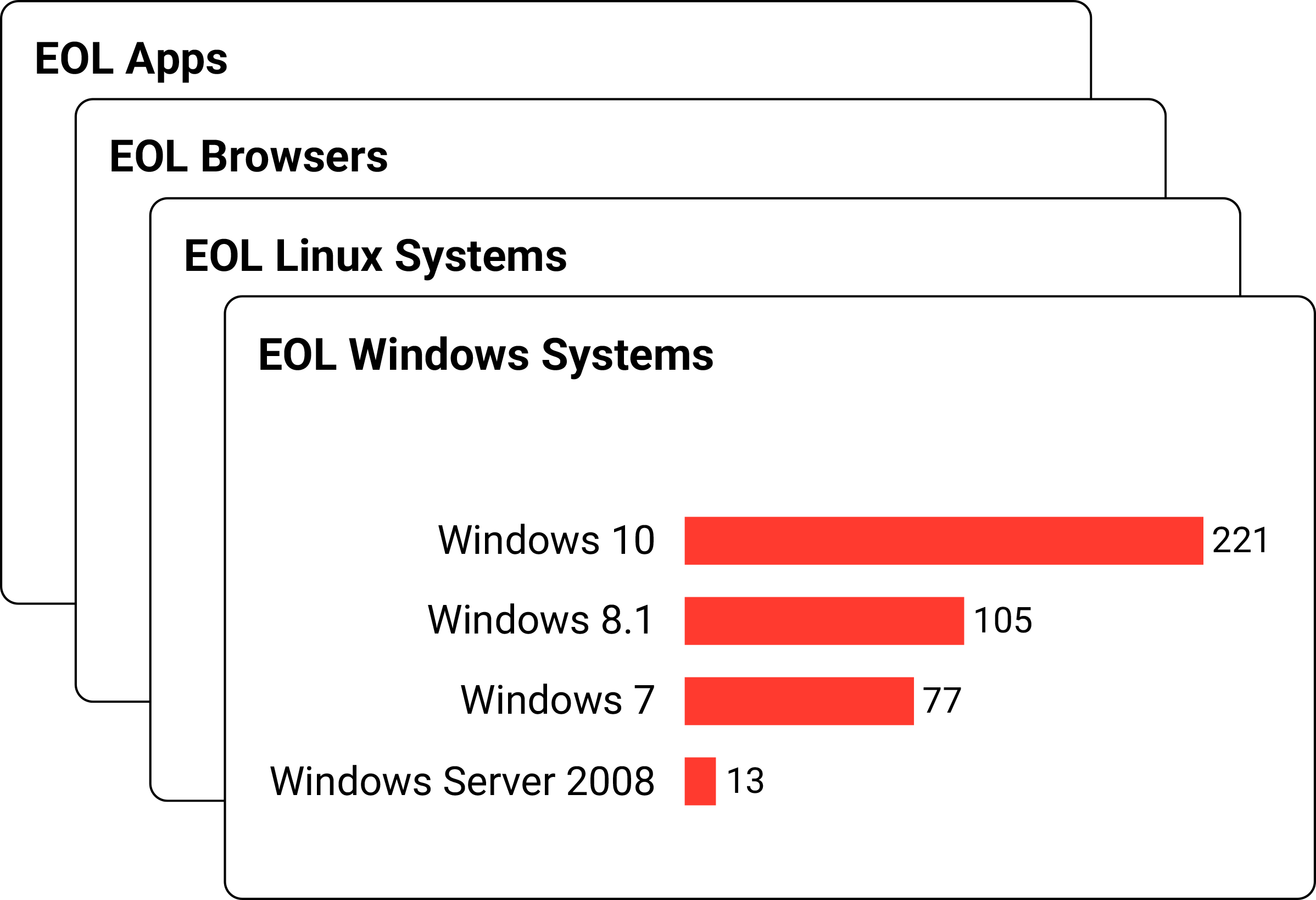
Generate audit and compliance reports about your risk posture – vulnerabilities, misconfigurations, End-of-Life (EOL) software, and more.



Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.